Effective risk management is crucial for organizational success. It’s not just about avoiding problems; it’s about proactively identifying, assessing, and responding to potential threats and opportunities. This guide explores a comprehensive framework for developing and implementing robust risk management strategies, covering everything from defining risk and identifying potential threats to monitoring and controlling risks over time. We will examine various methodologies and best practices to help organizations navigate uncertainty and achieve their objectives.
From understanding different risk types (financial, operational, strategic, reputational) and employing assessment techniques like SWOT analysis and risk checklists, to implementing response strategies such as avoidance, mitigation, and transfer, we will cover a broad spectrum of essential concepts. The role of technology in enhancing risk management, along with building a strong risk culture and effective communication, will also be examined through real-world examples and case studies.
Defining Risk and its Context
Risk management is a crucial process for any organization, regardless of size or industry. Understanding the nature of risk and its various forms is the foundational step towards developing and implementing effective strategies to mitigate potential negative impacts. This section will define risk and explore its different types, highlighting the key characteristics of successful risk management and illustrating how risk appetite varies across different sectors.
Risk, in its simplest form, is the potential for an undesirable outcome. It encompasses the possibility of losses, setbacks, or failures that could negatively affect an organization’s objectives. This potential is often quantified in terms of probability and impact, allowing for a more structured approach to management. The context of risk is equally important; a minor event for one organization might be catastrophic for another, depending on factors like resources, resilience, and the specific nature of their operations.
Types of Risk
Risks can be categorized in various ways, but four common types are financial, operational, strategic, and reputational risks. Understanding these distinctions allows for a more targeted and effective risk management approach.
- Financial Risk: This encompasses potential losses related to financial assets, liabilities, and transactions. Examples include credit risk (failure of borrowers to repay loans), market risk (fluctuations in market values of investments), and liquidity risk (inability to meet short-term obligations).
- Operational Risk: This involves disruptions to an organization’s daily operations, impacting efficiency, productivity, and service delivery. Examples include system failures, supply chain disruptions, human error, and cybersecurity breaches. A manufacturing plant experiencing a fire, halting production, is a clear example of operational risk.
- Strategic Risk: These are risks related to an organization’s overall goals, strategies, and competitive positioning. Examples include market changes, technological advancements, regulatory shifts, and shifts in customer preferences. A company failing to adapt to a new technology that disrupts its market is an example of strategic risk.
- Reputational Risk: This relates to the potential for damage to an organization’s image, brand, and public perception. Negative publicity, ethical breaches, or product recalls can all significantly impact an organization’s reputation and its ability to operate effectively. A food company experiencing a large-scale product recall due to contamination would face significant reputational risk.
Characteristics of Effective Risk Management
Effective risk management is not simply about avoiding risk; it’s about understanding, assessing, and managing risk in a way that aligns with an organization’s strategic objectives and risk appetite. Key characteristics include:
- Proactive Approach: Identifying and addressing potential risks before they materialize, rather than reacting to crises.
- Comprehensive Assessment: A thorough evaluation of all potential risks, considering both their likelihood and potential impact.
- Integration with Strategy: Risk management should be integrated into the organization’s overall strategic planning process.
- Effective Communication: Clear and consistent communication about risk to all stakeholders.
- Continuous Monitoring and Improvement: Regularly reviewing and updating the risk management plan based on changes in the internal and external environment.
Risk Appetite Across Industries and Organizations
Risk appetite, the amount of risk an organization is willing to accept in pursuit of its objectives, varies significantly across industries and organizations. For example, a startup in the technology sector might have a higher risk appetite than an established financial institution. Startups often need to take more risks to achieve rapid growth, while financial institutions are subject to stricter regulations and a greater need for stability. Similarly, a company in a rapidly evolving industry might have a higher risk appetite than one in a more stable industry. The aerospace industry, with its high safety standards, generally has a lower risk appetite than the gaming industry, where innovation and rapid product releases are prioritized.
Risk Identification and Assessment
Effective risk management hinges on accurately identifying and assessing potential threats. This process involves systematically uncovering risks that could impact project goals and objectives, followed by evaluating their potential severity and likelihood. A thorough approach ensures resources are allocated efficiently to mitigate the most significant risks.
Methods for Identifying Potential Risks
Several methods facilitate the identification of potential risks. Choosing the most appropriate method often depends on the project’s complexity, resources available, and the nature of the risks involved. A combination of techniques often proves most effective.
| Method | Advantages | Disadvantages |
|---|---|---|
| Brainstorming | Encourages collaborative idea generation, can uncover unexpected risks, relatively quick and inexpensive. | Can be dominated by individuals, may overlook less obvious risks, requires skilled facilitation. |
| SWOT Analysis | Provides a structured framework for identifying both internal and external factors, highlights strengths and weaknesses to inform risk response. | Can be overly simplistic, may not capture all relevant risks, requires clear definition of scope. |
| Risk Checklists | Provides a comprehensive list of potential risks, ensures consistency across projects, can be easily adapted. | May not be exhaustive, can be overly generic, risks not on the checklist may be missed. |
Qualitative and Quantitative Risk Assessment Techniques
Risk assessment involves evaluating the likelihood and potential impact of identified risks. Qualitative assessment uses descriptive scales to categorize risks, while quantitative assessment utilizes numerical data for a more precise evaluation.
Qualitative risk assessment uses descriptive terms (e.g., low, medium, high) to rate the likelihood and impact of a risk. For example, a project might assess the risk of “supplier delay” as having a “high” likelihood and a “medium” impact. This provides a relative ranking of risks without requiring precise numerical data.
Quantitative risk assessment involves assigning numerical probabilities and monetary values to risks. For instance, a project might estimate a 20% chance of a $100,000 cost overrun due to unexpected material price increases. This allows for a more precise calculation of the expected monetary value (EMV) of each risk: EMV = Probability × Impact. This allows for a more data-driven approach to prioritization.
Risk Register Template
A risk register is a crucial tool for documenting and tracking identified risks. The following template Artikels essential components:
| Risk Description | Likelihood (Qualitative or Quantitative) | Impact (Qualitative or Quantitative) | Response Plan |
|---|---|---|---|
| e.g., Supplier Delay | High (70% probability) | Medium (estimated $50,000 cost overrun) | Identify alternative suppliers, negotiate longer lead times, secure contingency budget. |
| e.g., Regulatory Change | Medium (30% probability) | High (potential project shutdown) | Monitor regulatory developments, engage legal counsel, develop contingency plans. |
Risk Response Strategies
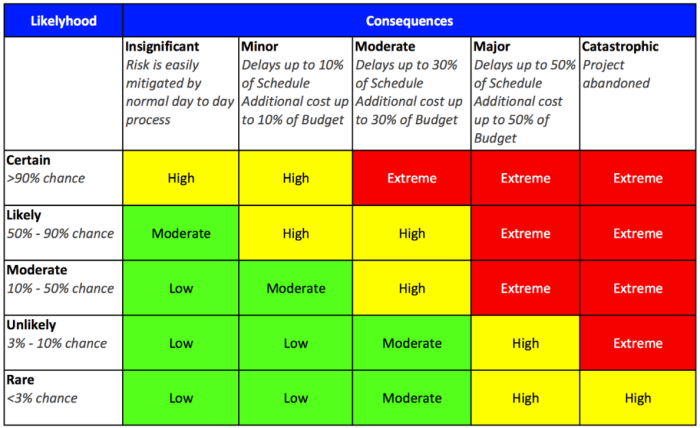
Once risks have been identified and assessed, the next crucial step is developing and implementing appropriate response strategies. Effective risk management isn’t just about identifying problems; it’s about proactively addressing them to minimize potential negative impacts and maximize opportunities. This involves choosing from a range of strategies tailored to the specific nature and severity of each risk.
The Four Main Risk Response Strategies
Four primary strategies guide how organizations address identified risks: avoidance, mitigation, transfer, and acceptance. The selection of the most suitable strategy depends on a careful evaluation of the risk’s likelihood, potential impact, and the organization’s risk appetite.
- Avoidance: This involves eliminating the risk entirely by not undertaking the activity that creates it. For example, a company might decide not to launch a new product in a volatile market to avoid the risk of financial losses associated with market uncertainty. This is a straightforward approach, but it might also mean missing out on potential opportunities.
- Mitigation: This strategy aims to reduce the likelihood or impact of a risk. For instance, a construction company might implement stricter safety protocols to mitigate the risk of workplace accidents. This involves proactive measures to lessen the negative consequences if the risk does occur.
- Transfer: This involves shifting the risk to a third party. A common example is purchasing insurance to transfer the financial risk of property damage or liability. Other examples include outsourcing a high-risk activity to a specialized vendor or using contractual agreements to allocate risk.
- Acceptance: This strategy involves acknowledging the risk and accepting the potential consequences. This is often chosen for low-probability, low-impact risks where the cost of mitigation outweighs the potential loss. For example, a small business might accept the risk of minor equipment malfunctions, opting to repair them as needed rather than investing in expensive preventative maintenance.
Risk Mitigation Techniques
Several techniques can be employed to mitigate risks. The choice depends on the specific risk and organizational context. Effective mitigation often involves a combination of these methods.
- Process Improvement: Streamlining processes to eliminate inefficiencies and reduce error rates can significantly mitigate operational risks. For example, implementing a robust quality control system in manufacturing can reduce the risk of producing defective products.
- Redundancy: Creating backups or alternative systems can reduce the impact of failures. For example, having a backup power generator ensures operations continue during power outages, mitigating the risk of production downtime. Data backups are another prime example.
- Insurance: Transferring the financial burden of specific risks to an insurance company is a common mitigation technique. This protects the organization from significant financial losses due to unforeseen events like fire, theft, or liability claims.
Developing a Risk Response Plan: Hypothetical Scenario
Let’s consider a hypothetical scenario: A software company is launching a new mobile application. A key risk is the potential for a major security breach, which could lead to data loss, reputational damage, and legal repercussions.
Here’s a sample risk response plan:
- Risk: Major security breach of the mobile application.
- Likelihood: Medium (based on industry benchmarks and threat landscape analysis).
- Impact: High (data loss, reputational damage, legal fees, loss of customers).
- Response Strategy: Mitigation and Transfer
- Mitigation Actions:
- Implement robust security protocols during the development phase, including penetration testing and security audits.
- Employ multi-factor authentication for user accounts.
- Regularly update software to patch security vulnerabilities.
- Invest in employee security awareness training.
- Transfer Actions:
- Purchase cyber liability insurance to cover potential financial losses from a data breach.
- Contingency Plan: Develop a comprehensive incident response plan outlining steps to take in the event of a security breach, including communication protocols with affected users and regulatory bodies.
Risk Monitoring and Control
Effective risk monitoring and control are crucial for ensuring that identified risks remain within acceptable tolerances and that the organization’s objectives are not jeopardized. A proactive approach to monitoring allows for timely intervention, preventing minor issues from escalating into major problems. This section details the importance of regular risk monitoring and reporting, best practices for tracking key risk indicators (KRIs), and the implementation of corrective actions.
Regular risk monitoring and reporting provide a continuous feedback loop, enabling organizations to understand the effectiveness of their risk response strategies and to identify emerging risks. This continuous assessment allows for adjustments to be made to the risk management plan as circumstances change. Without this ongoing process, the organization is essentially operating blind, vulnerable to unforeseen circumstances.
Tracking Key Risk Indicators (KRIs)
Tracking key risk indicators (KRIs) is essential for effective risk monitoring. KRIs are metrics that provide early warning signals of potential problems. Regular monitoring of these indicators allows for the identification of trends and patterns that may indicate a developing risk. For example, a rise in customer complaints could be a KRI indicating a potential problem with product quality or customer service. Similarly, a decrease in sales could indicate a problem with marketing or product competitiveness. Effective KRI tracking requires a clearly defined set of indicators, a regular monitoring schedule, and a system for reporting and analysis.
Implementing Corrective Actions
Once a risk has been identified through the monitoring of KRIs, appropriate corrective actions must be implemented promptly. This might involve adjusting existing risk response strategies, developing new strategies, or escalating the issue to a higher level of management. The effectiveness of the corrective actions should be carefully monitored to ensure that the risk is mitigated effectively. For example, if a rise in customer complaints is identified, corrective actions might include improved staff training, changes to product design, or an enhanced customer service process. The effectiveness of these actions should be tracked through continued monitoring of the KRI.
Risk Monitoring and Control Process Flowchart
The risk monitoring and control process can be visualized using a flowchart. The flowchart would begin with the regular monitoring of KRIs. If the KRIs indicate that a risk is exceeding its acceptable tolerance, this would trigger a review of the existing risk response strategy. If the current strategy is deemed insufficient, a new strategy would be developed and implemented. The effectiveness of the new strategy would then be monitored through continued tracking of the KRIs. This cyclical process ensures that risks are continuously monitored and controlled. The flowchart would visually represent this iterative process, showing the feedback loops and decision points involved. For instance, a diamond shape could represent the decision point of whether the KRI exceeds the tolerance, leading to different paths depending on the outcome. Rectangles could represent the actions taken at each stage, such as monitoring KRIs, reviewing the risk response strategy, developing a new strategy, and implementing corrective actions. Finally, arrows would connect the different elements of the flowchart, showing the flow of the process.
Integrating Risk Management into Business Processes
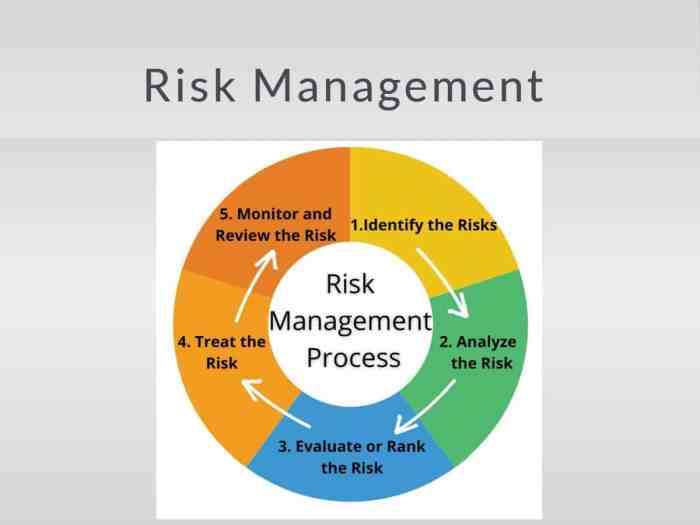
Effective risk management isn’t a standalone function; it’s a crucial component woven into the fabric of successful businesses. Integrating it into daily operations transforms it from a reactive measure to a proactive strategy, enhancing decision-making and fostering sustainable growth. This integration allows organizations to anticipate challenges, capitalize on opportunities, and ultimately, build resilience.
Integrating risk management into various business processes improves decision-making at all levels, from strategic planning to daily operations. It provides a structured framework for evaluating potential threats and opportunities, leading to more informed choices and better outcomes. By understanding and quantifying risks, businesses can make more strategic investments, allocate resources effectively, and improve overall performance.
Risk Management in Strategic Planning and Decision-Making
Risk management is not merely a checklist; it’s a dynamic process intrinsically linked to strategic planning. Integrating it involves proactively identifying and assessing potential risks that could impact the achievement of strategic goals. For instance, a company launching a new product might identify risks related to market competition, technological advancements, or supply chain disruptions. By incorporating these risks into their strategic plan, they can develop mitigation strategies, such as diversification of suppliers or robust marketing campaigns, to enhance the likelihood of success. This proactive approach allows for the development of contingency plans and the allocation of resources to address potential setbacks before they materialize, ultimately increasing the chances of achieving strategic objectives.
Risk Management’s Contribution to Operational Efficiency and Cost Reduction
Integrating risk management into operational processes leads to significant improvements in efficiency and cost reduction. By identifying and mitigating operational risks such as equipment failures, supply chain bottlenecks, or cybersecurity breaches, businesses can minimize disruptions and associated costs. For example, a manufacturing company that implements a robust risk management program for equipment maintenance can prevent costly downtime and production losses. Similarly, identifying and addressing cybersecurity vulnerabilities can prevent significant financial and reputational damage. This proactive approach to risk management not only prevents losses but also allows for the optimization of resources, leading to improved overall efficiency and cost savings.
Risk Management and Compliance with Regulatory Requirements
Compliance with relevant regulations and industry standards is paramount for any organization. Risk management plays a critical role in ensuring compliance by identifying and addressing potential non-compliance risks. This includes risks related to data privacy, environmental regulations, health and safety standards, and other legal requirements. A well-structured risk management program helps organizations establish robust internal controls, implement effective monitoring systems, and ensure adherence to all applicable laws and regulations. Failure to comply can result in significant penalties, legal action, and reputational damage. Therefore, a proactive approach to risk management is essential for maintaining compliance and mitigating potential legal and financial consequences.
Risk Culture and Communication
A strong risk culture is the bedrock of effective risk management. It’s not simply a set of policies; it’s a shared understanding and commitment throughout the organization to proactively identify, assess, and manage risks. A positive risk culture encourages open communication, accountability, and a willingness to learn from both successes and failures. This ultimately leads to better decision-making and improved organizational resilience.
Effective communication is crucial for disseminating risk information and fostering a strong risk culture. Without clear, consistent, and timely communication, risk management efforts will be hampered. Information needs to reach the right people at the right time, in a format they can understand and act upon. This includes not just reporting on existing risks, but also fostering a culture where individuals feel empowered to raise concerns and share information about potential risks.
Effective Communication Strategies for Risk Information
Effective communication of risk information requires a multifaceted approach, tailoring the message and method to the specific audience. This includes clear and concise language, avoiding technical jargon where possible, and utilizing various communication channels to ensure widespread reach. Visual aids, such as charts and graphs, can be particularly effective in conveying complex information. Regular training programs and workshops can reinforce the importance of risk management and ensure everyone understands their roles and responsibilities. Feedback mechanisms should be in place to ensure communication is effective and that any misunderstandings are quickly addressed. Finally, a consistent and transparent communication process builds trust and confidence in the risk management framework.
Risk Communication Plan
A well-structured communication plan ensures that risk information reaches the appropriate audiences effectively and efficiently. This plan should detail the communication channels, frequency, and content tailored to each group’s needs and understanding.
- Senior Management: Regular reports (e.g., monthly or quarterly) summarizing key risks, their potential impact, and proposed mitigation strategies. These reports should use concise language and focus on high-level strategic risks. Presentations during board meetings or executive briefings can also be valuable. The focus here is on strategic decision-making and resource allocation.
- Employees: Regular newsletters, internal memos, or town hall meetings to communicate general risk awareness and relevant training. The language should be accessible and focus on individual roles and responsibilities in managing risk. This might include scenarios relevant to their specific tasks or departments, encouraging them to report potential risks.
- External Stakeholders (e.g., investors, regulators): Formal reports, press releases, and presentations that adhere to regulatory requirements and industry best practices. The communication should be transparent and highlight the organization’s commitment to risk management. The focus is on maintaining trust and confidence. Examples include annual reports, sustainability reports, or responses to regulatory inquiries.
Emerging Risks and Technologies
The modern business landscape is characterized by rapid technological advancements and evolving global challenges. These factors introduce a new category of risks that require proactive and innovative risk management strategies. This section will explore emerging risks associated with cybersecurity, climate change, and technological advancements, and demonstrate how technology itself can be leveraged to improve risk management processes.
Cybersecurity Risks
Cybersecurity threats are constantly evolving, becoming more sophisticated and impactful. Ransomware attacks, data breaches, and denial-of-service attacks pose significant financial and reputational risks to organizations of all sizes. The increasing reliance on interconnected systems and cloud-based services expands the attack surface, making robust cybersecurity measures crucial. Examples include the Colonial Pipeline ransomware attack in 2021, which caused significant fuel shortages, and the 2017 Equifax data breach, which exposed the personal information of millions of individuals. These events highlight the devastating consequences of inadequate cybersecurity defenses and the need for proactive risk mitigation strategies.
Climate Change Risks
Climate change presents a wide range of physical and transition risks to businesses. Physical risks include extreme weather events (hurricanes, floods, wildfires) that can damage infrastructure, disrupt operations, and impact supply chains. Transition risks arise from policy changes, technological innovations, and shifts in consumer preferences aimed at mitigating climate change. For example, carbon pricing mechanisms and regulations on greenhouse gas emissions can impact profitability and investment decisions. The increasing frequency and intensity of extreme weather events, as evidenced by recent hurricanes and droughts, underscore the growing urgency to incorporate climate-related risks into risk management frameworks.
Technological Advancements: Risks and Opportunities
While technology offers numerous benefits, it also introduces new risks. Artificial intelligence (AI) systems, for example, can be vulnerable to bias and manipulation, leading to inaccurate or unfair outcomes. The development and deployment of autonomous vehicles present safety and liability concerns. Furthermore, the rapid pace of technological change can render existing systems and processes obsolete, creating a need for continuous adaptation and investment. The increasing reliance on complex technological systems also raises concerns about system failures and cascading effects.
Technology Enhancing Risk Management
Technology plays a vital role in enhancing risk management processes. Artificial intelligence (AI) can be used for predictive modeling, identifying patterns and anomalies that might indicate emerging risks. Big data analytics allows organizations to analyze vast amounts of data to identify trends, assess vulnerabilities, and improve decision-making. Machine learning algorithms can automate risk assessment and monitoring tasks, freeing up human resources for more strategic activities. Blockchain technology can enhance data security and transparency, reducing the risk of fraud and data breaches.
Comparison of Traditional and Technology-Enhanced Risk Management
| Feature | Traditional Risk Management | Technology-Enhanced Risk Management |
|---|---|---|
| Risk Identification | Relies heavily on expert judgment and historical data; often reactive. | Leverages AI and big data analytics for proactive identification of emerging risks and patterns. |
| Risk Assessment | Qualitative assessments, often subjective and prone to bias. | Quantitative assessments using advanced statistical modeling and simulations; more objective and precise. |
| Risk Response | Manual processes, often slow and inefficient. | Automated workflows and decision support systems; faster and more efficient responses. |
| Risk Monitoring | Periodic reviews and reports; limited real-time visibility. | Real-time monitoring and alerts using dashboards and automated systems; improved responsiveness. |
Case Studies in Risk Management

Examining real-world examples of risk management, both successful and unsuccessful, provides invaluable insights into practical application and potential pitfalls. These case studies highlight the importance of proactive risk identification, thorough assessment, and effective response strategies. Analyzing these examples allows for a deeper understanding of how different approaches impact outcomes.
Successful Risk Management: The Case of Johnson & Johnson’s Tylenol Recall
In 1982, Johnson & Johnson faced a crisis when several bottles of Tylenol were found to contain cyanide, resulting in fatalities. The company’s response, however, is widely considered a textbook example of effective crisis management and risk mitigation. Instead of prioritizing profit, Johnson & Johnson immediately initiated a massive recall of all Tylenol products nationwide, costing them millions of dollars. They also implemented triple-sealed packaging and tamper-resistant caps. This proactive and transparent approach, prioritizing public safety above immediate financial concerns, not only saved lives but also preserved the brand’s reputation in the long run. The swift and decisive action demonstrated a commitment to ethical responsibility and customer well-being, which ultimately bolstered public trust and ensured the brand’s long-term survival. This case study underscores the importance of prioritizing ethical considerations and swift action in high-stakes situations.
Risk Management Failure: The Deepwater Horizon Oil Spill
The Deepwater Horizon oil spill in 2010 resulted from a series of risk management failures by BP, Transocean, and Halliburton. Inadequate risk assessments, cost-cutting measures that compromised safety protocols, and a lack of effective communication and collaboration among the involved parties contributed to the catastrophic event. The lack of a robust safety culture, coupled with a disregard for potential hazards, led to the explosion, resulting in significant environmental damage, loss of life, and billions of dollars in fines and cleanup costs. This incident serves as a stark reminder of the devastating consequences that can arise from neglecting risk management best practices. The subsequent investigations revealed a failure to adequately address well-control risks, a culture that prioritized production over safety, and insufficient oversight by regulatory bodies.
Comparison of Risk Management Approaches
The Tylenol recall and the Deepwater Horizon disaster represent contrasting approaches to risk management. Johnson & Johnson demonstrated a proactive, ethical, and transparent approach, prioritizing public safety and long-term brand reputation. In contrast, BP, Transocean, and Halliburton displayed a reactive, cost-cutting approach that prioritized short-term gains over safety and long-term consequences. The former resulted in the preservation of brand reputation and public trust, while the latter resulted in significant environmental damage, loss of life, and massive financial penalties. This comparison highlights the importance of a comprehensive risk management framework that incorporates ethical considerations, proactive risk identification, thorough assessment, and effective communication throughout the organization and with relevant stakeholders. The difference in outcomes underscores the crucial role of a strong safety culture and a commitment to prioritizing safety over short-term cost savings.
Wrap-Up

By understanding and implementing effective risk management strategies, organizations can significantly reduce their exposure to potential threats, improve operational efficiency, and enhance their overall resilience. This guide has provided a framework for navigating the complexities of risk, from identification and assessment to response and monitoring. Remember that risk management is an ongoing process, requiring continuous monitoring, adaptation, and improvement to remain effective in a constantly evolving environment. Proactive risk management isn’t just about preventing losses; it’s about unlocking opportunities and driving sustainable growth.
Questions Often Asked
What is the difference between risk tolerance and risk appetite?
Risk tolerance refers to the acceptable variation in outcomes, while risk appetite represents the overall level of risk an organization is willing to take to achieve its objectives.
How often should risk assessments be performed?
The frequency of risk assessments depends on the organization’s context and risk profile. However, regular reviews (e.g., annually or semi-annually) are generally recommended, with more frequent assessments for high-risk areas.
What are some common pitfalls to avoid in risk management?
Common pitfalls include failing to adequately identify all potential risks, underestimating the likelihood or impact of risks, and lacking a robust risk response plan. Insufficient communication and a weak risk culture are also major obstacles.