Effective risk management is paramount for any organization navigating the complexities of today’s dynamic environment. From nascent startups to established corporations, understanding and mitigating potential threats is crucial for achieving strategic goals and ensuring long-term sustainability. This guide delves into the core principles of a robust Risk Management Framework, exploring its various components and practical applications across diverse sectors. We will examine different methodologies, tools, and strategies to help you navigate the process of identifying, assessing, responding to, and monitoring risks effectively.
The framework’s adaptability allows for tailoring to specific organizational contexts, whether it’s managing project risks in software development, safeguarding against cybersecurity breaches, or ensuring compliance with industry regulations. By implementing a well-defined framework, organizations can proactively address potential problems, optimize resource allocation, and ultimately enhance their overall resilience and success.
Defining Risk Management Frameworks
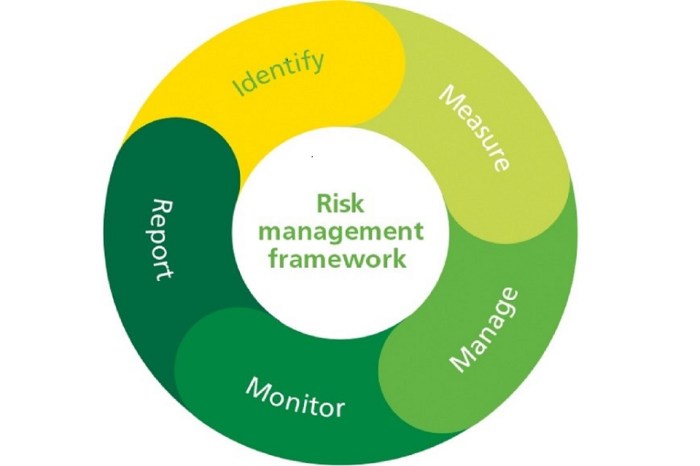
A robust risk management framework provides a structured approach to identifying, assessing, and mitigating potential threats to an organization’s objectives. It ensures consistent application of risk management principles across all levels and functions, fostering a proactive and resilient organizational culture. The effectiveness of a framework hinges on its adaptability to the specific context, resources, and risk appetite of the organization.
Core components of a robust risk management framework typically include establishing context, identifying risks, analyzing risks, evaluating risks, treating risks, monitoring and reviewing risks, and communicating and consulting. Each of these components involves specific activities and processes, ensuring a holistic approach to risk management. For example, establishing context involves defining the scope of the framework, identifying stakeholders, and determining the organization’s risk appetite. Risk identification might involve brainstorming sessions, checklists, or hazard and operability studies (HAZOP). Risk analysis delves into the likelihood and impact of identified risks, often employing both qualitative and quantitative methods.
Examples of Risk Management Frameworks Across Industries
Various industries employ different risk management frameworks tailored to their specific needs and regulatory requirements. For example, the financial services industry often uses frameworks aligned with Basel III regulations, focusing on capital adequacy and operational risk management. The healthcare industry may leverage frameworks like the ISO 14971, emphasizing medical device safety and risk management. The information technology sector commonly utilizes frameworks like the NIST Cybersecurity Framework or ISO 27001, focusing on information security and data protection. These frameworks offer guidelines, best practices, and methodologies, allowing organizations to adapt them to their specific contexts and risk profiles.
Comparison of ISO 31000 and NIST Cybersecurity Framework
The ISO 31000 standard provides a comprehensive and internationally recognized framework for managing all types of risks, encompassing a broad range of organizational contexts. It emphasizes a systematic and iterative approach, focusing on risk governance, risk assessment, and risk treatment. In contrast, the NIST Cybersecurity Framework (CSF) is specifically designed for managing cybersecurity risks within organizations. While it draws upon many principles similar to ISO 31000, the CSF is more prescriptive, offering specific guidelines and best practices for identifying, assessing, and mitigating cybersecurity threats. The CSF utilizes a framework of “Identify, Protect, Detect, Respond, and Recover” functions, providing a structured approach to cybersecurity risk management. While ISO 31000 provides a broader, more general framework, the NIST CSF offers a more targeted and actionable approach to cybersecurity.
Qualitative and Quantitative Risk Assessment Methods
Qualitative risk assessment methods rely on subjective judgments and expert opinions to assess the likelihood and impact of risks. These methods often utilize scales or matrices to rank risks based on descriptive terms like “low,” “medium,” and “high.” Examples include risk scoring matrices and decision trees. Qualitative assessments are valuable when data is limited or when the focus is on understanding the relative importance of different risks. Quantitative risk assessment methods, on the other hand, use numerical data and statistical analysis to estimate the likelihood and impact of risks. These methods often involve probability distributions and cost-benefit analyses. Examples include Monte Carlo simulations and fault tree analysis. Quantitative assessments provide a more precise and objective measure of risk, allowing for more informed decision-making, particularly when dealing with high-impact, high-consequence risks. The choice between qualitative and quantitative methods often depends on the nature of the risk, the availability of data, and the resources available for the assessment.
Risk Identification and Assessment
Effective risk identification and assessment are crucial for the success of any software development project. Failing to proactively identify and manage potential risks can lead to delays, cost overruns, and even project failure. This section details the processes involved in identifying, assessing, and prioritizing risks within a software development context.
Identifying Potential Risks in a Software Development Project
The following table Artikels potential risks associated with a hypothetical software development project. These risks are categorized by type, described in detail, and assessed based on their likelihood and impact. Likelihood is rated on a scale of 1 to 5 (1 being unlikely, 5 being very likely), and impact is rated on a scale of 1 to 5 (1 being low impact, 5 being catastrophic impact).
| Risk Type | Description | Likelihood | Impact |
|---|---|---|---|
| Technical Risk | Unexpected technical challenges during integration of third-party APIs. | 3 | 4 |
| Resource Risk | Key developers leaving the project mid-development. | 2 | 5 |
| Schedule Risk | Underestimation of development time leading to missed deadlines. | 4 | 3 |
| Financial Risk | Unexpected increase in hardware or software costs. | 3 | 3 |
| Scope Risk | Requirement creep leading to scope expansion without budget adjustments. | 4 | 4 |
Conducting a Stakeholder Analysis to Identify Risk Tolerance Levels
Stakeholder analysis involves identifying all individuals or groups who have an interest in the project’s outcome. This includes developers, project managers, clients, investors, and end-users. Understanding each stakeholder’s risk appetite—their willingness to accept risk—is vital for effective risk management. This can be achieved through interviews, surveys, and workshops. For example, a client might have a low risk tolerance, prioritizing project stability and on-time delivery above all else, while investors might have a higher tolerance for risk in exchange for potentially higher returns. The risk tolerance levels identified inform the risk response strategies employed.
Prioritizing Identified Risks
Risks are prioritized based on a combination of their likelihood and impact. A simple method is to multiply the likelihood score by the impact score to obtain a risk score. Risks with higher scores are prioritized for immediate attention. For instance, in the table above, the risk of key developers leaving the project (likelihood 2, impact 5, risk score 10) would be prioritized over the risk of increased hardware costs (likelihood 3, impact 3, risk score 9). More sophisticated methods, such as using a risk matrix with different levels of risk tolerance, can also be employed.
Risk Register Template
A risk register is a centralized repository for tracking all identified risks. It provides a clear overview of the project’s risk landscape and the actions taken to mitigate those risks. The following fields are essential for a comprehensive risk register:
| Field | Description |
|---|---|
| Risk Description | A clear and concise description of the risk. |
| Risk Owner | The individual responsible for managing the risk. |
| Mitigation Plan | The strategy to reduce the likelihood or impact of the risk. |
| Status | The current state of the risk (e.g., open, in progress, closed). |
Risk Response Strategies
Developing effective risk response strategies is crucial for mitigating potential negative impacts on an organization’s objectives. Once risks have been identified and assessed, the next step involves determining how best to address them. This involves a careful evaluation of the risk’s likelihood and potential impact, and selecting a strategy that aligns with the organization’s risk appetite and resources.
Risk Response Strategy Options
Organizations typically employ four primary strategies to address identified risks: avoidance, mitigation, transfer, and acceptance. The choice of strategy depends on a variety of factors, including the severity of the risk, the cost of implementing a response, and the organization’s overall risk tolerance.
- Avoidance: This strategy involves eliminating the risk entirely by not undertaking the activity that gives rise to it. For example, a company might decide not to launch a new product in a volatile market to avoid the risk of financial losses. This is a simple strategy, but it might limit opportunities.
- Mitigation: This involves reducing the likelihood or impact of a risk. For instance, a company might implement stricter security protocols to mitigate the risk of a data breach. Mitigation strategies aim to lessen the potential negative consequences.
- Transfer: This strategy involves shifting the risk to a third party. Purchasing insurance to cover potential losses is a common example of risk transfer. Outsourcing a task to a vendor who accepts the associated risks is another form of transfer.
- Acceptance: This involves acknowledging the risk and deciding to bear the potential consequences. This is typically used for low-probability, low-impact risks where the cost of mitigation outweighs the potential loss. For example, a small business might accept the risk of minor equipment malfunctions.
Risk Response Strategy Decision Tree
A decision tree can be a valuable tool for guiding the selection of an appropriate risk response strategy. The tree typically branches based on the likelihood and impact of the risk. A simple representation would be:
- High Likelihood & High Impact: Avoidance or Mitigation (often both in combination)
- High Likelihood & Low Impact: Mitigation or Acceptance
- Low Likelihood & High Impact: Transfer or Acceptance
- Low Likelihood & Low Impact: Acceptance
Note: This is a simplified representation. A more sophisticated decision tree might incorporate additional factors, such as cost and regulatory requirements.
Data Breach Mitigation Plan
A data breach represents a high-priority risk for many organizations. A robust mitigation plan is crucial to minimize the impact of such an event.
- Regular Security Audits: Conduct regular assessments of the organization’s security infrastructure to identify vulnerabilities.
- Employee Security Training: Educate employees on security best practices, including phishing awareness and password management.
- Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Incident Response Plan: Develop a detailed plan outlining the steps to be taken in the event of a data breach, including communication protocols and forensic analysis.
- Multi-Factor Authentication: Implement multi-factor authentication for all user accounts to enhance security.
- Regular Software Updates: Ensure all software and systems are updated with the latest security patches.
- Data Loss Prevention (DLP) Tools: Utilize DLP tools to monitor and prevent sensitive data from leaving the organization’s network.
Risk Transfer Through Insurance and Outsourcing
Transferring risk involves shifting the responsibility and potential financial consequences of a risk to a third party. This is commonly achieved through insurance or outsourcing.
- Insurance: Purchasing insurance policies, such as cyber liability insurance or property insurance, transfers the financial burden of specific risks to the insurance company. The organization pays premiums in exchange for coverage in the event of a covered loss.
- Outsourcing: Outsourcing certain functions or processes to a third-party vendor can transfer some of the associated risks to the vendor. For example, outsourcing data center operations transfers the risk of infrastructure failures to the vendor. However, it’s crucial to carefully vet vendors and ensure appropriate contractual agreements are in place.
Risk Monitoring and Reporting

Effective risk management isn’t a one-time event; it’s an ongoing process. Regular monitoring and review are crucial for ensuring that identified risks remain under control and that new risks are identified and addressed promptly. This continuous cycle of assessment and adaptation is vital for maintaining organizational resilience and achieving strategic objectives.
Regular monitoring allows for early detection of emerging risks or changes in the risk landscape. It also provides an opportunity to assess the effectiveness of implemented risk mitigation strategies and make adjustments as needed. Without consistent monitoring, organizations risk overlooking critical issues that could significantly impact their operations and goals.
Key Performance Indicators for Risk Management Effectiveness
Tracking key performance indicators (KPIs) provides quantifiable measures of the effectiveness of the risk management framework. These metrics offer insights into the efficiency and efficacy of the implemented risk management processes. Selecting appropriate KPIs depends on the organization’s specific context and risk profile. However, some common examples are valuable across various sectors.
- Number of Risks Identified and Addressed: This KPI tracks the volume of risks identified and the number successfully mitigated, indicating the effectiveness of risk identification and response processes. A high number of identified and addressed risks suggests a proactive approach to risk management. Conversely, a low number might highlight gaps in risk identification or inadequate response strategies.
- Frequency of Risk Reviews: This KPI measures how often risks are reviewed and reassessed, reflecting the organization’s commitment to ongoing risk monitoring. Regular reviews, perhaps quarterly or annually, ensure risks are not overlooked and that mitigation strategies remain relevant.
- Cost of Risk Events: This KPI tracks the financial impact of actual risk events. A low cost of risk events demonstrates effective mitigation strategies and preparedness. High costs may signal weaknesses in the risk management framework, requiring review and improvement.
- Risk Score Changes: This KPI tracks changes in the overall risk score over time. A consistent decrease in the risk score suggests that risk mitigation efforts are successful. Conversely, an increase in the risk score indicates a need for immediate action and a re-evaluation of the risk management approach.
Risk Reporting Template for Executive Management
A concise and well-structured report is essential for effectively communicating risk information to executive management. The report should focus on the most critical risks and their potential impact on the organization’s strategic objectives.
| Risk | Likelihood | Impact | Risk Score | Mitigation Strategy | Mitigation Progress | Owner |
|---|---|---|---|---|---|---|
| Cybersecurity Breach | High | Significant Financial Loss, Reputational Damage | High | Implement multi-factor authentication, employee training | 75% complete | IT Manager |
| Supply Chain Disruption | Medium | Production Delays, Increased Costs | Medium | Diversify suppliers, build buffer stock | 50% complete | Supply Chain Manager |
| Regulatory Changes | Low | Compliance Issues, Fines | Low | Regularly monitor regulatory updates, engage legal counsel | 100% complete | Compliance Officer |
Communicating Risk Information Effectively to Different Stakeholders
Effective risk communication requires tailoring the message to the specific audience. Executive management needs a high-level summary of key risks and their potential impact. Operational staff requires detailed information about specific risks and their mitigation strategies. External stakeholders, such as investors or customers, need information that is transparent and understandable.
Effective communication is key to building trust and ensuring buy-in for risk management initiatives.
Integration with Other Management Systems
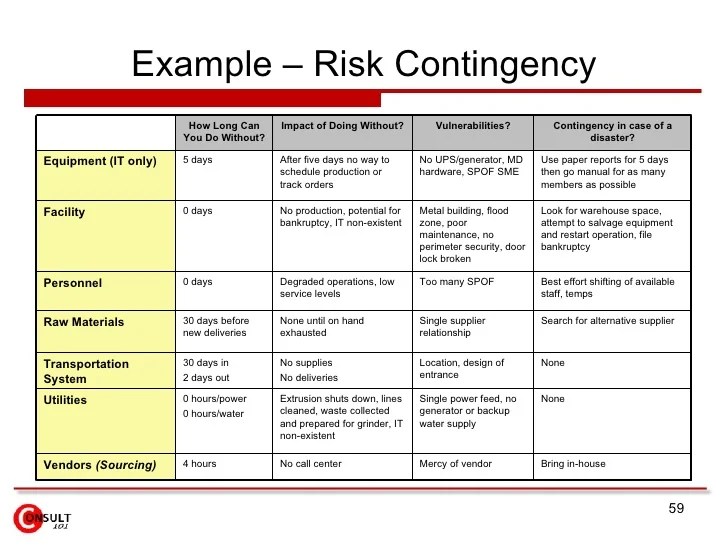
A robust risk management framework doesn’t operate in isolation; its effectiveness hinges on seamless integration with other crucial organizational management systems. This interconnectedness ensures a holistic approach to managing risks and achieving strategic objectives. Effective integration allows for a unified view of organizational challenges and opportunities, leading to more informed and proactive decision-making.
Risk management acts as a vital supporting function across various organizational domains. By identifying and mitigating potential risks, it directly contributes to the success of quality management initiatives, enhances project execution, and ensures ongoing compliance with relevant regulations and standards. This integrated approach prevents duplication of effort and fosters a culture of proactive risk awareness across the entire organization.
Risk Management’s Role in Achieving Organizational Objectives
Risk management is not merely a compliance exercise; it’s a strategic tool that directly supports the achievement of organizational objectives. By proactively identifying and addressing potential threats, organizations can protect their valuable assets, improve operational efficiency, and enhance their ability to capitalize on opportunities. A well-defined risk management framework allows for the development of contingency plans, ensuring business continuity even in the face of unforeseen circumstances. This proactive approach enhances the organization’s resilience and ability to adapt to change, ultimately contributing to the realization of its strategic goals. For example, a company launching a new product might identify market competition as a key risk. A robust risk management process would then lead to the development of a marketing strategy designed to mitigate this risk, potentially increasing the chances of successful product launch and achieving revenue targets.
Risk Management Integration in Agile and Waterfall Methodologies
The integration of risk management differs depending on the chosen project methodology. In waterfall methodologies, risk assessment typically occurs upfront, during the planning phase. Risks are documented, analyzed, and mitigation strategies are defined before the project progresses to the next stage. This approach, while thorough, can be less adaptable to changing circumstances. Agile methodologies, on the other hand, embrace iterative development and continuous risk assessment. Risks are identified and addressed throughout the project lifecycle, allowing for greater flexibility and responsiveness to emerging issues. While both approaches aim to manage risks, their timing and frequency differ significantly, reflecting the inherent flexibility of agile and the structured nature of waterfall. A company developing a software application using an agile approach might conduct daily stand-up meetings to identify and address emerging risks, ensuring quick responses and preventing potential project delays.
Examples of Risk Management’s Contribution to Improved Decision-Making
Effective risk management provides valuable insights that directly enhance decision-making processes. By quantifying potential risks and their associated impacts, organizations can make more informed choices about resource allocation, project prioritization, and strategic planning. For example, a financial institution might use risk assessment models to determine the optimal level of investment in different asset classes, balancing potential returns with the associated risks. Similarly, a manufacturing company might use risk analysis to decide whether to invest in new safety equipment, weighing the cost against the potential for reduced accidents and improved worker safety. The data-driven insights provided by a well-implemented risk management framework contribute to more objective and effective decision-making at all levels of the organization.
Illustrative Example: Cybersecurity Risk Management
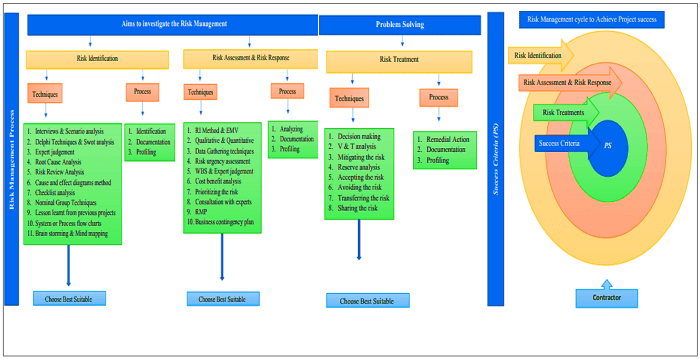
This section provides a practical example of how a cybersecurity risk—specifically, a phishing attack—can be managed using a comprehensive risk management framework. We will walk through the identification, assessment, response, and mitigation of this risk, highlighting both technical and non-technical control measures.
Let’s imagine a scenario where a company experiences a sophisticated phishing attack targeting its employees. The attackers send highly convincing emails appearing to originate from a trusted source, such as the company’s CEO or a major financial institution. These emails contain malicious links or attachments designed to steal credentials or install malware on the victim’s computer.
Cybersecurity Risk Identification and Assessment
The initial step involves identifying the potential for a phishing attack. This can be achieved through various methods, including vulnerability assessments, threat intelligence feeds, and security awareness training for employees. Once identified, the risk must be assessed to determine its likelihood and potential impact.
- Likelihood: The likelihood of a successful phishing attack depends on factors such as the sophistication of the attack, the susceptibility of employees to phishing scams, and the effectiveness of existing security controls. A highly realistic phishing email sent to a large number of employees could result in a high likelihood of success.
- Impact: The potential impact of a successful attack could range from minor data breaches to significant financial losses, reputational damage, and legal repercussions. For example, the compromise of employee credentials could lead to unauthorized access to sensitive company data, while the installation of malware could cripple operations and lead to data exfiltration.
- Risk Rating: The likelihood and impact are combined to determine the overall risk rating. A high likelihood combined with a high impact would result in a high-risk rating, requiring immediate attention.
Cybersecurity Risk Response Strategies
Based on the risk assessment, appropriate response strategies are developed and implemented. These strategies aim to reduce the likelihood and impact of the risk.
- Risk Avoidance: While not always feasible, avoiding certain activities or systems that are particularly vulnerable to phishing could be considered. This might involve restricting access to sensitive systems or data.
- Risk Mitigation: This involves implementing controls to reduce the likelihood and impact of a phishing attack. These controls can be technical or non-technical.
- Risk Transfer: This involves transferring the risk to a third party, such as through cybersecurity insurance.
- Risk Acceptance: In some cases, the risk might be accepted if the cost of mitigation outweighs the potential impact.
Implementing Technical and Non-Technical Controls
Implementing a combination of technical and non-technical controls is crucial for effective mitigation.
- Technical Controls: These include email filtering and anti-spam solutions, intrusion detection and prevention systems, endpoint protection software (antivirus and anti-malware), and multi-factor authentication (MFA) to enhance account security.
- Non-Technical Controls: These focus on educating and empowering employees to recognize and avoid phishing attempts. This includes regular security awareness training, phishing simulations, and clear communication protocols for reporting suspicious emails.
Defense-in-Depth Cybersecurity Strategy
A layered security approach, often referred to as “defense-in-depth,” is essential for mitigating cybersecurity risks. This involves implementing multiple layers of security controls to protect against various types of threats.
Imagine a diagram representing concentric circles. The innermost circle represents the most sensitive data and systems, protected by strong authentication and authorization controls (e.g., MFA, access control lists). The next circle represents the network perimeter, secured by firewalls, intrusion detection/prevention systems, and network segmentation. The outermost circle represents the user layer, protected by security awareness training, email filtering, and endpoint protection. Each layer acts as a barrier, and even if one layer is breached, others are in place to prevent further damage. This layered approach significantly enhances overall security posture.
Conclusive Thoughts

Implementing a comprehensive Risk Management Framework is not merely a compliance exercise; it’s a strategic imperative. By proactively identifying, assessing, and mitigating risks, organizations can foster a culture of preparedness, enhance decision-making, and improve overall operational efficiency. The journey may involve navigating complexities and adapting strategies, but the ultimate reward is a more resilient, adaptable, and successful organization. This guide has provided a foundation; remember to continuously refine and improve your framework to keep pace with evolving challenges and opportunities.
Questions and Answers
What is the difference between risk avoidance and risk mitigation?
Risk avoidance involves eliminating the risk entirely, often by not undertaking the activity that creates the risk. Risk mitigation involves reducing the likelihood or impact of a risk through proactive measures.
How often should a risk register be updated?
The frequency of updates depends on the organization and the nature of the risks. Regular updates, at least monthly or quarterly, are recommended, with more frequent updates for high-priority risks.
What are some common KPIs for measuring risk management effectiveness?
Examples include the number of risks identified and mitigated, the cost of risk events, the time taken to respond to risks, and the overall impact of risks on organizational objectives.
How does a Risk Management Framework contribute to improved decision-making?
By providing a structured approach to identifying and assessing risks, the framework allows for more informed and data-driven decisions, reducing uncertainty and improving the likelihood of successful outcomes.