Business Continuity Planning (BCP) is more than just a checklist; it’s a strategic roadmap for navigating unforeseen disruptions. From natural disasters to cyberattacks, unexpected events can cripple even the most robust organizations. A well-defined BCP, however, transforms these potential crises into manageable challenges, minimizing downtime and preserving operational capacity. This guide delves into the essential components of a comprehensive BCP, empowering businesses of all sizes to proactively safeguard their future.
We will explore the key stages of BCP development, from identifying potential threats and conducting a thorough risk assessment to implementing robust mitigation strategies and regularly testing the plan’s effectiveness. The focus will be on practical applications and actionable steps, providing a clear framework for building resilience and ensuring business continuity in the face of adversity.
Defining Business Continuity Planning (BCP)
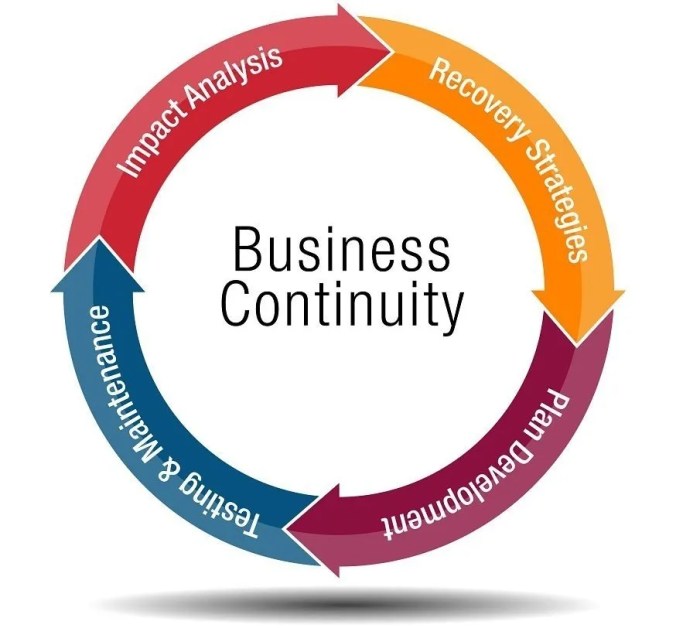
Business Continuity Planning (BCP) is a comprehensive management process designed to ensure that an organization can continue operating during and after a disruptive event. It’s not just about recovering from a disaster; it’s about proactively identifying potential threats, assessing their impact, and implementing strategies to minimize disruption and maintain essential business functions. A well-developed BCP allows businesses to protect their reputation, maintain customer loyalty, and ultimately, survive unforeseen challenges.
Business Continuity Planning encompasses a wide range of activities, designed to mitigate risks and ensure operational resilience. A robust BCP considers various potential disruptions, from natural disasters like earthquakes and hurricanes to cyberattacks and pandemics. It goes beyond simply restoring IT systems; it ensures the continuation of all critical business processes and the protection of valuable assets.
Core Components of a Robust BCP
A successful BCP requires several key elements working in harmony. These include a thorough risk assessment identifying potential threats and their likelihood and impact; a detailed business impact analysis (BIA) pinpointing critical business functions and their dependencies; the development of recovery strategies outlining how to restore operations; resource allocation, ensuring sufficient funding and personnel are available; and a comprehensive communication plan enabling effective information dissemination to stakeholders. Regular testing and updates are crucial to ensure the BCP remains relevant and effective. Finally, a well-defined recovery timeline, detailing steps and expected restoration times for each critical function, is essential.
Differences Between BCP and Disaster Recovery Planning (DRP)
While often used interchangeably, BCP and DRP are distinct but related concepts. BCP is the broader strategy encompassing all aspects of business continuity, including preventing disruptions and recovering from them. DRP, on the other hand, focuses specifically on the technical recovery of IT systems and data after a disaster. DRP is a subset of BCP, addressing only one aspect of the overall business continuity strategy. For instance, a DRP might detail the steps to restore a company’s server infrastructure after a fire, while the broader BCP would encompass strategies to maintain customer communication, alternative production sites, and employee safety during the disruption.
Examples of Businesses Benefiting from a Comprehensive BCP
Many businesses would benefit significantly from a comprehensive BCP. Hospitals, for instance, require robust BCPs to ensure continued patient care during power outages or natural disasters. Financial institutions rely on BCPs to maintain operations and protect sensitive customer data during cyberattacks. Manufacturing companies use BCPs to minimize production downtime and supply chain disruptions. Even small businesses, such as local restaurants or retail stores, can benefit from a basic BCP to protect against unforeseen events like equipment failures or temporary closures due to weather. The benefits extend to all sectors, regardless of size.
A Simple BCP Framework for Small Businesses
Small businesses can implement a simplified BCP framework focusing on their most critical functions. This framework could include a basic risk assessment focusing on high-impact events; a simplified BIA identifying key functions and their dependencies; a communication plan detailing how to contact employees and customers during disruptions; a basic recovery strategy outlining how to restore critical functions; and a simple resource allocation plan ensuring sufficient funds and personnel. Regular review and updates are essential, even with a simplified framework, to ensure its continued relevance. The key is to start small, focusing on the most critical aspects, and gradually expanding the plan as the business grows and evolves.
Risk Assessment and Identification
Effective Business Continuity Planning (BCP) hinges on a thorough understanding of potential threats. A robust risk assessment process identifies vulnerabilities and helps prioritize mitigation strategies, ensuring business resilience. This section details methods for identifying, analyzing, and prioritizing risks to business operations.
Risk assessment is a systematic process of identifying potential threats to an organization’s operations, analyzing their likelihood and potential impact, and developing strategies to mitigate those risks. It involves a careful examination of internal and external factors that could disrupt business activities, ranging from natural disasters to cyberattacks and human error.
Threat Identification and Analysis
Identifying potential threats requires a multi-faceted approach, considering various internal and external factors. A brainstorming session involving key stakeholders across different departments can be highly effective. This collaborative approach ensures a comprehensive understanding of potential risks from diverse perspectives.
| Threat | Likelihood | Impact | Mitigation Strategy |
|---|---|---|---|
| Natural Disaster (e.g., Earthquake) | Medium (depending on location) | High (potential for significant property damage and business interruption) | Develop a disaster recovery plan including offsite data backups, alternative work locations, and insurance coverage. |
| Cyberattack (e.g., Ransomware) | High (increasing frequency and sophistication of attacks) | High (data loss, financial losses, reputational damage) | Implement robust cybersecurity measures, including regular security audits, employee training, and incident response planning. |
| Pandemic (e.g., Flu Outbreak) | Medium (possibility of future outbreaks) | Medium to High (disruption to workforce, supply chain disruptions) | Develop remote work capabilities, establish alternative supply chains, and implement pandemic preparedness protocols. |
| Power Outage | Medium (depending on location and infrastructure) | Medium (disruption to operations, data loss if backups are not available) | Invest in backup power generators, uninterruptible power supplies (UPS), and implement procedures for managing power outages. |
Likelihood and Impact Assessment Methods
Assessing the likelihood and impact of identified risks requires a structured approach. Likelihood can be estimated using qualitative scales (e.g., low, medium, high) or quantitative methods (e.g., probability calculations based on historical data). Impact assessment often focuses on financial losses, reputational damage, and operational disruptions. Qualitative methods like scoring matrices can be used, while quantitative methods may involve financial modeling or cost-benefit analysis.
Risk Assessment Tools and Methodologies
Several tools and methodologies aid in risk assessment. These include:
- Failure Mode and Effects Analysis (FMEA): A systematic approach to identifying potential failure modes and their effects on a system or process.
- Fault Tree Analysis (FTA): A top-down approach that traces the causes of a specific undesired event.
- Risk Matrix: A visual tool that plots risks based on their likelihood and impact, allowing for prioritization.
- SWOT Analysis: Identifies Strengths, Weaknesses, Opportunities, and Threats to the organization.
Risk Prioritization
Once risks have been assessed, they need to be prioritized based on their likelihood and impact. A common approach is to use a risk matrix, where risks are plotted on a graph with likelihood on one axis and impact on the other. Risks in the high likelihood/high impact quadrant receive the highest priority for mitigation.
For example, a cyberattack with high likelihood and high impact (data loss, financial losses, reputational damage) would rank higher than a low likelihood, low impact event like a minor equipment malfunction. Prioritization ensures that resources are allocated effectively to address the most critical risks first.
Business Impact Analysis (BIA)
A Business Impact Analysis (BIA) is a critical component of Business Continuity Planning (BCP). It systematically identifies and analyzes the potential consequences of disruptions to a business’s operations. The BIA helps prioritize resources and efforts by determining which business functions are most critical and the potential impact of their disruption. This analysis informs the development of recovery strategies and ensures that the most vital functions are protected first.
The BIA process involves identifying critical business functions, determining their dependencies, and analyzing the potential impact of disruptions on those functions. This analysis helps determine Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs), crucial metrics for recovery strategies.
Conducting a BIA to Determine Critical Business Functions
The BIA process begins with identifying all business functions. This often involves brainstorming sessions with representatives from various departments to ensure a comprehensive view. Each function is then evaluated based on its importance to the overall business. Factors to consider include revenue generation, legal and regulatory compliance, customer satisfaction, and reputational impact. A scoring system can be used to rank functions based on these factors, helping to prioritize those most critical to the organization’s survival. For instance, a financial institution might prioritize functions related to transaction processing and customer account management above less critical functions like marketing campaigns.
Identifying Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs)
Once critical business functions are identified, the next step is to determine their RTOs and RPOs. The RTO is the maximum acceptable downtime for a critical function before it significantly impacts the business. The RPO, on the other hand, is the maximum acceptable data loss in case of a disruption. For example, a hospital’s emergency room system might have an RTO of 30 minutes and an RPO of 15 minutes, reflecting the critical need for immediate access to patient information. In contrast, a marketing department’s email system might have a higher RTO and RPO, as the impact of a short-term disruption is less severe. Determining these values requires careful consideration of the impact of downtime and data loss on various aspects of the business.
Different BIA Methodologies
Several methodologies can be used to conduct a BIA. These range from simple questionnaires and interviews to more complex, quantitative approaches. One common approach is a structured questionnaire distributed to key personnel across different departments. This allows for gathering consistent data across the organization. Another approach uses facilitated workshops, bringing together key stakeholders to collaboratively assess the impact of various disruptions. More sophisticated methodologies might involve quantitative analysis, such as modeling the financial impact of different disruption scenarios. The choice of methodology depends on the size and complexity of the organization and the resources available.
Example BIA Table
The following table illustrates a simplified BIA for a hypothetical retail business.
| Critical Business Function | Dependencies | RTO (hours) | RPO (hours) |
|---|---|---|---|
| Sales Transactions Processing | Point of Sale (POS) System, Network Connectivity | 2 | 1 |
| Inventory Management | Warehouse Management System, Database | 24 | 12 |
| Customer Relationship Management (CRM) | Database, Network Connectivity | 48 | 24 |
| Website Operations | Web Server, Network Connectivity | 8 | 4 |
Developing a BCP Strategy
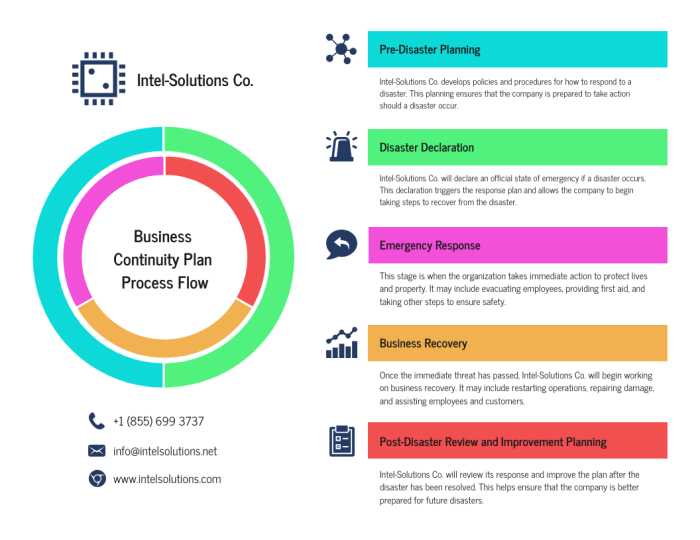
Developing a robust Business Continuity Plan (BCP) strategy involves selecting and implementing methods to ensure business operations continue during and after a disruptive event. This requires a careful consideration of various strategies, their associated costs, and their effectiveness in mitigating potential risks identified during the Business Impact Analysis (BIA). The chosen strategy must align with the organization’s risk tolerance and critical business functions.
BCP Strategies: Backup and Recovery, Redundancy, and Failover
Several key strategies contribute to business continuity. Backup and recovery involves creating copies of critical data and systems, allowing for restoration in case of data loss or system failure. This is a fundamental approach, but its effectiveness depends on the frequency and thoroughness of backups, as well as the speed and ease of recovery. Redundancy, on the other hand, involves creating duplicate systems or processes, ensuring that if one fails, another is immediately available to take over. This is often more expensive upfront but can significantly reduce downtime. Failover is a specific type of redundancy where systems automatically switch to a backup system upon detection of a primary system failure, minimizing disruption. The choice between these strategies often depends on the criticality of the function, the acceptable downtime, and the available budget. A small business might rely heavily on cloud-based backups, while a large financial institution might invest in geographically diverse redundant data centers.
Cost-Effectiveness Comparison of BCP Strategies
The cost-effectiveness of different BCP strategies varies considerably. Backup and recovery solutions, while generally less expensive initially, may require significant investment in storage and recovery testing. Redundancy and failover solutions, such as redundant servers or geographically dispersed data centers, involve substantially higher upfront capital expenditure but can lead to significant cost savings by minimizing downtime and preventing data loss, which can be far more expensive to recover. The optimal strategy balances the cost of implementation with the potential financial impact of a disruption. For instance, a small online retailer might find a cloud-based backup and recovery solution sufficient, while a large manufacturing plant might require a more robust and expensive redundancy strategy to avoid significant production losses.
Maintaining Communication During a Disruption
Maintaining clear and effective communication during a disruption is crucial for coordinating recovery efforts and keeping stakeholders informed. A well-defined communication plan should Artikel communication channels (e.g., email, SMS, dedicated communication platforms), designated communication personnel, and pre-approved messages for various scenarios. This plan should include procedures for updating stakeholders on the situation, recovery progress, and any necessary actions. Organizations should consider using multiple communication channels to ensure redundancy and reach a broad audience, even in the face of network outages. For example, a company might utilize SMS alerts for urgent updates and a dedicated website or intranet for detailed information.
Examples of Successful BCP Strategies
Many organizations have successfully implemented BCP strategies. For example, Amazon’s massive cloud infrastructure utilizes extensive redundancy and failover mechanisms to ensure high availability of its services. Their strategy involves geographically distributed data centers and automated failover systems that minimize disruption to users even in the event of major outages. Similarly, financial institutions often employ robust disaster recovery plans that include redundant data centers and backup systems, ensuring continued operation even in the face of natural disasters or cyberattacks. These successful examples demonstrate the importance of investing in a comprehensive BCP strategy that accounts for various potential disruptions.
Implementing and Testing the BCP
Implementing a Business Continuity Plan (BCP) is not a one-time event; it’s an ongoing process requiring careful planning, execution, and continuous improvement. Successful implementation hinges on clear communication, active participation from all stakeholders, and a commitment to regular testing and refinement. This ensures the plan remains relevant and effective in the face of evolving threats and circumstances.
Implementing the BCP involves translating the strategies and procedures Artikeld in the plan into actionable steps. This includes assigning responsibilities, securing necessary resources, and establishing clear communication channels. It’s crucial to ensure that all employees understand their roles and responsibilities during a disruption, and that the necessary technology and infrastructure are in place to support business operations during a recovery. Regular reviews and updates are also vital to maintain the plan’s relevance.
BCP Implementation Steps
The successful implementation of a BCP requires a phased approach. Each phase builds upon the previous one, ensuring a comprehensive and effective plan. Key steps include resource allocation, staff training, technology acquisition or upgrades, and the establishment of clear communication protocols. Regular testing and updates are essential throughout this process.
The Importance of Regular Testing and Training Exercises
Regular testing and training are paramount to ensure the BCP remains effective and that personnel are adequately prepared to respond to disruptions. These exercises identify weaknesses in the plan, highlight areas requiring improvement, and build team cohesion and familiarity with the procedures. The frequency and type of testing should be tailored to the organization’s specific risks and critical business functions. Without regular testing, a BCP can become outdated and ineffective, leaving the organization vulnerable. For instance, a company that experiences a significant technological shift without updating its BCP risks finding its recovery strategies obsolete and ineffective during a real crisis.
Types of BCP Tests
Several types of tests can be used to evaluate the effectiveness of a BCP. Each test offers a different level of complexity and realism, allowing organizations to progressively assess their preparedness.
- Tabletop Exercises: These are relatively low-cost, low-stress exercises that involve a group discussion of potential scenarios. Participants walk through the BCP, identifying potential problems and refining response strategies. A recent tabletop exercise conducted by a financial institution revealed a gap in their communication protocols during a simulated cyberattack, leading to improvements in their alert system and escalation procedures.
- Functional Exercises: These exercises involve testing specific functions or processes Artikeld in the BCP. For example, a company might test its data backup and recovery procedures or its ability to switch to an alternate work location. A retail company successfully tested its point-of-sale system failover during a functional exercise, preventing significant revenue loss during a subsequent power outage.
- Full-Scale Simulations: These are the most comprehensive and realistic tests, involving a complete disruption of normal operations. They simulate a real-world event, allowing the organization to test its entire BCP from start to finish. A large manufacturing company conducted a full-scale simulation of a major earthquake, identifying critical vulnerabilities in their supply chain and leading to significant improvements in their disaster recovery strategies.
Documenting and Maintaining the BCP
Maintaining a well-documented and regularly updated BCP is crucial for its ongoing effectiveness. The BCP document should be easily accessible, regularly reviewed, and updated to reflect changes in the organization’s operations, risks, and technology. A version control system is recommended to track changes and ensure everyone is working with the most up-to-date version. Regular reviews should be scheduled, and a designated individual or team should be responsible for maintaining the plan. The documentation should include a clear Artikel of the plan, contact information for key personnel, detailed procedures for various scenarios, and a record of all testing and training exercises. This ensures that the BCP remains a living document that adapts to the evolving needs of the organization. Failure to maintain the BCP could lead to inadequate responses during actual disruptions, causing significant financial and reputational damage.
Communication and Stakeholder Management
Effective communication is the bedrock of a successful business continuity plan. During a disruption, clear, consistent, and timely information flow is crucial for minimizing damage, maintaining operational efficiency, and preserving stakeholder confidence. A well-defined communication plan ensures everyone knows their roles, responsibilities, and how to access critical information.
The importance of a robust communication strategy cannot be overstated. A breakdown in communication can lead to confusion, panic, and ultimately, hinder recovery efforts. Conversely, a well-executed communication plan can significantly reduce the impact of a disruptive event by fostering collaboration, transparency, and a sense of control. This section will explore strategies for communicating with various stakeholders and Artikel the key elements of a comprehensive communication plan.
Communication Channels and Strategies for Different Stakeholders
Effective communication during a crisis requires a multi-channel approach tailored to the specific needs of each stakeholder group. Employees, customers, suppliers, and regulatory bodies all have different information requirements and preferred communication methods. For instance, employees may require regular updates via email and internal messaging systems, while customers might prefer updates through the company website, social media, or phone calls. Suppliers need clear communication about potential delays or changes in orders, and regulatory bodies need prompt notification of any incidents that could impact public safety or compliance. A tailored approach ensures that the right information reaches the right people through the most effective channels.
Designing a Communication Plan: Channels and Escalation Procedures
A comprehensive communication plan should Artikel specific communication channels, responsible parties, and escalation procedures. This plan should detail who is responsible for disseminating information, the specific channels to be used (e.g., email, SMS, phone calls, social media, website updates), and the frequency of updates. It should also define escalation procedures for handling critical situations or when communication channels are disrupted. For example, a tiered escalation system might involve initial communication through email, followed by SMS alerts for urgent updates, and finally, phone calls for critical incidents. The plan should also specify communication protocols for different types of disruptions, ensuring flexibility and adaptability. Regular testing and review of the plan are crucial to ensure its effectiveness.
Examples of Effective Communication Strategies During Crises
During Hurricane Katrina, some companies proactively communicated with employees and customers well in advance of the storm’s landfall, providing clear instructions and support. This proactive approach minimized confusion and fostered a sense of security. Conversely, companies that failed to communicate effectively experienced significant reputational damage and operational disruptions. Similarly, during the COVID-19 pandemic, companies that provided transparent and regular updates to their employees about safety measures and work-from-home policies experienced higher levels of employee morale and productivity compared to those that lacked clear communication. These examples highlight the importance of clear, consistent, and timely communication in mitigating the negative impacts of disruptive events. The key is to be prepared, proactive, and transparent in all communications.
BCP Maintenance and Review

A Business Continuity Plan (BCP) is not a static document; it requires ongoing maintenance and regular review to ensure its continued effectiveness. Changes in the business environment, technological advancements, and lessons learned from past incidents necessitate updates to maintain the plan’s relevance and resilience. Ignoring this crucial aspect can render the BCP obsolete and ineffective during a real crisis.
Regular review and updating of the BCP are essential to its success. A well-maintained BCP provides a dynamic framework that adapts to evolving risks and ensures the organization remains prepared for various disruptions. This iterative process enhances the plan’s accuracy, completeness, and overall effectiveness in mitigating business interruptions. Failure to update the plan could lead to inadequate responses during an incident, resulting in increased downtime, financial losses, and reputational damage.
Incorporating Lessons Learned from Past Incidents
A thorough post-incident review is critical for improving the BCP. This involves analyzing what worked well, what didn’t, and identifying areas for improvement. Documenting these lessons learned ensures that future responses are more effective and efficient. This process should include gathering information from all relevant stakeholders, analyzing the effectiveness of existing procedures, and identifying gaps in the plan. For example, if a recent power outage revealed weaknesses in the backup power system, the BCP should be updated to reflect this and include mitigation strategies such as investing in a more robust system or establishing alternative power sources. A detailed record of these incidents, including root cause analysis and corrective actions, should be maintained.
BCP Review Schedule
Establishing a regular schedule for BCP review is paramount. The frequency of reviews depends on several factors, including the organization’s risk profile, the industry it operates in, and the complexity of its operations. A suggested schedule could be:
- Annual Review: A comprehensive review of the entire BCP, including all sections and procedures, should be conducted annually. This review should assess the overall effectiveness of the plan and identify areas for improvement.
- Quarterly Review: A shorter, more focused review of critical aspects of the BCP, such as contact information, recovery procedures, and resource availability, can be performed quarterly. This ensures that the plan remains up-to-date and accurate.
- Post-Incident Review: A thorough review should be conducted after any significant incident, regardless of the frequency of scheduled reviews. This review should focus on identifying lessons learned and incorporating necessary changes into the BCP.
This schedule should be documented and communicated to all relevant stakeholders.
Metrics for Measuring BCP Effectiveness
Several metrics can be used to measure the effectiveness of a BCP. These metrics provide quantifiable data to assess the plan’s performance and identify areas needing improvement. Examples include:
- Recovery Time Objective (RTO) Achievement: This measures the time it takes to restore critical business functions after a disruption. A successful BCP should result in RTOs being met or exceeded.
- Recovery Point Objective (RPO) Achievement: This measures the acceptable data loss in the event of a disruption. A well-designed BCP minimizes data loss, ensuring that the RPO is met.
- Downtime Reduction: Tracking the reduction in downtime following incidents demonstrates the BCP’s effectiveness in minimizing business interruptions.
- Cost Savings: Calculating the cost savings resulting from successful BCP implementation, such as reduced recovery costs or avoided losses, provides a strong indicator of its value.
- Stakeholder Satisfaction: Gathering feedback from stakeholders involved in the BCP’s implementation and execution provides valuable insights into its effectiveness and areas for improvement.
Regular monitoring of these metrics allows for continuous improvement of the BCP and ensures its ongoing relevance.
Technology and BCP
Technology plays a crucial role in supporting business continuity by enabling organizations to maintain operations during disruptive events. Effective technology integration allows for quicker recovery times, minimized data loss, and enhanced overall resilience. A well-designed BCP leverages technology to ensure business processes continue, even when faced with significant challenges.
Technology’s contribution to business continuity extends beyond simple redundancy. It facilitates proactive risk mitigation and enables organizations to adapt to unforeseen circumstances more effectively. The strategic use of technology can significantly improve the efficiency and effectiveness of a BCP, transforming a reactive approach to a more proactive and resilient posture.
Cloud Computing in Business Continuity
Cloud computing offers several advantages for business continuity. By migrating critical applications and data to the cloud, organizations can ensure access even if their on-premise infrastructure is compromised. Cloud providers typically offer multiple data centers and robust disaster recovery capabilities, providing geographic redundancy and high availability. This reduces the risk of significant downtime and data loss. For example, a company could use cloud-based file storage to ensure data backups are accessible from anywhere, facilitating rapid recovery after a natural disaster or cyberattack. The scalability of cloud services also allows businesses to easily adjust their IT resources based on demand during recovery efforts.
Virtualization and Business Continuity
Virtualization enables the creation of virtual machines (VMs) that run independently of the underlying physical hardware. This allows for easy replication and migration of VMs to different servers or data centers, ensuring business continuity in the event of hardware failure. For example, a company could have virtualized servers running critical applications replicated to a secondary data center. If the primary data center experiences an outage, the VMs can be quickly switched over to the secondary location, minimizing disruption. Virtualization also facilitates testing and training for disaster recovery scenarios without impacting production environments.
Data Replication and Business Continuity
Data replication creates copies of data at different locations, ensuring data availability even if one location is affected by a disruption. This can involve replicating data to a secondary data center, a cloud storage service, or even to external storage devices. Real-time replication minimizes data loss, while asynchronous replication provides a cost-effective solution with a slightly higher risk of data loss in the event of a disaster. For instance, a financial institution might use real-time data replication to ensure that transaction data is always available, minimizing the impact of a server failure.
Security Considerations for Technology Solutions in BCP
Implementing technology solutions for business continuity requires careful consideration of security risks. Data security, access control, and disaster recovery plans must be thoroughly addressed. Robust security measures, such as encryption, access control lists, and multi-factor authentication, are essential to protect sensitive data stored in the cloud or replicated across different locations. Regular security audits and penetration testing should be conducted to identify and mitigate potential vulnerabilities. Furthermore, incident response plans should be in place to address security breaches and data loss. For example, encryption of data at rest and in transit is crucial to prevent unauthorized access, even if a data breach occurs.
Improving BCP Efficiency and Effectiveness with Technology
Technology significantly enhances the efficiency and effectiveness of BCP. Automated systems can streamline the recovery process, reducing manual intervention and speeding up the restoration of critical business functions. For instance, automated failover systems can quickly switch operations to backup systems in case of an outage, minimizing downtime. Real-time monitoring tools can provide early warning of potential disruptions, allowing for proactive mitigation. Furthermore, technology facilitates improved communication and collaboration during a crisis, enabling faster decision-making and coordinated responses. A well-integrated technology solution can reduce the overall cost of BCP implementation and maintenance while increasing the effectiveness of the plan.
Conclusive Thoughts
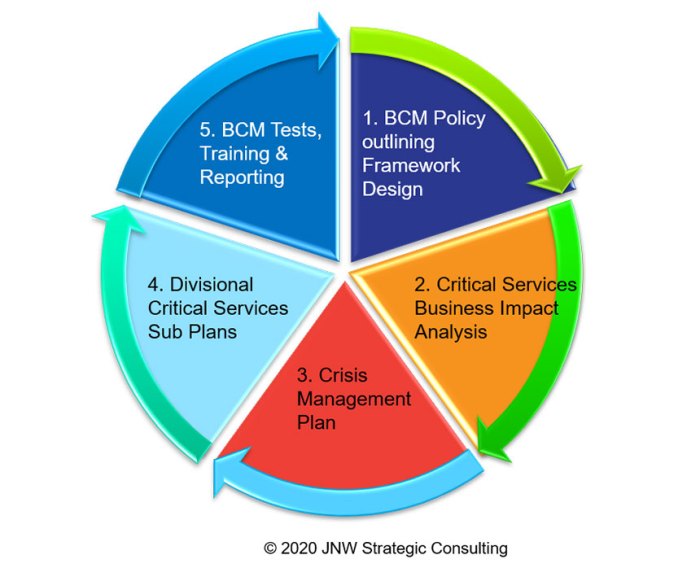
Developing a robust Business Continuity Plan is not a one-time task but an ongoing process of assessment, adaptation, and improvement. By proactively identifying risks, implementing mitigation strategies, and regularly testing the plan, businesses can significantly reduce their vulnerability to disruptions. The investment in BCP translates to enhanced operational resilience, minimized financial losses, and the preservation of valuable relationships with customers and stakeholders. Ultimately, a well-executed BCP ensures that your business can not only survive unforeseen events but also thrive in the face of adversity.
Clarifying Questions
What is the difference between BCP and Disaster Recovery Planning (DRP)?
BCP is a broader concept encompassing all aspects of maintaining business operations during disruptions. DRP is a subset of BCP focusing specifically on recovering IT systems and data after a disaster.
How often should a BCP be tested?
The frequency of testing depends on the organization’s risk profile and the criticality of its operations. At minimum, annual testing is recommended, with more frequent testing for high-risk scenarios.
What is the role of insurance in BCP?
Insurance can mitigate some financial losses resulting from disruptions, but it’s not a substitute for a comprehensive BCP. BCP focuses on minimizing disruptions, while insurance covers the aftermath.
How can small businesses afford a BCP?
Small businesses can start with a simple, cost-effective BCP focusing on their most critical functions. Many free resources and templates are available online.