In today’s dynamic business landscape, unforeseen disruptions can severely impact operations. A robust Business Continuity Plan (BCP) isn’t just a good idea; it’s a necessity for organizations of all sizes. This guide provides a comprehensive framework for developing and implementing a BCP, helping you navigate potential crises and ensure the continued operation of your business. We’ll explore risk assessment, plan development, testing procedures, and crucial technological considerations to build resilience against various threats.
From identifying potential risks and analyzing their impact to creating detailed recovery strategies and implementing effective communication protocols, this guide equips you with the knowledge and tools to safeguard your business against the unexpected. We will delve into the intricacies of recovery time objectives (RTOs) and recovery point objectives (RPOs), ensuring your business can recover quickly and efficiently from any disruption. The importance of regular testing and updates to your BCP will also be emphasized, ensuring its ongoing relevance and effectiveness.
Introduction to Business Continuity Planning
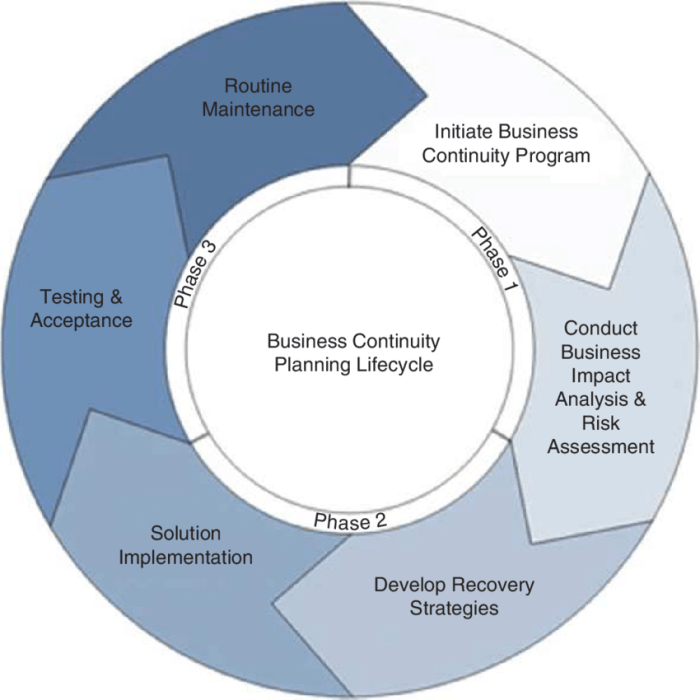
Business Continuity Planning (BCP) is the process of creating a plan to ensure that an organization can continue its essential operations during and after a disruptive event. This involves identifying potential threats, assessing their impact, and developing strategies to mitigate those risks and maintain business operations. A well-developed BCP minimizes downtime, protects revenue streams, and safeguards the organization’s reputation.
BCP is crucial for organizations of all sizes. While larger enterprises might face more complex disruptions and have more extensive resources, even small businesses are vulnerable to unforeseen events. A robust BCP allows smaller organizations to compete more effectively by ensuring resilience and operational stability. Larger organizations benefit from minimizing financial losses, maintaining customer trust, and upholding regulatory compliance through a comprehensive BCP. The scale of the plan will differ, but the underlying principles remain the same: proactive risk management and the ability to quickly recover from unforeseen circumstances.
Potential Disruptions Requiring a BCP
A wide range of events can disrupt business operations, necessitating a well-defined BCP. These disruptions can be categorized as natural disasters, technological failures, human error, or external factors. For example, a hurricane could damage physical infrastructure, causing widespread power outages and halting operations. A cyberattack could compromise sensitive data, leading to financial losses and reputational damage. A critical employee’s unexpected absence due to illness could temporarily halt critical processes. Finally, economic downturns or changes in market demand can impact revenue and necessitate operational adjustments. Effective BCPs anticipate these varied scenarios and Artikel recovery strategies for each.
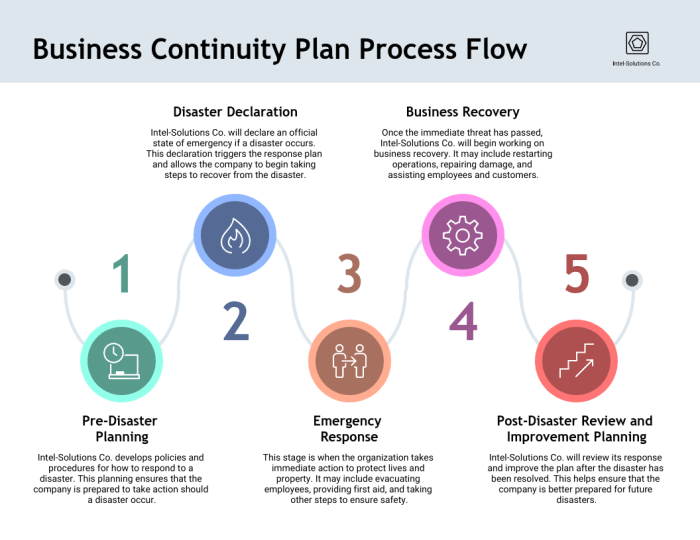
A Simple BCP Process Flowchart
The BCP process can be visualized using a simple flowchart. Imagine a flowchart starting with a “Trigger Event” box, representing any disruptive event. This box would connect to a “Risk Assessment” box, detailing the impact of the event on the organization. This box then leads to a “Recovery Strategy Development” box, outlining the steps needed to restore operations. Following this is an “Implementation and Testing” box, where the plan is put into action and regularly tested for effectiveness. Finally, the flowchart concludes with a “Monitoring and Review” box, ensuring the plan remains current and relevant. This cyclical process ensures the BCP remains a living document, constantly adapted to evolving risks and organizational changes. The flowchart visually represents the iterative nature of BCP, highlighting the importance of continuous improvement and adaptation.
Risk Assessment and Analysis
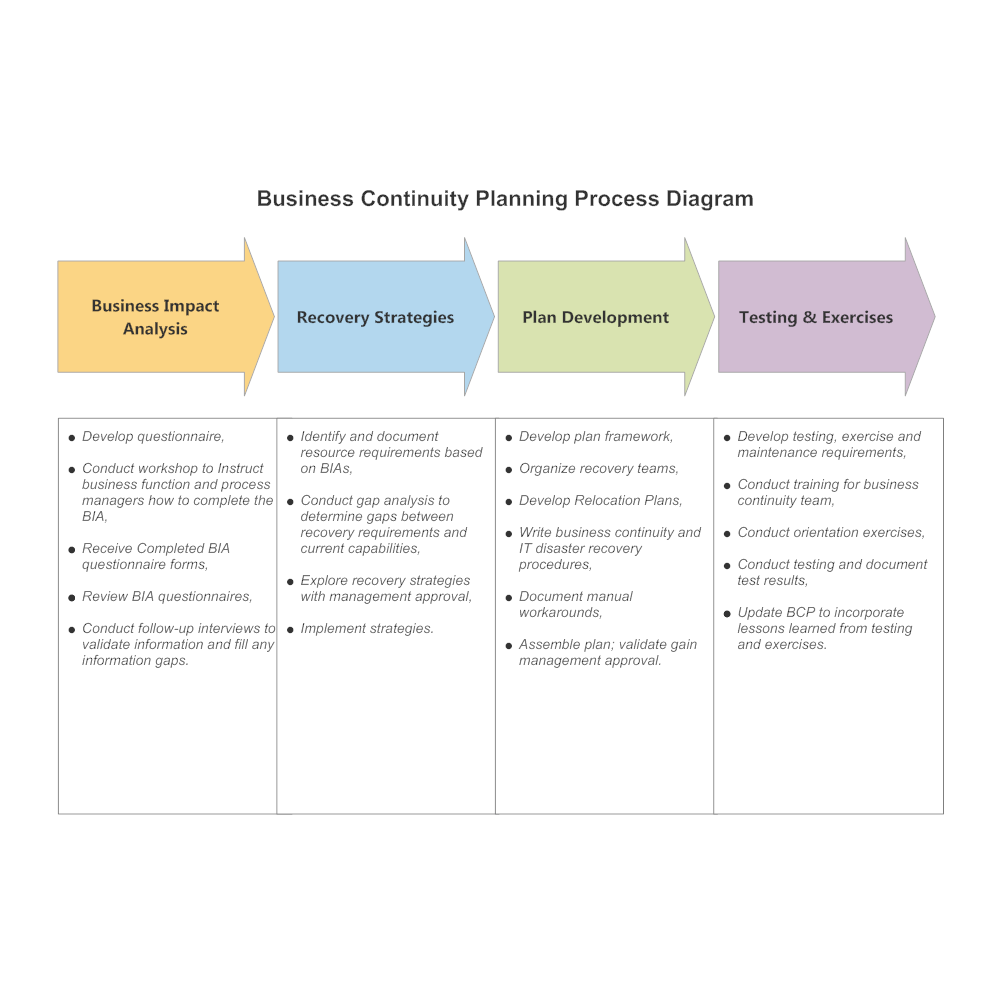
A robust Business Continuity Plan (BCP) hinges on a thorough understanding of potential threats to your organization. Risk assessment and analysis is the crucial first step in identifying these threats, evaluating their likelihood and potential impact, and developing mitigation strategies. This process allows for proactive planning, minimizing disruption and ensuring business resilience.
Identifying potential internal and external threats requires a comprehensive approach. We need to consider a wide range of factors that could negatively affect business operations.
Identifying Internal and External Threats
Internal threats stem from within the organization and can include things like employee negligence, IT system failures, inadequate security protocols, or even internal fraud. External threats originate outside the organization and encompass a broader spectrum, including natural disasters, cyberattacks, pandemics, economic downturns, supply chain disruptions, and regulatory changes. A systematic review of all aspects of the business is necessary to identify potential vulnerabilities. For example, a manufacturing company might assess the risk of equipment malfunction, while a financial institution would prioritize the risk of a cyber security breach.
Assessing Likelihood and Impact of Risks
Once potential risks are identified, we need to evaluate their likelihood and potential impact on the business. Likelihood refers to the probability of a risk occurring, while impact assesses the severity of consequences if the risk materializes. Several methods exist for this assessment, including qualitative approaches (using descriptive scales like low, medium, and high) and quantitative approaches (using statistical data and probability calculations). The choice of method depends on the complexity of the business and the available data. Qualitative methods are often sufficient for smaller organizations, while larger organizations might benefit from more sophisticated quantitative analysis.
Risk Assessment Matrix
The following table provides a structured way to document the identified risks, their likelihood, impact, and planned mitigation strategies.
| Risk | Likelihood | Impact | Mitigation Strategy |
|---|---|---|---|
| Major Power Outage | Medium | High | Invest in backup power generators and redundant power supplies. Regularly test backup systems. |
| Cybersecurity Breach | Medium | High | Implement robust cybersecurity measures, including firewalls, intrusion detection systems, and employee security awareness training. Regularly update security software. |
| Key Employee Loss | Low | Medium | Develop comprehensive succession plans and cross-train employees. |
| Natural Disaster (Flood) | Low | High | Develop a disaster recovery plan that includes data backups stored offsite and a plan for relocating critical operations. Consider flood insurance. |
Conducting a Business Impact Analysis (BIA)
A Business Impact Analysis (BIA) is a critical process to understand the potential consequences of disruptions to business operations. The BIA systematically identifies critical business functions, assesses their dependencies, and determines the potential impact of disruptions on these functions. This analysis helps prioritize resources and develop effective recovery strategies. The BIA typically involves interviewing key personnel, reviewing business processes, and analyzing data to determine recovery time objectives (RTOs) and recovery point objectives (RPOs). RTOs define the maximum acceptable downtime for a business function, while RPOs specify the maximum acceptable data loss. For instance, a hospital’s RTO for its emergency room system would likely be much lower than that of a retail store’s online ordering system. The BIA results directly inform the development of recovery strategies and resource allocation within the BCP.
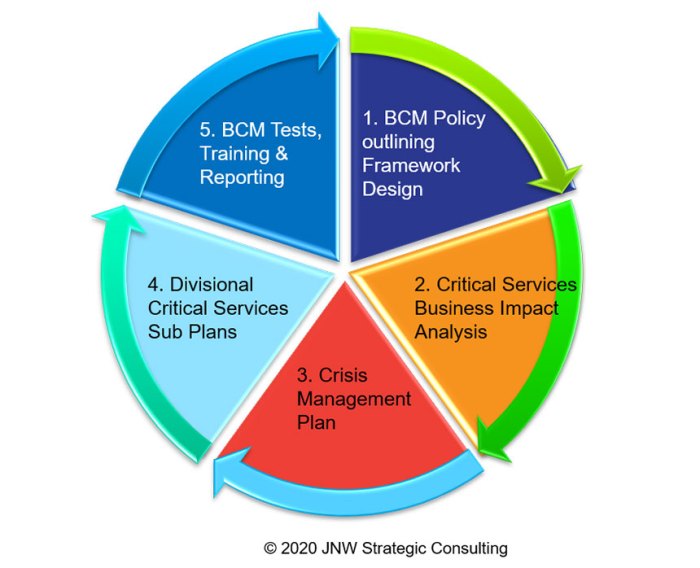
Developing a Business Continuity Plan

Creating a robust Business Continuity Plan (BCP) is crucial for organizational resilience. A well-developed BCP Artikels the steps an organization will take to ensure continued operations during and after a disruptive event. This plan should be a living document, regularly reviewed and updated to reflect changes in the business environment and potential threats.
Key Elements of a Comprehensive BCP Document
A comprehensive BCP needs to cover a wide range of aspects to be truly effective. It’s not simply a list of emergency contacts; it’s a detailed roadmap for navigating unforeseen circumstances. The level of detail required will vary depending on the size and complexity of the organization, but all plans should include the fundamental elements Artikeld below.
- Business Impact Analysis (BIA): This section identifies critical business functions and assesses the potential impact of disruptions on those functions. It quantifies potential losses and helps prioritize recovery efforts.
- Risk Assessment and Analysis: This detailed assessment identifies potential threats (natural disasters, cyberattacks, pandemics, etc.) and their likelihood and potential impact on the organization. It informs the development of mitigation strategies.
- Recovery Strategies: This Artikels specific steps for recovering critical business functions following a disruptive event. This includes identifying alternative work locations, data backups, and communication protocols.
- Resource Allocation: This section details the resources (financial, human, technological) required to implement the recovery strategies. It also includes a plan for securing these resources in advance.
- Communication Plan: This Artikels how the organization will communicate with employees, customers, suppliers, and other stakeholders before, during, and after a disruptive event. This is critical for maintaining trust and confidence.
- Testing and Maintenance: This section describes the process for regularly testing and updating the BCP to ensure its effectiveness and relevance. Regular testing is crucial for identifying weaknesses and improving the plan.
Importance of RTOs and RPOs
Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) are critical metrics within a BCP. They define acceptable downtime and data loss. Failing to define these clearly can lead to significant financial and reputational damage.
RTO: The maximum tolerable downtime for a business function before unacceptable consequences occur. For example, an RTO of 4 hours for an e-commerce platform means the site must be restored within 4 hours to avoid significant revenue loss.
RPO: The maximum acceptable data loss in the event of a disruption. An RPO of 24 hours for a financial institution means that no more than 24 hours of data can be lost during a system failure.
Defining these objectives ensures that recovery efforts are focused on the most critical functions and data, maximizing efficiency and minimizing impact.
Sample BCP Structure
A well-structured BCP enhances readability and usability. The following is a sample structure; adjustments might be needed based on the organization’s specific needs.
- 1. Introduction
- 1.1 Purpose and Scope
- 1.2 Definitions
- 2. Business Impact Analysis (BIA)
- 2.1 Critical Business Functions
- 2.2 Impact Assessment
- 3. Risk Assessment and Analysis
- 3.1 Threat Identification
- 3.2 Vulnerability Assessment
- 3.3 Risk Prioritization
- 4. Recovery Strategies
- 4.1 Recovery Time Objectives (RTOs)
- 4.2 Recovery Point Objectives (RPOs)
- 4.3 Recovery Procedures
- 5. Resource Allocation
- 5.1 Financial Resources
- 5.2 Human Resources
- 5.3 Technological Resources
- 6. Communication Plan
- 6.1 Internal Communication
- 6.2 External Communication
- 6.3 Media Relations
- 7. Testing and Maintenance
- 7.1 Testing Procedures
- 7.2 Review and Update Schedule
Incorporating Crisis Communication Strategies
Effective crisis communication is paramount during and after a disruptive event. The BCP should clearly define communication channels, key messages, and responsibilities for disseminating information. This includes pre-approved messaging for various scenarios, designated spokespeople, and procedures for handling media inquiries. A well-defined communication strategy can significantly mitigate reputational damage and maintain stakeholder confidence. For example, a pre-written press release template for a data breach, specifying who will speak to the media and what information will be released, would help maintain control and consistency during a critical event.
Business Continuity Strategies and Procedures
Effective business continuity relies on proactive strategies and well-defined procedures to mitigate the impact of disruptions. This section details various approaches and provides examples to guide the development of your organization’s specific plan. Understanding these strategies and implementing robust procedures are crucial for minimizing downtime and ensuring business resilience.
Business Continuity Strategies: A Comparison
Several key strategies contribute to business continuity. Backup and recovery involves creating copies of critical data and systems, allowing for restoration in case of failure. Failover, on the other hand, automatically switches operations to a secondary system or location when the primary system becomes unavailable. Redundancy incorporates duplicate components or systems, ensuring continued operation even if one part fails. Each strategy offers a different level of protection and cost, necessitating a careful evaluation based on risk assessment and organizational needs. For example, a small business might prioritize backup and recovery for essential data, while a large financial institution might implement full redundancy for critical systems.
Procedures for Various Disruption Scenarios
Effective business continuity requires detailed procedures for handling specific scenarios.
Data Loss Procedures
Data loss procedures should Artikel steps for identifying the extent of the loss, recovering data from backups, and implementing measures to prevent future occurrences. This includes regularly scheduled backups, offsite storage of backups, and robust data security protocols. For instance, a procedure might involve verifying the integrity of backups, restoring data to a test environment before deploying to production, and conducting a post-incident review to identify vulnerabilities.
Power Outage Procedures
Power outage procedures should address immediate actions, such as switching to backup power sources (generators), securing sensitive equipment, and notifying relevant personnel. These procedures might also include a communication plan to inform clients and stakeholders about the outage and expected restoration time. A detailed checklist of actions, responsibilities, and contact information is essential. For example, the plan might specify who is responsible for starting the generator, how to monitor fuel levels, and what communication channels to use for updates.
Natural Disaster Procedures
Procedures for natural disasters should incorporate evacuation plans, data backup and recovery strategies, and communication protocols for remote work. These plans should account for the specific risks faced by the organization, such as flooding, earthquakes, or hurricanes. Pre-defined communication channels, alternate work locations, and emergency contact lists are critical. For example, the plan could include pre-arranged agreements with temporary office spaces, procedures for securing physical assets, and protocols for contacting employees to ensure their safety.
Essential Resources for Business Continuity
The success of a business continuity plan hinges on having readily available resources.
A comprehensive list of essential resources includes:
- Backup power sources (generators, UPS systems)
- Offsite data backups and recovery systems
- Redundant hardware and software
- Communication systems (phones, email, messaging platforms)
- Alternate work locations or remote access capabilities
- Emergency contact lists and communication protocols
- Trained personnel for various roles and responsibilities
- Disaster recovery site (hot site, cold site, warm site)
- Security measures to protect physical and digital assets
- Insurance policies covering business interruption
Communication Protocols During Disruptions
Effective communication is vital during disruptions.
Clear communication protocols are crucial for keeping stakeholders informed and coordinating responses. These protocols should define communication channels, frequency of updates, and responsible parties for different audiences (employees, customers, partners, investors). For example, a company might use email for general updates, text messages for urgent alerts, and a dedicated website or social media page for public information. Pre-defined messaging templates can ensure consistency and efficiency in communication. Regular drills and simulations can help refine communication procedures and ensure team preparedness.
Testing and Maintenance of the BCP
A well-developed Business Continuity Plan (BCP) is only as good as its implementation and regular review. Without consistent testing and updates, the plan quickly becomes outdated and ineffective, failing to provide the necessary guidance during a crisis. Regular testing and maintenance are crucial for ensuring the BCP remains a relevant and reliable tool for business resilience.
Regular testing and review of the BCP are vital for several reasons. Firstly, it identifies weaknesses and gaps in the plan, allowing for proactive adjustments before a real-world crisis occurs. Secondly, it ensures that all employees are familiar with their roles and responsibilities during a disruption. Finally, it provides valuable data for continuous improvement, enhancing the plan’s effectiveness over time. A robust testing program is essential for verifying the plan’s feasibility and ensuring its alignment with the evolving business environment.
BCP Test Types
Different types of tests cater to various needs and resource levels. Choosing the appropriate test type depends on factors like the complexity of the plan, available resources, and the level of detail required.
- Tabletop Exercises: These involve a facilitated discussion among key personnel, walking through various scenarios and identifying potential challenges and solutions. They are relatively low-cost and can be conducted frequently to address specific aspects of the plan.
- Functional Exercises: These involve testing specific functions or processes within the BCP, such as data backup and recovery or communication protocols. They provide a more practical assessment of the plan’s effectiveness in handling specific critical functions.
- Full-Scale Simulations: These are comprehensive tests that involve a large-scale simulation of a disaster scenario. They are the most resource-intensive but offer the most realistic assessment of the plan’s effectiveness. This approach often involves multiple departments and simulates a complete disruption, including relocation to an alternate site.
BCP Testing and Review Schedule
A structured schedule ensures consistent monitoring and improvement. The frequency of testing should be proportionate to the risk level and the criticality of the business functions covered by the plan.
| Date | Activity |
|---|---|
| Q1 2024 | Tabletop Exercise: Focus on Communication Protocols |
| Q2 2024 | Functional Exercise: Data Backup and Recovery |
| Q3 2024 | Review and Update BCP based on previous test results and business changes |
| Q4 2024 | Tabletop Exercise: Focus on Alternate Site Operations |
| Q1 2025 | Full-Scale Simulation (Partial) – focusing on IT infrastructure recovery |
Updating the BCP
After each test, a thorough analysis of the results is crucial. This involves identifying areas where the plan performed well, as well as areas needing improvement. Documentation of these findings is essential for informing subsequent updates. Changes in the business environment, such as mergers, acquisitions, or significant technological advancements, also necessitate BCP revisions. The update process should involve relevant stakeholders and follow a documented change management process to ensure the plan remains accurate, current, and effective. For example, a company experiencing rapid growth might need to update its BCP to reflect the increased number of employees and the expansion of its IT infrastructure. Similarly, a company implementing a new cloud-based system would need to update its BCP to incorporate procedures for accessing and recovering data from the cloud.
Technology and Infrastructure Considerations
Technology plays a crucial role in ensuring business continuity. A robust technological infrastructure is essential for maintaining operations during disruptions, enabling rapid recovery, and minimizing downtime. Effective strategies must encompass data protection, system resilience, and disaster recovery planning.
Effective business continuity relies heavily on a well-planned and resilient technological infrastructure. This includes not only the hardware and software but also the processes and procedures for managing and protecting them. Failure to adequately address technology and infrastructure can severely impact recovery time and potentially lead to irreversible business losses.
Data Backup and Recovery Strategies
Data is the lifeblood of most businesses. Therefore, implementing a comprehensive data backup and recovery strategy is paramount. This involves regular backups, utilizing multiple backup locations (on-site and off-site), and employing robust data recovery procedures. Testing the recovery process is crucial to ensure its effectiveness.
A robust data backup strategy should consider various factors, including the frequency of backups, the types of data backed up (critical vs. non-critical), the storage medium used (tape, disk, cloud), and the recovery time objective (RTO) and recovery point objective (RPO). For example, a financial institution might require near real-time backups with minimal RTO and RPO, whereas a small retail business might have a more relaxed schedule. Off-site backups are essential to protect against physical damage to the primary location.
Disaster Recovery Solutions
Disaster recovery solutions are designed to restore business operations after a significant disruption. These solutions can range from simple failover systems to complex, geographically dispersed data centers. The choice of solution depends on the organization’s size, criticality of operations, and risk tolerance.
Examples of disaster recovery solutions include:
- Failover systems: These automatically switch operations to a backup system in case of failure. A simple example is a mirrored server setup where one server takes over if the primary server fails.
- Cloud-based solutions: Cloud providers offer various disaster recovery services, including data replication, virtual machine backups, and disaster recovery-as-a-service (DRaaS). This allows for quick recovery by utilizing resources in a geographically separate data center.
- Hot site: A fully equipped backup facility that can be immediately operational. This is a costly option but offers the fastest recovery time.
- Cold site: A facility with basic infrastructure that needs to be equipped before becoming operational. This is a more affordable option but requires more time to become operational.
Ensuring IT Infrastructure Resilience
Building a resilient IT infrastructure requires a multi-faceted approach. This includes redundancy in hardware and software, robust network security, regular system maintenance, and comprehensive disaster recovery planning. Furthermore, a well-defined incident response plan is vital for addressing and resolving IT-related disruptions effectively.
Key aspects of ensuring IT infrastructure resilience include:
- Redundancy: Implementing redundant systems, such as multiple servers, network connections, and power supplies, ensures continued operation even if one component fails.
- Network security: Robust security measures, including firewalls, intrusion detection systems, and regular security audits, protect against cyberattacks and data breaches that can disrupt operations.
- Regular maintenance: Proactive maintenance, including software updates, hardware upgrades, and system backups, helps prevent failures and maintain optimal performance.
- Disaster recovery planning: A comprehensive disaster recovery plan Artikels procedures for recovering from various disruptions, including natural disasters, cyberattacks, and equipment failures.
Legal and Regulatory Compliance
Maintaining legal and regulatory compliance is paramount in any business continuity plan (BCP). Failure to comply can result in significant financial penalties, reputational damage, and even legal action. A robust BCP must proactively address these requirements to minimize risk and ensure the organization’s continued operation during and after a disruptive event.
Legal and regulatory requirements related to business continuity vary significantly depending on industry, location, and the specific nature of the business. Understanding these obligations is crucial for developing an effective and compliant BCP. Non-compliance can lead to severe consequences, highlighting the importance of a proactive and comprehensive approach.
Relevant Legal and Regulatory Frameworks
Many legal and regulatory frameworks impact business continuity. These vary by industry and geographical location. For example, financial institutions are subject to stringent regulations regarding data security and operational resilience, while healthcare providers must adhere to HIPAA regulations in the United States regarding patient data privacy. Understanding these specific regulations is crucial for effective compliance.
Importance of Compliance
Compliance with relevant legal and regulatory requirements is not merely a matter of avoiding penalties; it’s a fundamental aspect of responsible business practice. It demonstrates a commitment to protecting stakeholders’ interests, including customers, employees, and investors. A compliant BCP fosters trust and enhances the organization’s reputation, contributing to long-term sustainability and success. Non-compliance, on the other hand, can lead to significant financial losses, legal challenges, and irreparable damage to brand image.
Best Practices for Ensuring Compliance
Implementing best practices ensures ongoing compliance. This involves regularly reviewing and updating the BCP to reflect changes in legislation and regulatory guidance. Regular audits and assessments help identify potential gaps and ensure the plan remains effective and compliant. Training employees on relevant regulations and their roles in the BCP is also crucial. Finally, maintaining thorough documentation of compliance efforts provides a verifiable record of adherence to legal and regulatory requirements. This proactive approach safeguards the organization from potential legal and financial risks.
Integrating Legal and Regulatory Considerations into the BCP
Integrating legal and regulatory considerations into the BCP is a crucial step in developing a comprehensive and compliant plan. This involves identifying all applicable laws and regulations, assessing potential risks associated with non-compliance, and developing strategies to mitigate those risks. The BCP should clearly Artikel the organization’s responsibilities under these regulations and the procedures for ensuring compliance during and after a disruptive event. This integrated approach ensures that the BCP not only addresses operational continuity but also legal and regulatory obligations. For instance, a BCP for a financial institution might include specific procedures for maintaining data security and regulatory reporting during a system outage, ensuring compliance with relevant financial regulations. Similarly, a healthcare provider’s BCP would incorporate protocols for maintaining patient data privacy and compliance with HIPAA regulations during an emergency.
Conclusion
Developing a comprehensive Business Continuity Plan is a crucial investment in your organization’s future. By proactively identifying and mitigating risks, establishing clear recovery strategies, and implementing regular testing procedures, you can significantly reduce the impact of disruptions and ensure business continuity. This guide provides a solid foundation for building a resilient organization capable of weathering any storm. Remember, a well-executed BCP isn’t just about surviving a crisis; it’s about thriving through it.
Common Queries
What is the difference between RTO and RPO?
RTO (Recovery Time Objective) is the maximum acceptable downtime after a disruption. RPO (Recovery Point Objective) is the maximum acceptable data loss after a disruption.
How often should my BCP be tested?
The frequency of testing depends on your risk profile and industry regulations, but at least an annual review and tabletop exercise are recommended.
Who should be involved in creating a BCP?
A cross-functional team representing various departments, including IT, operations, finance, and legal, should be involved.
What are some common pitfalls to avoid when creating a BCP?
Common pitfalls include unrealistic RTOs/RPOs, insufficient testing, lack of management support, and failing to regularly update the plan.