Risk Management Framework Examples: Prepare yourself for a delightful deep dive into the wonderfully wacky world of risk management! We’ll explore the frameworks that help businesses (and even slightly disorganized individuals) navigate the treacherous terrain of potential problems. Think of it as a thrilling adventure, but instead of battling dragons, we’re battling… spreadsheets. (Almost as exciting, right?)
This exploration will cover various frameworks, including the internationally renowned ISO 31000, the digitally-focused NIST Cybersecurity Framework, and the comprehensive COSO ERM. We’ll examine their core principles, implementation steps, and real-world applications across diverse industries like healthcare, finance, and manufacturing. Buckle up, it’s going to be a wild (but informative) ride!
Introduction to Risk Management Frameworks
Let’s face it, navigating the treacherous waters of business without a proper risk management framework is like sailing a bathtub in a hurricane – exhilarating, perhaps, but ultimately disastrous. A robust framework isn’t just a good idea; it’s the difference between weathering the storm and becoming a very soggy statistic.
A risk management framework provides a structured and consistent approach to identifying, assessing, and responding to risks that could impact an organization’s objectives. Think of it as a detailed map charting the potential hazards on your journey to success, allowing you to anticipate obstacles and plan alternative routes before you’re stranded on the side of the road with a flat tire (and no spare).
Importance of a Robust Risk Management Framework
A strong risk management framework is vital for several reasons. Firstly, it enhances decision-making by providing a clear understanding of potential threats and opportunities. Secondly, it improves resource allocation, ensuring that resources are focused on mitigating the most significant risks. Finally, a robust framework fosters a culture of proactive risk awareness, empowering employees at all levels to identify and report potential issues before they escalate into full-blown crises. Imagine the peace of mind!
Key Benefits of Implementing a Risk Management Framework
Implementing a risk management framework offers numerous advantages. Three key benefits include: improved decision-making, leading to more strategic and effective choices; increased efficiency, by focusing resources on the most critical risks; and enhanced reputation and stakeholder confidence, demonstrating a commitment to responsible risk management. These benefits can translate to a healthier bottom line and a more secure future.
Types of Risk Management Frameworks
Various risk management frameworks exist, each with its own strengths and weaknesses. Some popular examples include COSO (Committee of Sponsoring Organizations of the Treadway Commission), ISO 31000 (International Organization for Standardization), and NIST Cybersecurity Framework. COSO focuses on enterprise-wide risk management, while ISO 31000 offers a more general approach applicable across various sectors. The NIST framework, as its name suggests, specializes in cybersecurity risks. Choosing the right framework depends on the specific needs and context of the organization. Selecting the wrong framework is like choosing a tiny umbrella in a monsoon – it’s not going to cut it.
Examples of Risk Management Frameworks: Risk Management Framework Examples
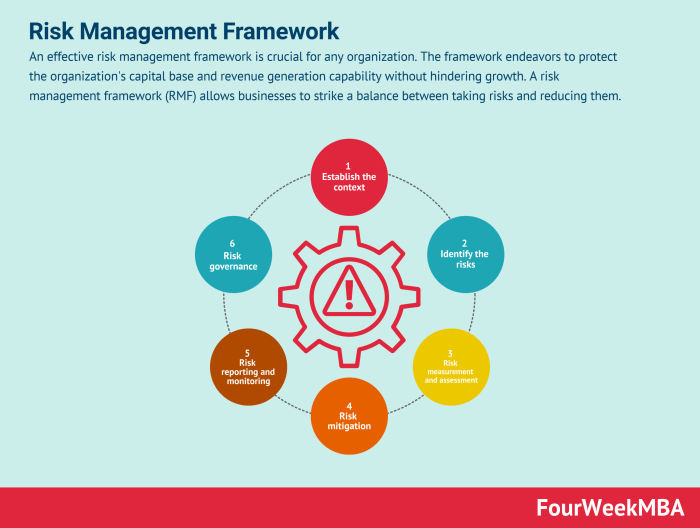
Embarking on the thrilling journey of risk management can feel like navigating a minefield blindfolded – unless you have a trusty framework to guide you. These frameworks provide a structured approach, transforming the daunting task of risk assessment into a manageable, even… dare we say, enjoyable, process. Let’s delve into the world of risk management frameworks, starting with a heavyweight contender: ISO 31000.
ISO 31000 Core Principles
ISO 31000 isn’t just another set of guidelines; it’s a philosophical masterpiece disguised as a risk management standard. Its core principles aren’t just suggestions; they’re the bedrock upon which effective risk management is built. Think of them as the secret ingredients to a delicious risk-mitigation cake (don’t worry, no actual baking is required). These principles emphasize a proactive, integrated approach, ensuring that risk management is woven into the fabric of an organization, rather than being a tacked-on afterthought. They promote a holistic view, considering the interconnectedness of various risks and their potential impact. Ignoring these principles is like trying to build a house on a foundation of jelly – it’s a recipe for disaster.
Implementing ISO 31000: A Step-by-Step Guide (Almost)
Implementing ISO 31000 is a journey, not a sprint. It requires a structured approach, involving careful planning and execution. While the standard doesn’t prescribe a rigid, one-size-fits-all process, it suggests a series of steps to guide organizations through the implementation process. These steps involve establishing the context, identifying risks, analyzing and evaluating risks, treating risks, monitoring and reviewing risks, and communicating and consulting. It’s like assembling a complex Lego castle – each step is crucial, and skipping one can lead to a wobbly tower of impending doom.
Comparison of ISO 31000 with Other Frameworks
ISO 31000 isn’t the only sheriff in town. Other frameworks, such as the NIST Cybersecurity Framework and COSO ERM, offer their own unique approaches to risk management. While they share some common ground, their focus and methodologies differ significantly. Think of them as different tools in a risk management toolbox – each has its strengths and weaknesses, and the best choice depends on the specific needs of the organization. Choosing the wrong tool is like trying to hammer in a screw – it might eventually work, but it’ll be inefficient and frustrating.
Comparison Table: ISO 31000, NIST Cybersecurity Framework, and COSO ERM
| Feature | ISO 31000 | NIST Cybersecurity Framework | COSO ERM |
|---|---|---|---|
| Focus | Broad risk management | Cybersecurity risk management | Enterprise risk management |
| Scope | All types of organizations and risks | Organizations in the digital space | Entire organization and its operations |
| Methodology | Principles-based approach | Framework-based approach with five functions (Identify, Protect, Detect, Respond, Recover) | Component-based approach with eight components |
| Implementation | Flexible and adaptable | Structured and prescriptive | Comprehensive and detailed |
Examples of Risk Management Frameworks: Risk Management Framework Examples
The world of risk management is a thrilling rollercoaster, a dizzying blend of potential disaster and triumphant mitigation. One of the most celebrated (and frankly, quite useful) frameworks for navigating this thrilling ride is the NIST Cybersecurity Framework. It’s not just for the tech-savvy; it’s for anyone who understands the vital importance of protecting their digital assets – which, let’s be honest, is pretty much everyone these days.
NIST Cybersecurity Framework: The Five Functions
The NIST Cybersecurity Framework (CSF) is a voluntary framework, meaning it’s a helpful guide, not a legally binding set of rules. Think of it as a well-organized toolbox, packed with the right instruments to handle various cybersecurity challenges. Its core structure rests on five interconnected functions: Identify, Protect, Detect, Respond, and Recover. These functions aren’t sequential steps; they operate concurrently, creating a dynamic and robust defense system. Imagine them as a highly coordinated superhero team, each member with a unique but essential role.
- Identify: This involves understanding your organization’s assets, their value, and the associated risks. It’s like taking inventory of your digital kingdom, noting what’s valuable and what’s vulnerable. A thorough inventory might reveal a weakness in your network’s defenses, or an outdated software system posing a significant threat.
- Protect: This focuses on developing and implementing safeguards to limit or contain the impact of a cybersecurity event. This is where you build your castle walls – employing access controls, data security measures, and other preventative measures to keep the bad guys out.
- Detect: Here, the focus shifts to identifying the occurrence of a cybersecurity event. Think of this as your early warning system – intrusion detection systems, security information and event management (SIEM) tools, and regular security audits are all part of this crucial function. A prompt detection system allows for quicker response times, minimizing potential damage.
- Respond: This is the action phase – containing the impact of a cybersecurity event, taking actions to reduce damage and limit further harm. This involves having a well-defined incident response plan and a team ready to spring into action. Imagine it as your well-trained fire brigade, ready to extinguish the flames of a cyberattack.
- Recover: This final stage involves restoring any capabilities or services that were impaired due to a cybersecurity incident. It’s about getting back on your feet after the attack – restoring data, rebuilding systems, and learning from the experience to prevent future incidents. Think of it as rebuilding your castle, stronger than before.
Importance of the NIST Cybersecurity Framework in a Digital Environment, Risk Management Framework Examples
In today’s hyper-connected world, where data breaches are becoming increasingly sophisticated and frequent, a robust cybersecurity framework is not a luxury; it’s a necessity. The NIST CSF provides a structured approach to managing cybersecurity risks, enabling organizations to align their efforts with industry best practices and regulatory requirements. Its flexibility allows organizations of all sizes and across various sectors to adapt it to their specific needs, making it a truly versatile tool in the fight against cyber threats. Consider the recent surge in ransomware attacks – a well-implemented NIST CSF can significantly reduce the likelihood and impact of such events.
Challenges in Implementing the NIST Cybersecurity Framework
Implementing the NIST CSF, while beneficial, isn’t without its challenges.
- Resource Constraints: Implementing the framework requires significant investment in personnel, technology, and training. Many smaller organizations might struggle with the financial burden, potentially hindering their ability to fully adopt the framework.
- Lack of Skilled Personnel: The successful implementation of the NIST CSF demands a workforce with the necessary skills and expertise. A shortage of cybersecurity professionals can make it difficult to find and retain the talent needed to effectively manage and implement the framework.
- Keeping Up with Evolving Threats: The cybersecurity landscape is constantly evolving, with new threats and vulnerabilities emerging regularly. Maintaining a framework that keeps pace with these changes requires continuous monitoring, updates, and adaptations, posing a significant ongoing challenge.
Best Practices for Successful Implementation of the NIST Cybersecurity Framework
Successful implementation hinges on a strategic and phased approach.
- Start Small, Think Big: Begin by focusing on a specific area or function of the framework, gradually expanding as you gain experience and resources. This phased approach minimizes disruption and allows for a more manageable implementation process.
- Prioritize and Focus: Identify your organization’s most critical assets and focus your efforts on protecting them first. Prioritization ensures that resources are allocated effectively and that the most significant risks are addressed.
- Regularly Assess and Update: The NIST CSF is not a “set it and forget it” solution. Regular assessments and updates are crucial to ensure that the framework remains effective in the face of evolving threats. Regular audits and security testing should be a cornerstone of your ongoing efforts.
- Foster a Culture of Security: Successful implementation relies on the buy-in and participation of everyone within the organization. A strong security culture, where security is viewed as a shared responsibility, is essential for long-term success. Regular training and awareness programs are crucial in this endeavor.
Examples of Risk Management Frameworks: Risk Management Framework Examples
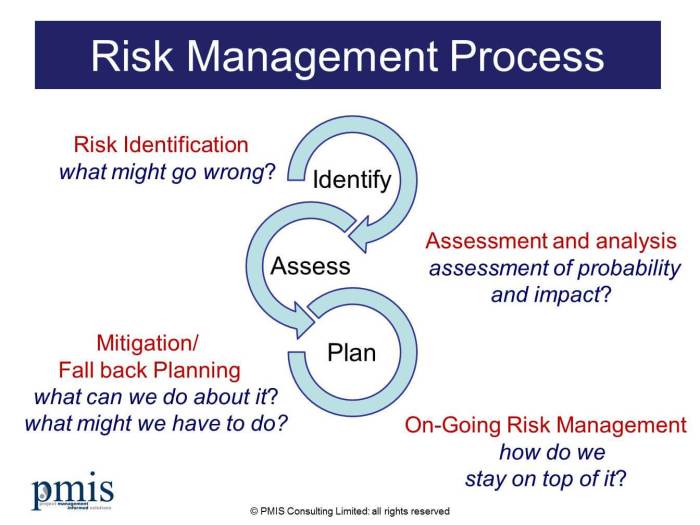
Let’s delve into the wonderfully complex world of risk management frameworks. Think of them as the instruction manuals for keeping your enterprise from turning into a spectacular, albeit expensive, firework display. One of the most prominent and widely adopted frameworks is the COSO Enterprise Risk Management (ERM) framework. It’s not just for accountants hiding in dimly lit offices; it’s a tool for everyone from the CEO to the intern who accidentally deleted the entire marketing campaign.
COSO ERM Framework Components
The COSO ERM framework, in its glorious complexity, provides a comprehensive approach to managing risks. It’s less about avoiding risk altogether (because let’s face it, that’s impossible) and more about identifying, assessing, and responding to risks in a way that aligns with an organization’s objectives. Think of it as a sophisticated game of risk-wrestling, where you strategically maneuver to minimize damage.
The Eight Components of the COSO ERM Framework and Their Interrelationships
The COSO framework is built upon eight interconnected components, each playing a crucial role in the overall risk management process. These components aren’t independent islands; they’re more like cogs in a well-oiled (hopefully) machine. If one component falters, the entire system can grind to a halt.
- Internal Environment: This sets the tone at the top. It’s about ethics, integrity, and the overall culture of risk awareness. A strong internal environment is like having a well-trained security guard at the front door – it deters trouble before it even starts. Think of a company with a strong code of conduct versus one where questionable practices are commonplace. The former is much better equipped to handle risks.
- Objective Setting: Before you can manage risk, you need to know what you’re trying to achieve. Clearly defined objectives provide a framework for identifying and prioritizing risks that could derail your plans. It’s like setting a destination on your GPS – you need to know where you’re going before you can figure out the best route to avoid traffic jams (risks).
- Event Identification: This involves identifying both internal and external events that could impact the achievement of objectives. This isn’t just about the obvious threats; it’s about thinking outside the box and considering even the most unlikely scenarios. Think about a pandemic, a sudden change in government regulations, or a rogue intern with a penchant for deleting files.
- Risk Assessment: This is where you analyze the likelihood and impact of identified events. It involves determining the inherent risk (the risk before any responses are in place) and the residual risk (the risk after responses are implemented). This is about assigning probabilities and consequences to each identified event.
- Risk Response: This component involves selecting and implementing strategies to address identified risks. Options include avoiding, reducing, sharing, or accepting the risk. This is where you decide whether to build a fortress (avoidance), install a better alarm system (reduction), get insurance (sharing), or simply accept the risk of a minor scratch (acceptance).
- Control Activities: These are the actions established through policies and procedures to help ensure that risk responses are effectively carried out. Think of these as the practical steps taken to implement the risk responses. These are the security cameras, the fire drills, the regular software updates – the nuts and bolts of risk mitigation.
- Information and Communication: Effective communication is crucial. This component emphasizes the importance of sharing risk-related information throughout the organization. This is about ensuring everyone is on the same page and understands their role in managing risk. It’s the company-wide email chain, the regular risk management meetings, and the readily available risk assessment reports.
- Monitoring Activities: This is about regularly assessing the effectiveness of the risk management process. It involves tracking key risk indicators, conducting audits, and making necessary adjustments. This is about ongoing evaluation and improvement; it’s the continuous feedback loop that keeps the system functioning optimally.
COSO ERM Framework Application Across Industries
The COSO ERM framework is incredibly versatile. It can be adapted to fit the unique risk profiles of various industries. A bank faces different risks than a tech startup, and a hospital faces different risks than a manufacturing plant. The framework provides the adaptable structure; the specifics are tailored to the context. For example, a bank might focus heavily on credit risk and fraud, while a tech startup might prioritize cybersecurity and intellectual property protection.
Assessing and Mitigating Risks Using the COSO ERM Framework
Implementing the COSO ERM framework involves a systematic approach. It begins with defining objectives, identifying potential events, assessing their likelihood and impact, and then developing and implementing appropriate responses. Regular monitoring and communication are essential to ensure the effectiveness of the chosen strategies. This iterative process allows organizations to continuously adapt to changing circumstances and minimize potential disruptions. For instance, a company facing supply chain disruptions might use the framework to identify alternative suppliers, negotiate better contracts, or build up inventory reserves.
Risk Management Framework Examples in Specific Industries
The world of risk management is a thrilling rollercoaster, a dizzying blend of calculated gambles and strategic maneuvers. While the core principles remain consistent, the specific frameworks employed vary wildly depending on the industry, reflecting the unique challenges and potential pitfalls of each sector. Let’s delve into the fascinating, and sometimes frankly terrifying, world of risk management in three distinct industries.
The implementation of a robust risk management framework is crucial for any organization seeking to navigate the complex and often unpredictable landscape of modern business. Failing to adequately address potential risks can lead to significant financial losses, reputational damage, and even legal repercussions. Therefore, tailoring the framework to the specific needs and vulnerabilities of the industry is paramount.
Risk Management Frameworks in Healthcare
The healthcare industry, a delicate dance between life and death, faces unique challenges. Patient safety, regulatory compliance, and the ever-evolving technological landscape all contribute to a complex risk profile. Effective risk management is not just good practice; it’s a moral imperative.
- The Joint Commission’s accreditation standards: These standards require healthcare organizations to establish comprehensive risk management programs, focusing on patient safety, quality of care, and operational efficiency. Think of it as the industry’s gold standard, a rigorous checklist ensuring a minimum level of safety.
- ISO 31000: This international standard provides a flexible framework adaptable to various healthcare settings, guiding organizations in identifying, assessing, and treating risks related to patient care, operations, and compliance. It’s a global best practice, offering a universally understood language for risk management.
- NIST Cybersecurity Framework: Given the increasing reliance on electronic health records and interconnected systems, cybersecurity is paramount. This framework helps healthcare organizations manage and mitigate cybersecurity risks, protecting sensitive patient data and maintaining operational integrity. Think of it as a digital fortress, safeguarding valuable information.
Risk Management Frameworks in Financial Services
The financial services industry operates in a high-stakes environment, where even minor missteps can have cascading effects. Robust risk management is not just desirable; it’s essential for maintaining stability and protecting stakeholders’ interests. A single bad bet can bring down the house, so careful planning is critical.
- Basel Accords: These international agreements set minimum capital requirements for banks, aiming to prevent financial crises by ensuring banks have enough capital to absorb potential losses. Think of it as a global insurance policy for the financial system.
- Solvency II: Similar to Basel Accords but specifically for insurance companies, this regulatory framework aims to ensure insurers have sufficient capital to meet their obligations. It’s a safety net, designed to protect policyholders.
- COSO Framework: This widely adopted internal control framework helps financial institutions identify and manage risks related to financial reporting, operations, and compliance. It’s a comprehensive internal check, ensuring accountability and transparency.
Risk Management Frameworks in Manufacturing
Manufacturing, with its complex supply chains and intricate processes, faces risks ranging from equipment malfunctions to supply chain disruptions. Effective risk management is crucial for maintaining operational efficiency, product quality, and worker safety. It’s a balancing act, aiming for maximum output while minimizing hazards.
- ISO 9001: This quality management system standard helps manufacturing organizations identify and manage risks related to product quality, customer satisfaction, and operational efficiency. It’s a badge of quality, signifying a commitment to excellence.
- ISO 14001: This environmental management system standard guides manufacturers in identifying and mitigating environmental risks, such as pollution and waste disposal. It’s a green initiative, aiming for sustainable manufacturing practices.
- OSHA guidelines: Occupational Safety and Health Administration guidelines provide a framework for managing workplace hazards, ensuring worker safety and reducing the risk of accidents. It’s a life-saver, prioritizing employee well-being.
Differences in Risk Management Approaches Across Industries
While the fundamental principles of risk management remain consistent across industries, the specific approaches and priorities vary significantly. Healthcare prioritizes patient safety and regulatory compliance, while finance focuses on financial stability and regulatory adherence. Manufacturing emphasizes operational efficiency, product quality, and worker safety. Each industry tailors its risk management strategy to its unique challenges and vulnerabilities, highlighting the importance of a context-specific approach.
Illustrative Example: A Hypothetical Risk Management Plan

Let’s imagine a charming little bakery, “Crumbs of Delight,” run by the wonderfully optimistic (but slightly disorganized) Beatrice. Beatrice’s biggest worry isn’t burnt croissants; it’s the potential for a devastating fire in her kitchen. This isn’t just a case of slightly singed pastries; we’re talking a full-blown inferno, capable of wiping out her business overnight. This scenario provides a perfect, albeit slightly smoky, example of how a risk management plan can save the day (and the bakery).
Risk Identification and Assessment
Identifying the fire risk is the first, and arguably most crucial, step. Beatrice, armed with a newfound appreciation for risk management, meticulously lists potential fire hazards: faulty wiring, overloaded electrical outlets, unattended ovens, and even the occasional rogue stray spark from the whimsical gas oven. She then assesses the likelihood of each hazard causing a fire and the potential severity of the resulting damage. For example, faulty wiring is deemed highly likely (given the age of the building) and capable of causing significant damage, while a stray spark is less likely but still potentially catastrophic. This assessment helps prioritize which risks require immediate attention.
Risk Response Strategies
Now that the risks are identified and assessed, it’s time for action! Beatrice implements several risk response strategies. For the high-likelihood, high-impact risk of faulty wiring, she invests in a professional electrical inspection and necessary repairs. For the less likely but still significant risk of oven mishaps, she implements a strict protocol for oven usage and temperature monitoring, including regular maintenance checks. She also installs a state-of-the-art fire suppression system – a slightly extravagant but undeniably effective solution. These proactive measures significantly reduce the likelihood and impact of a fire.
Monitoring and Review
Beatrice doesn’t stop at implementation; she actively monitors the effectiveness of her risk management plan. She schedules regular inspections of electrical systems and oven maintenance. She also ensures her staff is adequately trained on fire safety procedures. The effectiveness of the plan is measured through key metrics such as the number of near misses, the cost of preventative maintenance, and employee satisfaction with safety protocols. Regular review allows her to adapt and improve the plan as needed, ensuring it remains relevant and effective in mitigating fire risks.
Consequences of Not Implementing a Risk Management Plan
Without a plan, Beatrice faces a catastrophic scenario. A fire could destroy her bakery, resulting in significant financial losses, potential injuries, and the heartbreaking loss of her beloved business. Insurance might cover some losses, but it wouldn’t replace the emotional toll or the time and effort required to rebuild. The lack of a proactive approach could have devastating consequences.
Key Performance Indicators (KPIs) for Monitoring
Several key metrics will be used to monitor the effectiveness of the plan. These include: the frequency of safety inspections, the number of fire safety training sessions conducted, the cost of preventative maintenance (electrical repairs, oven servicing, etc.), the number of near-miss incidents, and employee feedback on safety protocols. These KPIs provide a quantifiable measure of the plan’s success in mitigating fire risks and ensuring the safety of both staff and the business. Tracking these metrics allows Beatrice to make data-driven adjustments and improvements to her risk management plan, keeping Crumbs of Delight safe and delicious for years to come.
Tools and Techniques for Risk Management
Embarking on the thrilling adventure of risk management requires more than just a crystal ball and a lucky rabbit’s foot (though those certainly wouldn’t hurt!). A robust arsenal of tools and techniques is essential to navigate the treacherous terrain of potential pitfalls and emerge victorious. Let’s delve into the practical side of predicting and preventing the unexpected, shall we?
Qualitative and Quantitative Risk Assessment Methods
Risk assessment isn’t just about gut feelings; it’s about employing systematic methods to understand the likelihood and impact of potential risks. Qualitative methods, such as brainstorming sessions and expert interviews, offer a valuable, albeit subjective, insight into the nature of the risks. Quantitative methods, on the other hand, use numerical data to assign probabilities and potential financial losses to each risk. This often involves sophisticated statistical models, but don’t worry, we’ll keep it relatively painless.
For example, a qualitative assessment might involve a team discussing potential risks to a new product launch, assigning labels like “high,” “medium,” or “low” to the likelihood and impact of each risk. A quantitative approach might involve calculating the expected monetary value (EMV) of each risk using probabilities and financial projections. For instance, if there’s a 20% chance of a supply chain disruption costing $100,000, the EMV is $20,000 (0.20 * $100,000).
Risk Registers and Heat Maps
Once you’ve identified your risks, it’s time to organize them. Think of the risk register as your meticulously maintained risk filing cabinet, detailing each risk’s description, likelihood, impact, owner, and planned mitigation strategies. A heat map, on the other hand, provides a visual representation of your risks, plotting them on a grid based on likelihood and impact. It’s like a risk-themed game of Battleship, but instead of sinking ships, you’re conquering risks.
Imagine a heat map where the x-axis represents likelihood and the y-axis represents impact. Risks with high likelihood and high impact would be plotted in the top right corner, highlighting their urgent need for attention. Risks in the bottom left corner might be relatively benign and require less immediate action.
Risk Mitigation Strategies
Facing a risk head-on doesn’t always mean a head-on collision. We have a variety of strategic options at our disposal. Risk avoidance involves steering clear of the risky activity altogether – sometimes the best defense is a good offense (or avoidance, in this case). Risk reduction aims to minimize the likelihood or impact of the risk through preventative measures. Risk transfer involves shifting the risk to another party, like an insurance company. Finally, risk acceptance means acknowledging the risk and deciding to live with the potential consequences. This might seem reckless, but sometimes it’s the most practical approach, especially for low-impact risks.
For example, a company might avoid launching a product in a politically unstable region (avoidance), invest in robust security systems to reduce the likelihood of cyberattacks (reduction), purchase insurance to cover potential lawsuits (transfer), or accept the small risk of minor equipment malfunctions (acceptance).
Using KPIs to Monitor and Evaluate Risk Management Effectiveness
You’ve built your risk management fortress, but how do you know it’s working? Key Performance Indicators (KPIs) are your trusty sentinels, providing continuous monitoring of your risk management efforts. KPIs can include the number of risks identified, the number of risks mitigated, the cost of risk mitigation, and the number of incidents related to identified risks. Regularly reviewing these KPIs ensures that your risk management strategy is effective and adaptable to changing circumstances.
For example, a company might track the number of security breaches as a KPI. A decrease in this number would suggest that the implemented security measures are effective. Conversely, an increase would indicate a need to re-evaluate and enhance the risk management strategy. It’s all about continuous improvement, folks!
Wrap-Up
So, there you have it – a whirlwind tour through the fascinating (and frankly, slightly nerdy) world of risk management frameworks. While the specifics of each framework differ, the underlying principle remains the same: proactive planning and mitigation are key to avoiding disaster. Whether you’re a seasoned risk management professional or a curious beginner, understanding these frameworks is crucial in navigating the unpredictable landscape of modern business. Now go forth and mitigate! (Responsibly, of course.)
FAQ Guide
What’s the difference between qualitative and quantitative risk assessment?
Qualitative assessment uses descriptive terms (high, medium, low) to gauge risk likelihood and impact, while quantitative assessment uses numerical data and statistical methods for a more precise evaluation.
Can I use multiple risk management frameworks simultaneously?
Absolutely! Many organizations blend elements from different frameworks to create a customized approach tailored to their specific needs and risk profile. It’s like a delicious risk management cocktail – the right mix can be incredibly effective!
What if my business is too small for a formal risk management framework?
Even small businesses benefit from basic risk management. Start with a simple risk register, identify key threats, and develop basic mitigation plans. It’s better to be slightly prepared than completely unprepared!



