Know-Your-Customer Requirements Review: Navigating the labyrinthine world of KYC compliance can feel like a thrilling escape room, filled with puzzles, regulations, and the ever-present threat of penalties. This comprehensive guide will illuminate the path, transforming the daunting task of KYC review into a manageable and even… dare we say… enjoyable process. We’ll unravel the intricacies of data collection, verification methods, and risk mitigation, equipping you with the knowledge to not only meet compliance standards but also enhance the customer experience.
From defining core KYC components and understanding the legal landscape to mastering data security and streamlining the customer journey, this guide provides a practical, step-by-step approach. We’ll explore real-world examples across various industries, highlighting best practices and potential pitfalls. Get ready to conquer the KYC challenge!
Defining Know-Your-Customer (KYC) Requirements
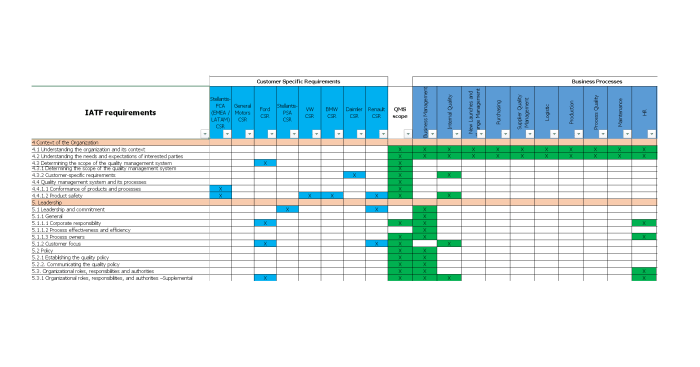
Knowing your customer isn’t just good manners; it’s the bedrock of responsible business practices, especially in sectors dealing with sensitive information and financial transactions. Failing to adequately implement KYC procedures can lead to hefty fines, reputational damage, and even criminal prosecution – not exactly the recipe for a successful business venture. Let’s delve into the fascinating world of KYC requirements.
Core Components of Effective KYC Requirements
Effective KYC hinges on a robust, multi-faceted approach. It’s not a one-size-fits-all solution; the specific requirements will vary depending on the industry and the level of risk involved. However, some common threads weave through most effective KYC programs. These typically involve collecting, verifying, and monitoring customer information, ensuring ongoing compliance with relevant regulations. This includes identifying the customer, verifying their identity using reliable sources, and understanding the nature of their business relationships. Think of it as a thorough background check, but with significantly more paperwork (and less intrigue).
Legal and Regulatory Frameworks Influencing KYC
The legal landscape governing KYC is, shall we say, rather…extensive. Different jurisdictions have different rules, and these rules are often updated to keep pace with evolving threats and technologies. Key regulations often include the Bank Secrecy Act (BSA) in the United States, the Anti-Money Laundering (AML) Directives in the European Union, and similar legislation in countries worldwide. These regulations aim to prevent financial crimes such as money laundering, terrorist financing, and fraud. Navigating this regulatory maze requires dedicated compliance teams and a healthy dose of caffeine.
Examples of KYC Requirements Across Various Industries
The KYC requirements vary wildly depending on the industry. Financial institutions, for instance, face significantly stricter regulations than, say, a small online bookstore. Banks are required to conduct extensive due diligence, including background checks, credit history reviews, and ongoing monitoring of transactions. In contrast, an e-commerce business might only require basic information like name and address verification, perhaps with additional checks for high-value transactions. The key difference lies in the level of risk associated with each industry and the potential for misuse of their services.
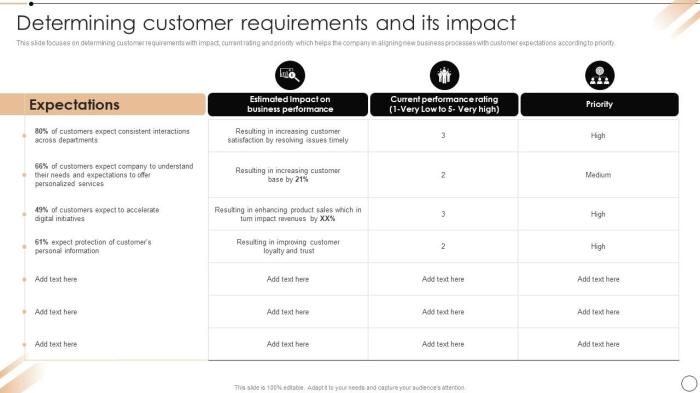
Comparison of KYC Requirements: Financial Institutions vs. E-commerce Businesses
| Requirement | Financial Institution | E-commerce Business | Notes |
|---|---|---|---|
| Customer Identification | Rigorous verification using multiple sources (passport, driver’s license, utility bills etc.) | Basic verification using name and address; potentially email verification | Level of verification directly correlates with risk assessment |
| Source of Funds | Extensive documentation required to trace the origin of funds | Generally not required unless transaction flags raise suspicion | High-value transactions may trigger additional scrutiny |
| Ongoing Monitoring | Continuous monitoring of transactions for suspicious activity | Typically limited to fraud detection systems and review of high-risk transactions | Frequency of monitoring depends on risk assessment |
| Record Keeping | Comprehensive record-keeping requirements for a minimum of 5-10 years | Record-keeping requirements vary depending on jurisdiction and transaction volume | Retention periods are subject to regulatory requirements |
The KYC Review Process
Ah, the KYC Review Process – a thrilling adventure into the world of compliance! Think of it as a meticulous treasure hunt, where the treasure is a confident understanding of your customer’s identity, and the pitfalls are… well, hefty fines. Let’s embark on this exciting journey, shall we?
A thorough KYC review is more than just ticking boxes; it’s a strategic dance between compliance and common sense. It’s about proactively identifying and mitigating risks, not just reactively patching holes after the fact. This process is vital for maintaining a healthy business reputation and avoiding regulatory headaches that could make a migraine seem like a pleasant afternoon nap.
Step-by-Step Guide for Conducting a Thorough KYC Requirements Review
Let’s break down this exhilarating process into manageable steps, each one as crucial as the last. Think of it as assembling a highly complex, yet utterly satisfying, piece of Lego – one wrong move, and you’re staring down the barrel of a regulatory gun.
- Document Collection and Verification: This involves gathering all necessary identification documents (passports, driver’s licenses, utility bills – the whole shebang!) and verifying their authenticity. Think of this as a detective’s meticulous examination of clues.
- Data Validation and Consistency Checks: Cross-referencing information from different sources is key. Inconsistencies? That’s your red flag waving frantically in the wind. Investigate immediately!
- Risk Assessment and Scoring: This is where the real fun begins. We assess the customer’s risk profile, considering factors like their geographic location, business activities, and transaction history. It’s like playing a game of risk assessment poker, and the stakes are high.
- Sanctions and PEP Screening: We check against sanctions lists and Politically Exposed Persons (PEPs) databases to ensure our customer isn’t accidentally funding a rogue nation or a particularly flamboyant dictator. Think of this as a background check on steroids.
- Ongoing Monitoring: The KYC process doesn’t end after the initial review. Ongoing monitoring is essential to catch any changes in a customer’s risk profile. It’s like keeping a watchful eye on your investments – constant vigilance is key.
The Importance of Risk Assessment in KYC Reviews
Risk assessment isn’t just a box to tick; it’s the beating heart of the KYC review process. It’s the compass guiding us through the murky waters of compliance. A robust risk assessment allows us to prioritize our efforts and allocate resources effectively, ensuring that we’re focusing on the customers who pose the greatest risk. Think of it as strategic triage in a compliance emergency room.
For example, a customer engaging in high-value transactions from a high-risk jurisdiction will require a much more thorough review than a customer making small, regular transactions from a low-risk location. This allows for proportionate effort and resource allocation.
Potential Weaknesses in Existing KYC Processes
Even the most robust KYC processes can have vulnerabilities. These weaknesses, if left unaddressed, can lead to significant compliance issues. Think of it as a fortress with weak points in the walls – an easy target for those with malicious intent.
- Insufficient Due Diligence: Rushing the process or cutting corners can lead to missed red flags and increased risk.
- Outdated Technology: Using outdated systems can make it difficult to keep up with evolving regulations and identify emerging threats. Think of this as fighting a modern war with medieval weapons.
- Lack of Training: Employees who lack proper training may not be able to identify suspicious activity or conduct thorough reviews.
- Ineffective Monitoring: Failing to monitor customer activity on an ongoing basis can allow risky behavior to go undetected.
Flowchart Illustrating the KYC Review Process
Imagine a flowchart as a visual map guiding you through the KYC review process. Each decision point is a fork in the road, leading you either to further investigation or a successful completion of the review. This flowchart helps ensure a consistent and thorough review for every customer.
The flowchart would begin with “Customer Application Received”. This would branch into “Collect Required Documentation” and “Initial Risk Assessment”. The risk assessment would lead to either “Low Risk – Proceed to Onboarding” or “High Risk – Enhanced Due Diligence”. The “Enhanced Due Diligence” path would involve additional checks and documentation before proceeding to onboarding. Finally, both paths converge at “Customer Onboarding Complete”. Each decision point would be clearly marked, and the flowchart would visually represent the entire process in a clear and concise manner.
Data Collection and Verification Methods

Ah, data collection – the thrilling pursuit of knowing your customer! It’s less Indiana Jones and more meticulously cross-referencing spreadsheets, but equally vital for keeping your business on the right side of the law (and avoiding those pesky fines that could fund a small nation’s vacation). This section delves into the fascinating world of gathering and verifying customer information, a process as delicate as a soufflé and as crucial as a well-placed comma in a legal document.
Gathering the necessary data for KYC compliance is a multifaceted process, requiring a blend of technology and human judgment. The methods used will vary depending on the risk profile of the customer and the regulatory environment. The goal is to balance efficiency with accuracy, a tightrope walk indeed.
Customer Data Collection Methods
Several methods exist for collecting customer data, each with its own strengths and weaknesses. These methods often work in concert to create a comprehensive profile.
The most common methods include:
- Online Forms: Simple, efficient, and readily available. These forms allow customers to input their information directly, but require robust validation to ensure data accuracy.
- In-Person Applications: Allow for immediate verification of identity documents and signatures. This method, while time-consuming, can provide a high degree of assurance.
- Third-Party Data Providers: These services offer pre-verified data, saving time and resources. However, reliance on external providers necessitates careful due diligence to ensure data quality and security.
Data Verification Techniques
Once collected, data must be rigorously verified. This is where the fun (and the serious legal stuff) really begins.
Various techniques exist to confirm the veracity of customer information. These methods range from simple checks to sophisticated algorithms.
- Identity Document Verification: Comparing submitted documents against government databases. This often involves optical character recognition (OCR) and biometric analysis to detect forgeries.
- Address Verification: Cross-referencing provided addresses with postal databases to confirm accuracy and residency. This helps prevent fraudsters from using false addresses.
- Credit Bureau Checks: Accessing credit reports to verify financial history and identity. This method is subject to strict privacy regulations and requires explicit customer consent.
- Biometric Authentication: Utilizing fingerprints, facial recognition, or voice patterns for identification. This adds a layer of security, but raises privacy concerns that must be addressed thoughtfully.
Best Practices for Data Accuracy and Integrity
Maintaining data accuracy and integrity is paramount. Think of it as your KYC reputation’s life raft.
Implementing the following best practices is crucial:
- Data Validation Rules: Implementing strict rules to ensure data conforms to expected formats and ranges. For example, rejecting phone numbers with incorrect length or invalid characters.
- Regular Data Audits: Conducting periodic audits to identify and correct inaccuracies. This helps maintain data quality and prevent future issues.
- Data Encryption: Protecting data at rest and in transit using strong encryption algorithms. This helps prevent unauthorized access and data breaches.
- Access Control: Limiting access to sensitive customer data to authorized personnel only. This reduces the risk of internal breaches and misuse of information.
Secure Storage and Management of Customer Data
Safeguarding customer data is not just a best practice; it’s a legal and ethical imperative. Think of it as building a high-security vault for your most precious assets (your customer data).
Secure storage and management involves:
- Data Masking: Protecting sensitive data by replacing certain characters with asterisks or other symbols, while retaining data usability for legitimate purposes.
- Data Retention Policies: Establishing clear guidelines for how long customer data should be stored, considering both legal and business requirements. This helps prevent unnecessary data accumulation and potential security risks.
- Regular Security Assessments: Conducting regular vulnerability assessments and penetration testing to identify and address potential security weaknesses. This proactive approach minimizes the risk of data breaches.
Addressing KYC Challenges and Risks
Ah, the thrilling world of KYC! While ensuring compliance might seem like navigating a minefield of regulations, the real challenge lies in the unexpected explosions – the quirks and complexities that can trip up even the most seasoned compliance officer. Let’s delve into the exciting (yes, exciting!) world of KYC challenges and how to defuse those ticking time bombs.
The reality is that KYC isn’t just about ticking boxes; it’s about building a robust system that’s both effective and efficient. Failing to do so can lead to significant repercussions, ranging from hefty fines to reputational damage that could make your company’s stock price plummet faster than a lead balloon.
Common Challenges Encountered During KYC Reviews
Navigating the KYC landscape is often like trying to assemble flat-pack furniture with only half the instructions – frustrating and potentially disastrous. Common hurdles include incomplete or inaccurate data provided by customers, difficulties verifying identities in certain jurisdictions (think of trying to verify someone’s identity in a remote Himalayan village!), and the ever-evolving regulatory landscape that keeps shifting like sand dunes in a desert storm. Maintaining up-to-date knowledge and adapting to changes are critical. Furthermore, managing the sheer volume of data involved can be overwhelming, especially for businesses dealing with a large number of clients. Finally, integrating KYC processes with existing systems can prove to be a technological headache.
Potential Risks Associated with Inadequate KYC Procedures
Inadequate KYC procedures are a recipe for disaster. Think of it as leaving your front door unlocked – inviting trouble in. The risks are numerous and potentially devastating. These include financial crimes such as money laundering and terrorist financing, which can lead to significant financial penalties and irreparable damage to a company’s reputation. Failure to comply with regulations can result in hefty fines and legal repercussions, potentially impacting the business’s viability. Moreover, inadequate KYC can expose a company to reputational damage, eroding customer trust and leading to a loss of business. In the age of social media, negative publicity can spread like wildfire, potentially causing irreparable harm. Finally, failing to identify high-risk customers could lead to losses through fraud or other criminal activities.
Strategies for Mitigating KYC-Related Risks
Thankfully, we’re not entirely at the mercy of KYC chaos. Implementing robust strategies can significantly reduce risks. This includes leveraging advanced technologies like AI and machine learning for efficient data analysis and identity verification. Investing in comprehensive training programs for staff on KYC procedures and best practices is essential. Regular audits and reviews of KYC processes are crucial to identify and address weaknesses. Furthermore, establishing clear escalation procedures for handling suspicious activity is vital. Collaborating with other financial institutions and sharing information (where legally permissible) can enhance the overall effectiveness of KYC efforts. Finally, staying abreast of regulatory changes and adapting processes accordingly is paramount to maintaining compliance.
Responding to KYC Violations or Breaches
Let’s face it: despite our best efforts, KYC violations or breaches can still occur. When they do, a well-defined response plan is essential. This includes promptly reporting violations to the relevant authorities, conducting a thorough internal investigation to determine the root cause of the breach, and implementing corrective measures to prevent future occurrences. Communicating transparently with affected customers and stakeholders is crucial to maintaining trust and minimizing reputational damage. Finally, documenting all aspects of the incident, including the investigation, corrective actions, and lessons learned, is crucial for continuous improvement. Remember, a well-defined response plan is not just about damage control; it’s about demonstrating a commitment to compliance and ethical business practices.
KYC and Customer Experience: Know-Your-Customer Requirements Review
Let’s face it: nobody enjoys filling out endless forms. But KYC compliance is a necessary evil, a bit like flossing – nobody *loves* it, but neglecting it leads to far bigger problems. The challenge, then, is to transform this necessary evil into something… less evil. The key is to find the sweet spot between robust security and a genuinely positive customer experience.
Balancing KYC compliance with a positive customer experience requires a delicate dance. It’s about minimizing friction without compromising security. Think of it as a tightrope walk, where one wrong step could send your customers (and your business) tumbling. The good news is that with careful planning and smart technology, you can successfully navigate this precarious path and even impress your customers in the process.
Streamlining the KYC Process to Minimize Customer Friction
Streamlining the KYC process involves identifying and eliminating unnecessary steps, leveraging technology to automate tasks, and employing user-friendly interfaces. Imagine the difference between filling out a multi-page paper form with illegible handwriting instructions versus a slick, intuitive online application that guides you through each step with clear, concise explanations and helpful prompts. The latter is significantly less likely to induce customer rage, or at least a mild headache. This could involve using pre-filled forms where possible, integrating with existing databases to avoid redundant data entry, and providing real-time feedback to customers during the process. The aim is to make the process as smooth and efficient as possible, making customers feel valued and respected, rather than treated like suspects in a high-stakes heist.
Examples of User-Friendly KYC Onboarding Experiences
A user-friendly KYC onboarding experience might involve a simple, visually appealing interface with clear instructions, progress indicators, and readily available customer support. Imagine a process that uses facial recognition technology, allowing customers to verify their identity quickly and securely with a simple selfie. Or perhaps a system that integrates with existing government databases, automatically verifying information without requiring manual input. Another example is a system that allows customers to upload documents through a secure portal, receiving immediate feedback on whether the documents are acceptable. These features, when combined, contribute to a smoother, more efficient, and less frustrating KYC onboarding experience.
Best Practices for Communicating KYC Requirements to Customers
Effective communication is crucial for managing customer expectations and ensuring compliance. Before launching into the intricacies of KYC, it’s vital to provide a clear and concise explanation of why these measures are necessary. Transparency is key – let customers know that these steps are designed to protect their own financial security and the integrity of the platform. This could involve a series of short, easily digestible videos, interactive FAQs, or even a fun, animated explainer that demystifies the process. The goal is to build trust and make customers feel informed and in control, rather than feeling like they’re navigating a bureaucratic maze. Using plain language, avoiding jargon, and offering multiple channels for support (email, phone, chat) all contribute to a positive customer experience. Think of it as explaining the need for a security system to your family – it’s not fun, but it’s essential for peace of mind.
Ongoing Monitoring and Improvement
KYC compliance isn’t a “set it and forget it” kind of thing. Think of it more like a mischievous pet ferret – constantly needing attention, prone to unexpected escapes (regulatory changes!), and requiring regular training (process improvements). Ongoing monitoring and improvement are crucial for maintaining compliance and mitigating risks. Ignoring this vital aspect is like leaving that ferret unsupervised with your tax returns – chaos will ensue.
Ongoing KYC monitoring ensures your processes remain effective and up-to-date, preventing costly fines and reputational damage. Adapting to the ever-shifting regulatory landscape is a necessity, not an option. Imagine trying to navigate a minefield blindfolded – exhilarating, perhaps, but definitely not recommended for your business’s long-term health. Regular reviews and improvements are the defibrillator that keeps your KYC program alive and kicking.
KYC Monitoring Methods and Frequency
Regular monitoring involves actively reviewing KYC data, transaction patterns, and the effectiveness of your implemented processes. This isn’t a once-a-year check-up; think more along the lines of a diligent personal trainer – constant observation and adjustments. The frequency of monitoring depends on factors such as risk appetite, regulatory requirements, and the nature of your business. For high-risk businesses, daily monitoring might be necessary. For others, a weekly or monthly review might suffice. The key is consistency and a proactive approach. Consider using automated systems to flag potential issues and streamline the review process. This is particularly important when dealing with large volumes of data. Imagine trying to manually sift through mountains of paperwork – the sheer tedium would drive anyone to madness!
Adapting to Changing Regulatory Landscapes
Regulatory changes are inevitable. Think of it as the fashion industry for compliance – constantly evolving, sometimes baffling, and always requiring you to stay on top of the latest trends. To stay ahead, you need a robust system for tracking regulatory updates. This might involve subscribing to legal news services, attending industry conferences, and actively engaging with regulatory bodies. Once a change is identified, you need a swift and well-defined process for adapting your KYC procedures. This process should involve reviewing the impact of the change, updating your policies and procedures, retraining staff, and conducting a thorough assessment of your systems to ensure continued compliance. Failing to adapt is like wearing last year’s fashion – it might have worked then, but it’s outdated and potentially embarrassing now.
Key Performance Indicators (KPIs) for KYC Effectiveness
Measuring the effectiveness of your KYC program is crucial for demonstrating compliance and identifying areas for improvement. Here are some key performance indicators to consider:
- KYC process completion time: How long does it take to complete the KYC process for a new customer? A shorter completion time indicates efficiency.
- Number of KYC exceptions: How many cases require manual review or additional investigation? A high number of exceptions suggests potential weaknesses in your automated systems.
- Customer onboarding success rate: What percentage of customers successfully complete the KYC process? A low success rate may indicate process complexities or friction.
- Percentage of high-risk customers identified: How effective is your system at identifying high-risk customers? A high percentage indicates improved risk management.
- Cost per KYC process: What is the average cost of completing the KYC process for a single customer? Reducing this cost is always a good aim.
Regularly tracking these KPIs will help you identify trends, assess the effectiveness of your processes, and make data-driven improvements.
System for Regularly Reviewing and Improving KYC Processes
A structured approach to reviewing and improving your KYC processes is essential. This should involve regular meetings, thorough documentation, and a feedback mechanism. Consider establishing a dedicated KYC committee to oversee the process. This committee should be responsible for reviewing KPIs, identifying areas for improvement, and proposing solutions. They should also be responsible for keeping abreast of regulatory changes and ensuring that your KYC program remains up-to-date and effective. This systematic approach is like having a well-oiled machine – efficient, effective, and less prone to breakdowns. Regular audits, both internal and external, can provide an independent assessment of your KYC program’s effectiveness and compliance.
Illustrative Examples of KYC Requirements

KYC requirements, while seemingly straightforward, can be surprisingly nuanced and wildly different depending on the industry. Think of it as a game of regulatory whack-a-mole, where the rules change depending on the specific mole (industry) you’re trying to whack. Let’s delve into the wonderfully weird world of KYC across diverse sectors.
KYC Requirements in the Finance Industry
The financial industry, the heavyweight champion of KYC, demands a rigorous approach. Think multiple forms of identification, proof of address, and potentially even background checks. The stakes are high – we’re talking about people’s hard-earned money, after all. A lack of robust KYC can lead to money laundering, terrorist financing, and other nefarious activities. It’s a serious business, and the penalties for non-compliance are equally serious. Banks and other financial institutions typically require a combination of government-issued identification (passport, driver’s license), proof of address (utility bill, bank statement), and potentially source-of-funds documentation, particularly for larger transactions. These requirements are designed to verify the customer’s identity and ensure the legitimacy of their financial activities. The level of scrutiny increases significantly for high-net-worth individuals and those involved in international transactions.
KYC Requirements in the Gaming Industry
The gaming industry, while seemingly less high-stakes than finance, still has its own set of KYC hurdles. Online casinos and gaming platforms must comply with anti-money laundering (AML) regulations and prevent underage gambling. This usually involves verifying the age and identity of players through document verification, and often includes geolocation checks to ensure players are located where they claim to be. Transaction monitoring is also crucial, looking for unusual betting patterns that could indicate money laundering or other illicit activities. The penalties for failing to comply with KYC regulations in the gaming industry can include hefty fines and even license revocation. Think of it as a high-stakes poker game where the regulator is always watching your hand.
KYC Requirements in the Healthcare Industry
The healthcare industry, surprisingly, also has a significant KYC component, although it focuses less on financial transactions and more on patient identity and data protection. Accurate patient identification is crucial for preventing medical errors, ensuring proper billing, and protecting patient privacy. This typically involves verifying patient identity through government-issued IDs and potentially using biometric data like fingerprints. Healthcare providers also need to comply with regulations like HIPAA in the US, which sets strict standards for protecting patient health information. Failure to comply with KYC regulations in healthcare can result in fines, reputational damage, and potential legal action. It’s a matter of life, or at least, accurate medical records.
Visual Representation of a Customer Onboarding Process with Strong KYC Measures
Imagine a flowchart. The process begins with a customer initiating account creation. The next step is a clear, prominent section labeled “Identity Verification.” This section branches out to show various methods: uploading a government-issued ID, taking a selfie for facial recognition, and potentially providing additional documents like a utility bill. Each verification method has a separate box indicating success or failure. Successful verification leads to the next step: “Address Verification,” which follows a similar branching structure. Finally, after successful identity and address verification, the customer proceeds to account creation and activation. The flowchart clearly indicates that failure at any point in the verification process will halt the onboarding and require further action from the customer. The overall visual emphasizes the sequential and rigorous nature of the KYC process.
Scenario of KYC Process Failure, Know-Your-Customer Requirements Review
Imagine an online bank fails to properly verify the identity of a customer who opens an account using fraudulent documents. This customer then uses the account to launder money obtained through illegal activities. The bank, due to its inadequate KYC procedures, faces significant financial penalties, reputational damage, and potential legal action. The consequences can range from hefty fines to complete business closure, demonstrating the critical importance of robust KYC processes.
End of Discussion

Successfully navigating Know-Your-Customer requirements isn’t just about ticking boxes; it’s about building trust, mitigating risk, and providing a seamless customer experience. By understanding the intricacies of KYC compliance and implementing robust processes, businesses can protect themselves from legal repercussions, enhance their reputation, and foster stronger relationships with their clients. This journey, while challenging, ultimately empowers businesses to operate with confidence and integrity in today’s complex regulatory environment. So, embrace the challenge, and watch your KYC compliance soar!
FAQ
What happens if I fail a KYC review?
Failure can lead to hefty fines, reputational damage, and even business closure depending on the severity and jurisdiction. It’s best to avoid this by proactively implementing robust KYC procedures.
Can I outsource my KYC procedures?
Yes, many companies specialize in KYC compliance services. However, remember you remain ultimately responsible for ensuring compliance.
How often should I review my KYC processes?
Regular reviews are crucial, ideally at least annually, or more frequently if regulatory changes occur or significant business shifts happen.
What are some common KYC red flags?
Inconsistencies in provided information, suspicious transaction patterns, and a lack of verifiable documentation are all red flags.