The intricate world of finance often hides illicit activities, and combating them requires a robust framework. Anti-Money Laundering (AML) regulations are the cornerstone of this fight, designed to prevent criminals from disguising illegally obtained funds as legitimate income. Understanding these regulations is crucial for businesses and individuals alike, ensuring compliance and contributing to a safer financial ecosystem.
This guide delves into the complexities of AML, exploring its core principles, implementation strategies, and the consequences of non-compliance. We’ll examine various jurisdictions’ approaches, highlighting key differences in legislation and enforcement. Furthermore, we’ll dissect crucial elements like Customer Due Diligence (CDD), transaction monitoring, sanctions compliance, and the evolving role of technology in AML efforts.
Definition and Scope of Anti-Money Laundering (AML) Regulations

Anti-Money Laundering (AML) regulations are a complex web of laws and guidelines designed to prevent criminals from disguising illegally obtained funds as legitimate income. These regulations target the financial system, aiming to disrupt the flow of illicit money and weaken the financial infrastructure that supports criminal activities. The ultimate goal is to protect the integrity of the global financial system and deter criminal behavior.
AML regulations are built upon several core principles. Firstly, they mandate the identification and verification of customers (Know Your Customer or KYC). This involves collecting sufficient information to confirm the identity of individuals and entities engaging in financial transactions. Secondly, suspicious activity reporting (SAR) is a crucial element, requiring financial institutions to report any transactions that appear suspicious or potentially linked to money laundering or terrorist financing. Thirdly, record-keeping requirements ensure that detailed records of transactions are maintained for a specified period, allowing for auditing and investigation. Finally, compliance programs are essential; financial institutions must establish and maintain robust internal controls and procedures to effectively manage AML risks.
Objectives of AML Compliance Programs
The objectives of AML compliance programs are multifaceted. They aim to prevent the institution from being used to facilitate money laundering or terrorist financing, mitigate the risk of reputational damage and potential legal penalties associated with AML violations, and contribute to the broader effort of combating financial crime globally. A successful AML program involves ongoing risk assessments, employee training, independent audits, and a culture of compliance within the organization. The program’s effectiveness is regularly reviewed and updated to adapt to evolving threats and regulatory changes.
Comparison of AML Regulations Across Jurisdictions
AML regulations vary significantly across jurisdictions, reflecting differences in legal systems, risk profiles, and enforcement priorities. While the core principles remain consistent, the specific requirements, thresholds, and penalties differ substantially. For example, the United States, the United Kingdom, and the European Union each have distinct legislative frameworks and enforcement mechanisms.
| Jurisdiction | Key Legislation | Reporting Thresholds | Penalties for Non-Compliance |
|---|---|---|---|
| United States | Bank Secrecy Act (BSA), USA PATRIOT Act | Varies depending on the type of transaction and institution; generally, transactions exceeding $10,000 must be reported. | Significant fines, criminal charges, and potential imprisonment for individuals and institutions. |
| United Kingdom | Proceeds of Crime Act 2002, Money Laundering Regulations 2017 | Varies depending on the type of transaction and institution; generally, transactions exceeding £15,000 may trigger reporting requirements. | Significant fines, criminal charges, and potential imprisonment for individuals and institutions. The Financial Conduct Authority (FCA) has enforcement powers. |
| European Union | Fifth Anti-Money Laundering Directive (AMLD5) | Thresholds vary across member states but generally align with international standards. Focus is increasingly on risk-based approaches rather than fixed thresholds. | Significant fines and other sanctions vary across member states, but generally reflect the seriousness of the offense. National competent authorities enforce the legislation. |
Customer Due Diligence (CDD) Procedures
Customer Due Diligence (CDD) is a crucial component of Anti-Money Laundering (AML) compliance. It involves identifying and verifying the identity of customers to prevent them from being used for illicit financial activities. Robust CDD procedures are essential for financial institutions to mitigate risks and comply with regulatory requirements.
Know Your Customer (KYC) Process
The Know Your Customer (KYC) process is the foundation of CDD. It aims to understand the customer’s identity, business activities, and risk profile. This involves collecting, verifying, and maintaining information about the customer throughout their relationship with the financial institution. Failure to adequately perform KYC checks can lead to significant penalties.
Components of the KYC Process
The KYC process typically involves several key components. These include collecting identifying information such as name, address, date of birth, and proof of identity (e.g., passport, driver’s license). Verification of this information against reliable sources is also critical. Additionally, understanding the customer’s source of funds and the purpose of the account are essential aspects of a thorough KYC process. Ongoing monitoring of the customer’s activity is also necessary to identify any suspicious transactions or changes in their risk profile.
Enhanced Due Diligence for High-Risk Customers
Enhanced Due Diligence (EDD) is applied to customers deemed to be high-risk. These customers may include politically exposed persons (PEPs), individuals residing in high-risk jurisdictions, or those involved in high-risk activities such as international trade or cash-intensive businesses. EDD involves more stringent identification and verification procedures, more frequent monitoring, and a higher level of scrutiny of transactions. For example, EDD might require additional documentation to prove the source of funds or more frequent reviews of the customer’s account activity.
Customer Onboarding and AML Checks Flowchart
The following describes a simplified flowchart illustrating the steps involved in customer onboarding and AML checks.
1. Customer Application: The customer submits an application for an account or service.
2. Identity Verification: The institution verifies the customer’s identity using appropriate documentation.
3. Risk Assessment: The institution assesses the customer’s risk profile based on factors such as their occupation, geographic location, and transaction history.
4. CDD Procedures: The institution applies appropriate CDD procedures based on the risk assessment. This may include enhanced due diligence for high-risk customers.
5. Account Opening: If the AML checks are satisfactory, the account is opened.
6. Ongoing Monitoring: The institution continuously monitors the customer’s activity for suspicious transactions.
7. Suspicious Activity Report (SAR): If suspicious activity is detected, a SAR is filed with the relevant authorities.
Examples of Red Flags Indicating Potential Money Laundering Activities
Several red flags can indicate potential money laundering activities. These include unusually large cash deposits, complex or unusual transaction patterns, transactions involving shell companies or anonymous accounts, and a sudden increase in account activity. Another example is a customer attempting to structure transactions to avoid detection, breaking down a large sum of money into smaller amounts to avoid reporting thresholds. Furthermore, a significant discrepancy between declared income and the funds deposited can also be a red flag. Finally, a customer’s refusal to provide information requested during the KYC process should be treated as a serious red flag.
Transaction Monitoring and Reporting

Effective transaction monitoring and reporting are crucial components of a robust anti-money laundering (AML) program. These processes aim to identify suspicious activity indicative of money laundering or terrorist financing, allowing for timely intervention and reporting to the relevant authorities. This involves analyzing financial transactions to detect unusual patterns and promptly filing Suspicious Activity Reports (SARs) when necessary.
Transaction monitoring systems analyze large volumes of data to identify potentially suspicious transactions. These systems employ various methods to detect anomalies, including rule-based systems, anomaly detection algorithms, and network analysis techniques. Rule-based systems flag transactions that meet pre-defined criteria, such as exceeding a certain threshold or involving high-risk jurisdictions. Anomaly detection algorithms identify unusual patterns that deviate from established baselines, while network analysis techniques visualize relationships between accounts and transactions to uncover hidden connections.
Methods for Detecting Suspicious Transactions
Several methods are employed to detect suspicious transactions. These include setting thresholds for transaction values, monitoring unusual transaction frequencies, identifying unusual transaction patterns across multiple accounts, and analyzing relationships between individuals and entities involved in transactions. For instance, a sudden increase in deposits from numerous small accounts into a single account could be flagged. Similarly, frequent wire transfers to high-risk countries or jurisdictions known for money laundering activities would trigger further investigation. The use of complex layering techniques, involving multiple transactions to obscure the origin of funds, is another key indicator.
Suspicious Activity Report (SAR) Filing Process
Filing a SAR involves a structured process that typically includes documenting the suspicious activity, gathering supporting evidence, and submitting the report to the relevant financial intelligence unit (FIU). The process begins with the identification of a potentially suspicious transaction or pattern. This is followed by a thorough investigation to gather sufficient evidence to support the filing of a SAR. The SAR itself usually contains detailed information about the suspicious activity, the involved parties, and the reasons for suspicion. The FIU then reviews the SAR and may initiate further investigations or share the information with other agencies. Failure to file a SAR when required can result in significant penalties.
Examples of Suspicious Transaction Patterns
Several transaction patterns can raise red flags. These include structuring transactions to avoid reporting thresholds (e.g., depositing amounts just below the reporting limit multiple times), unusually large or frequent transactions from high-risk countries, transactions involving shell companies or anonymous accounts, and sudden and unexplained increases in account activity. For example, a series of cash deposits just below the reporting threshold, followed by a large wire transfer to an offshore account, would be highly suspicious. Similarly, numerous small transactions from multiple accounts converging into a single account, followed by a large withdrawal, would warrant further scrutiny. These patterns often indicate attempts to conceal the true nature and origin of funds.
The Role of Technology in Transaction Monitoring
Technology plays a pivotal role in enhancing the effectiveness of transaction monitoring. Advanced analytics, machine learning, and artificial intelligence (AI) are increasingly being used to analyze vast datasets, identify complex patterns, and improve the accuracy of suspicious activity detection. These technologies can process large volumes of data far more efficiently than manual review, allowing for the identification of subtle anomalies that might otherwise be missed. AI-powered systems can also adapt and learn over time, improving their ability to identify emerging money laundering techniques. For example, machine learning algorithms can identify unusual relationships between individuals and entities based on their transaction history, even if those relationships are not immediately apparent.
Sanctions Compliance and Screening
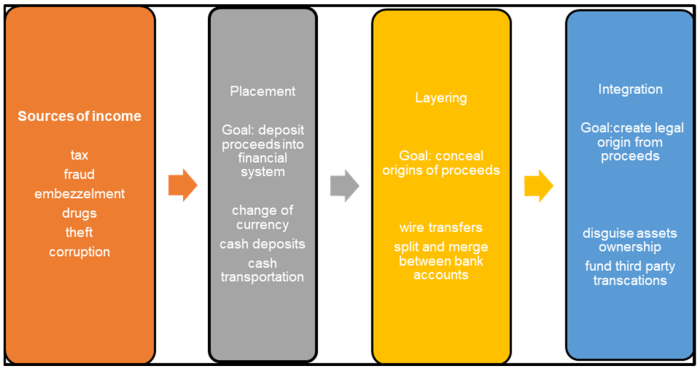
Sanctions compliance is a critical component of any effective anti-money laundering (AML) program. It involves identifying and mitigating the risks associated with conducting business with individuals or entities subject to economic or financial sanctions imposed by various governmental bodies. Failure to comply with sanctions regulations can result in significant financial penalties, reputational damage, and legal repercussions.
Sanctions programs aim to prevent illicit activities, such as terrorism financing and proliferation of weapons of mass destruction, by restricting access to the international financial system for designated individuals and entities. This section will detail the key aspects of sanctions compliance and screening.
Types of Sanctions
Various international organizations and national governments impose sanctions. Prominent examples include those administered by the United Nations (UN), the Office of Foreign Assets Control (OFAC) in the United States, the European Union (EU), and the United Kingdom (UK). UN sanctions often target individuals and entities associated with terrorist groups or those involved in conflicts. OFAC sanctions focus on a broader range of activities, including terrorism, narcotics trafficking, and human rights abuses. EU and UK sanctions mirror many of those imposed by the UN and OFAC, but may also include additional targets specific to their national interests. Each jurisdiction’s sanctions programs have their own unique characteristics, requiring businesses to maintain a comprehensive understanding of all applicable regulations.
Customer and Transaction Screening Process
Screening involves comparing customer data (names, addresses, dates of birth, etc.) and transaction details against sanctions lists maintained by relevant authorities. This process is typically automated using specialized software that continuously updates and compares data against the latest sanctions lists. A “hit” occurs when a match is found between a customer or transaction and a sanctioned entity. Hits require further investigation to determine if the match is a true positive (the customer is indeed sanctioned) or a false positive (a coincidental match due to common names or other factors). This investigation may involve manual review of supporting documentation, and potentially contacting the customer for clarification.
Managing Sanctions-Related Risks
Effective sanctions risk management involves a multi-faceted approach. This includes establishing a robust sanctions compliance program, regularly updating sanctions lists, and implementing thorough training for employees. Developing clear internal policies and procedures is crucial. These policies should define the responsibilities of different personnel, Artikel the screening process, and establish protocols for handling sanctions hits. Regular audits and independent reviews of the sanctions compliance program are also essential to ensure its effectiveness. Furthermore, implementing a robust system for monitoring transactions and identifying suspicious activity is critical to detect potential sanctions violations.
Best Practices for Sanctions Compliance
A strong sanctions compliance program necessitates a commitment to best practices. These include:
- Regularly updating sanctions lists and screening software to ensure accuracy.
- Implementing a robust customer due diligence (CDD) program to accurately identify and verify customers.
- Conducting thorough due diligence on all high-risk customers and transactions.
- Providing comprehensive training to all employees on sanctions regulations and procedures.
- Developing and maintaining clear internal policies and procedures for handling sanctions-related issues.
- Implementing a system for monitoring and reporting suspicious activity.
- Conducting regular audits and independent reviews of the sanctions compliance program.
- Maintaining accurate records of all sanctions-related activities.
- Developing a clear escalation process for handling sanctions hits and other compliance issues.
- Staying informed about changes in sanctions regulations and best practices.
AML Compliance Program Development and Implementation

A robust Anti-Money Laundering (AML) compliance program is crucial for organizations to mitigate risks and meet regulatory obligations. This program should be a living document, regularly reviewed and updated to reflect changes in legislation, technology, and the organization’s own risk profile. A well-designed program proactively identifies, assesses, and mitigates AML/CFT risks, fostering a culture of compliance throughout the organization.
Framework for a Comprehensive AML Compliance Program
A comprehensive AML compliance program requires a structured framework. This framework should encompass risk assessment, policies and procedures, training, monitoring, and reporting. The program should be tailored to the specific risks faced by the organization, considering factors such as the nature of its business, its customer base, and the geographic locations in which it operates. A clearly defined organizational structure with designated responsibilities ensures accountability and effective implementation. The program should also incorporate a system for regularly reviewing and updating its components to maintain effectiveness.
Key Elements of an Effective AML Compliance Program
Several key elements contribute to an effective AML compliance program. These include a comprehensive risk assessment identifying vulnerabilities and potential threats; clearly defined policies and procedures outlining the organization’s approach to AML compliance; a robust customer due diligence (CDD) program to verify customer identities and monitor transactions; a comprehensive transaction monitoring system capable of identifying suspicious activity; a staff training program designed to equip employees with the knowledge and skills necessary to detect and report suspicious activity; and finally, a system for reporting suspicious activity to the relevant authorities. Regular internal audits and independent reviews ensure the program remains effective and compliant.
AML Compliance Training for Staff
Effective AML compliance training is vital for staff at all levels. Training should be tailored to the roles and responsibilities of employees, providing them with the specific knowledge and skills necessary to perform their duties in compliance with AML regulations. The training should be interactive, engaging, and incorporate real-life scenarios to reinforce learning. Regular refresher training is crucial to maintain awareness of evolving risks and regulations. Training records should be meticulously maintained to demonstrate compliance. Consider using a blended learning approach that incorporates online modules, classroom sessions, and on-the-job training. This ensures diverse learning styles are catered to and knowledge retention is maximized. For example, a bank might use online modules for foundational knowledge, followed by role-playing exercises in a classroom setting to simulate real-world scenarios, and finally, on-the-job shadowing with experienced compliance officers.
Assessing the Effectiveness of an AML Compliance Program
Regular assessment is crucial for ensuring the ongoing effectiveness of an AML compliance program. This assessment should encompass a review of all aspects of the program, including policies and procedures, training, transaction monitoring, and reporting. A checklist can be used to facilitate a systematic review.
| Area | Checklist Item | Pass/Fail |
|---|---|---|
| Risk Assessment | Is a comprehensive risk assessment conducted regularly? | |
| Policies and Procedures | Are AML policies and procedures documented, readily accessible, and regularly reviewed? | |
| Customer Due Diligence (CDD) | Are CDD procedures consistently applied and documented? | |
| Transaction Monitoring | Is the transaction monitoring system effective in identifying suspicious activity? | |
| Sanctions Screening | Is effective sanctions screening conducted on all customers and transactions? | |
| Staff Training | Is regular and effective AML training provided to all relevant staff? | |
| Reporting | Are suspicious activity reports (SARs) filed promptly and accurately? | |
| Auditing | Are regular internal audits and independent reviews conducted? |
Consequences of Non-Compliance
Non-compliance with Anti-Money Laundering (AML) regulations carries severe consequences, impacting organizations financially, legally, and reputationally. The severity of penalties varies depending on factors such as the jurisdiction, the nature and extent of the violation, and the organization’s history of compliance. Understanding these potential ramifications is crucial for effective AML program development and implementation.
Potential Penalties for AML Violations
Penalties for AML violations can be substantial and far-reaching. These penalties are designed to deter illegal activity and hold organizations accountable for failing to prevent money laundering and terrorist financing. Financial penalties can range from significant fines to the forfeiture of assets involved in illicit transactions. In addition to monetary penalties, organizations may face criminal charges, leading to imprisonment for responsible individuals. Regulatory actions may also include license revocations, operational restrictions, and increased regulatory scrutiny. The specific penalties depend heavily on the regulatory body and the severity of the infraction. For example, a small oversight might result in a warning letter, while a deliberate attempt to conceal illicit funds could lead to millions in fines and criminal prosecution.
Reputational Damage Associated with AML Non-Compliance
The reputational damage stemming from AML non-compliance can be devastating. A single violation can severely tarnish an organization’s image, eroding public trust and damaging relationships with clients, partners, and investors. Negative media coverage, public relations crises, and a loss of consumer confidence can all follow an AML violation. This reputational harm can be long-lasting, even after penalties are paid and corrective actions are taken. The impact on brand value and future business opportunities can be significant, making reputation management a critical aspect of AML compliance.
Impact of AML Violations on Business Operations
AML violations can significantly disrupt business operations. Investigations, audits, and legal proceedings can consume considerable time and resources, diverting attention and funds from core business activities. Operational restrictions imposed by regulators can further limit an organization’s ability to conduct business as usual. The loss of clients and partners due to reputational damage can lead to decreased revenue and market share. Furthermore, the cost of remediation, including strengthening AML controls and implementing new compliance measures, can be substantial. In extreme cases, violations can lead to the complete shutdown of business operations.
Examples of Real-World Cases of AML Violations and Their Consequences
Several high-profile cases illustrate the severe consequences of AML non-compliance. For instance, HSBC faced billions of dollars in fines for failing to adequately monitor transactions, allowing money laundering to occur. Similarly, Société Générale was penalized for its involvement in a massive Russian money laundering scheme. These cases demonstrate the significant financial penalties, reputational damage, and operational disruptions that can result from AML violations. These examples highlight the importance of robust AML compliance programs and the serious consequences of neglecting them. The fines imposed and the lasting reputational harm suffered serve as stark warnings to other financial institutions and businesses.
Emerging Trends in AML Regulations and Technology

The landscape of Anti-Money Laundering (AML) compliance is constantly evolving, driven by increasingly sophisticated financial crime techniques and advancements in technology. This necessitates a continuous adaptation of regulatory frameworks and the implementation of innovative technological solutions to maintain effectiveness. This section will explore some of the key emerging trends shaping the future of AML.
Emerging Challenges in AML Compliance
The rise of cryptocurrency, decentralized finance (DeFi), and the proliferation of online payment systems present significant challenges for AML compliance. The anonymity afforded by these platforms makes it difficult to trace the flow of funds and identify beneficial owners. Furthermore, the global nature of these transactions necessitates international cooperation and harmonization of regulations, which can be a complex and time-consuming process. The sheer volume of transactions processed daily by financial institutions also poses a challenge, demanding efficient and scalable compliance solutions. Another significant hurdle is the evolving nature of money laundering techniques themselves, with criminals constantly adapting their methods to circumvent existing controls. This requires a proactive and adaptive approach to AML compliance, leveraging advanced technologies and intelligence to stay ahead of the curve.
The Role of Artificial Intelligence (AI) and Machine Learning (ML) in AML Compliance
AI and ML are revolutionizing AML compliance by automating previously manual and time-consuming processes. These technologies can analyze vast amounts of data far more quickly and efficiently than human analysts, identifying suspicious patterns and transactions that might otherwise be missed. AI-powered systems can analyze transactional data, customer profiles, and other relevant information to flag high-risk activities, prioritize investigations, and enhance the accuracy of risk assessments. Machine learning algorithms can learn from past patterns of suspicious activity, continuously improving their ability to detect new and evolving money laundering schemes. For instance, ML algorithms can be trained to identify unusual transaction patterns, such as unusually large or frequent transactions, or transactions involving known high-risk jurisdictions. This allows compliance teams to focus their resources on the most critical cases, increasing efficiency and effectiveness.
Innovative Technologies Enhancing AML Compliance
Several innovative technologies are being deployed to strengthen AML compliance efforts. RegTech solutions, specifically designed to address regulatory compliance challenges, offer a range of tools, including automated KYC/CDD processes, enhanced transaction monitoring systems, and sophisticated sanctions screening capabilities. Blockchain technology, while sometimes associated with illicit activities, can also be used to enhance transparency and traceability of transactions, making it easier to track the flow of funds and identify suspicious activity. The use of distributed ledger technology (DLT) allows for secure and transparent record-keeping, improving the accuracy and efficiency of AML investigations. Furthermore, advanced data analytics techniques enable financial institutions to gain deeper insights into their customer base and transaction patterns, enabling proactive risk management and more effective detection of money laundering attempts. For example, network analysis techniques can visualize relationships between individuals and entities, revealing hidden connections and potential money laundering schemes.
The Impact of FinTech on AML Regulations
The rapid growth of the FinTech sector has significantly impacted AML regulations. The innovative business models and technologies employed by FinTech companies, while offering numerous benefits, also pose unique challenges for regulators. The decentralized nature of many FinTech platforms makes it difficult to apply traditional AML controls. Regulators are grappling with how to effectively supervise these companies while ensuring that innovation is not stifled. This has led to a greater emphasis on collaborative regulatory approaches and the development of innovative regulatory technologies (RegTech) to address the specific challenges posed by the FinTech sector. The increasing adoption of open banking and APIs also presents new challenges, requiring regulators to develop frameworks that ensure the secure and responsible sharing of financial data while maintaining appropriate AML controls. The focus is shifting towards a risk-based approach, tailoring regulatory requirements to the specific risks posed by different FinTech business models and technologies.
Ending Remarks
Navigating the landscape of Anti-Money Laundering regulations demands vigilance and proactive measures. From robust Customer Due Diligence procedures to sophisticated transaction monitoring systems and a strong understanding of international sanctions, compliance is paramount. By embracing best practices, leveraging technological advancements, and staying abreast of emerging trends, businesses and individuals can contribute to a more secure and transparent financial system, mitigating risks and fostering trust.
Essential FAQs
What is the difference between AML and KYC?
AML (Anti-Money Laundering) refers to the overall regulations and procedures designed to prevent money laundering. KYC (Know Your Customer) is a crucial *part* of AML compliance, focusing on verifying the identity of customers to prevent the use of their accounts for illicit purposes.
How often should AML compliance training be conducted?
The frequency of AML training depends on factors like risk profile and regulatory requirements. However, annual training is generally recommended, with more frequent updates for staff handling high-risk transactions.
What are some examples of red flags in transaction monitoring?
Red flags include unusually large or frequent transactions, transactions involving shell companies or high-risk jurisdictions, and structured transactions designed to avoid detection.
Can small businesses avoid AML compliance?
No. Even small businesses are subject to AML regulations, although the specific requirements might be less stringent than for larger institutions. Ignoring AML compliance exposes them to significant legal and financial risks.



