Bank Account Management System: Imagine a world where your money magically appears and disappears, defying all logic and the laws of physics. Sounds chaotic, right? Thankfully, robust Bank Account Management Systems (BAMS) keep the financial universe from collapsing into a black hole of misplaced funds. These sophisticated systems are the unsung heroes of the banking world, tirelessly tracking every penny, ensuring transactions are secure, and generating reports that would make even the most seasoned accountant weep with joy (or terror, depending on the findings).
This exploration delves into the fascinating world of BAMS, examining its core functionalities, security protocols, transaction processing, reporting capabilities, system integrations, and scalability considerations. We’ll uncover the secrets behind seamless funds transfers, explore the intricate dance of encryption and authentication, and even peek behind the curtain at the data analytics that keep the whole thing running smoothly. Prepare to be amazed (and possibly a little bit bored by the sheer technical brilliance).
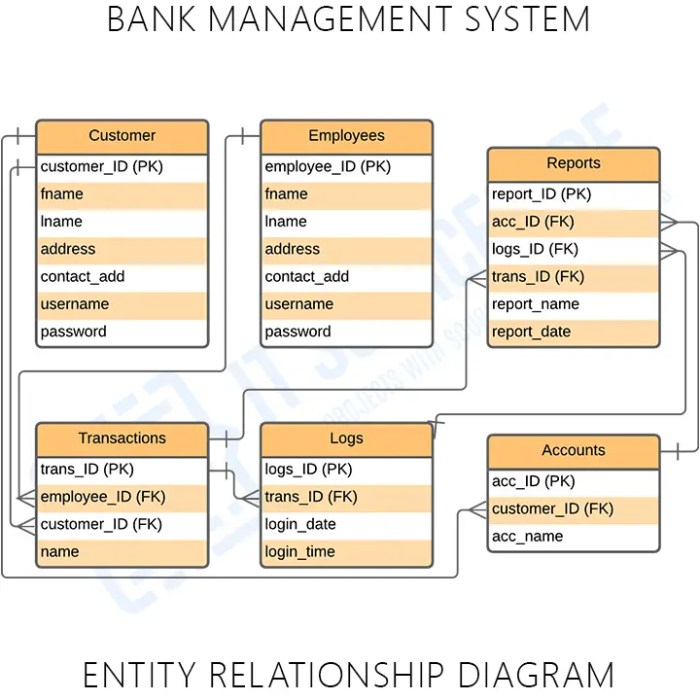
Features of a Bank Account Management System
A Bank Account Management System (BAMS), in its simplest form, is a digital Swiss Army knife for your finances. It’s far more sophisticated than just a glorified checkbook, promising efficiency and (hopefully) a reduction in the number of frantic calls to customer service. Let’s delve into its fascinating, and frankly, slightly addictive features.
Core Functionalities of a Bank Account Management System
A robust BAMS offers a suite of essential functionalities designed to streamline banking activities. These include account opening and closing, deposits and withdrawals (both in-person and electronic), balance inquiries, transaction history viewing, statement generation, and the ability to transfer funds between accounts (both internal and external). The system should also provide secure access controls and robust auditing capabilities to maintain the integrity of financial data. Think of it as a well-organized filing cabinet for your money, except far less dusty.
User Interface Elements for Account Holders
The user interface (UI) for account holders should be intuitive and user-friendly, even for those less tech-savvy (we’ve all been there). Common elements include a personalized dashboard displaying account balances and recent transactions, secure login and authentication mechanisms (hopefully involving more than just a simple password!), a clear and concise menu for navigating different account functionalities, and tools for managing personal information and preferences. Ideally, the system should offer multiple access points – desktop, mobile app, and perhaps even a friendly chatbot.
Administrative Features for Bank Employees
On the other side of the digital coin, bank employees require a powerful administrative interface. This typically includes tools for account creation and management, transaction processing and reconciliation, fraud detection and prevention systems (to keep those pesky digital pickpockets at bay), reporting and analytics capabilities (for identifying trends and optimizing services), and customer relationship management (CRM) features. Essentially, it’s a behind-the-scenes powerhouse keeping everything running smoothly. Imagine it as the control room for a very, very important financial spaceship.
User Flow Diagram for Funds Transfer
A typical funds transfer, say from checking to savings, might follow this flow: User logs in → Selects “Transfer Funds” → Specifies source and destination accounts → Enters transfer amount → Confirms details → System processes the transfer → User receives confirmation. This process should be designed to be secure, transparent, and, dare we say, even enjoyable. A little celebratory confetti animation wouldn’t hurt, right?
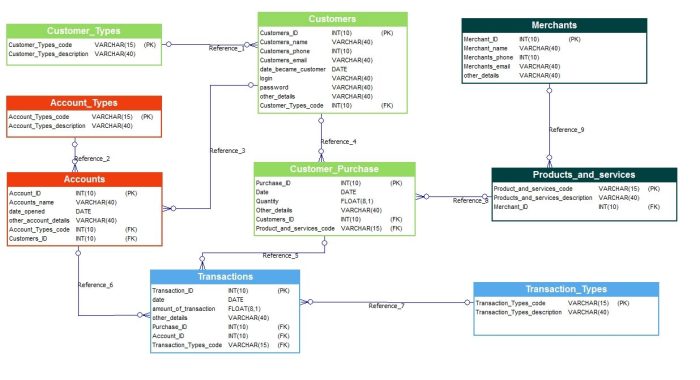
Comparison of Different Bank Account Types
The following table compares various bank account types, highlighting their key features. Remember, the exact features may vary depending on the financial institution.
| Account Type | Interest Rate | Fees | Features |
|---|---|---|---|
| Checking Account | Typically low or none | May include monthly maintenance fees or per-transaction fees | Debit card access, check writing, online banking |
| Savings Account | Generally higher than checking accounts | May include monthly maintenance fees or limited transaction limits | Higher interest rates, limited transactions |
| Money Market Account | Interest rate fluctuates with market conditions | May include higher minimum balance requirements and fees | Higher interest rates than savings accounts, check writing capabilities (sometimes) |
| Certificate of Deposit (CD) | Fixed interest rate for a specified term | Penalties for early withdrawal | Higher interest rates for longer terms, fixed-term investment |
Security Measures in Bank Account Management Systems
Protecting your hard-earned cash from digital bandits requires more than just a good password (though, let’s be honest, a good password is a *great* start!). A robust bank account management system employs a multi-layered security approach, like a digital fortress built by particularly clever squirrels. It’s not just about keeping the money safe, it’s about keeping the *system* safe – a breach in one area could compromise the whole shebang.
Encryption and Authentication in Securing Transactions
Encryption is the secret code your bank uses to scramble your sensitive information during transmission. Think of it as wrapping your money in invisible, unbreakable wrapping paper before sending it across the internet. Without the correct “key,” nobody can decipher the message. Authentication, on the other hand, is the process of verifying your identity before granting access to your account. It’s like the bank’s bouncer, checking your ID before letting you into the VIP area (where your money is, obviously). These two work together like a dynamic duo, ensuring only authorized users can access and manipulate financial data. For example, HTTPS protocol uses encryption (SSL/TLS) to secure communication between your browser and the bank’s server, while passwords and usernames are used for authentication.
Potential Vulnerabilities and Mitigation Strategies
Even the most secure systems have potential weaknesses. Phishing scams, for instance, attempt to trick users into revealing their login credentials. Malware can infect computers and steal sensitive data. SQL injection attacks target database vulnerabilities. To counter these threats, banks employ a variety of mitigation strategies including robust anti-phishing measures, regular security audits, strong firewalls, intrusion detection systems, and employee training programs. Think of it as a well-trained security team constantly patrolling the digital fortress, armed with the latest gadgets and ready to thwart any attempts at infiltration. A real-world example of a successful mitigation strategy is the widespread adoption of multi-factor authentication, making it significantly harder for hackers to gain unauthorized access.
Two-Factor Authentication Implementation
Two-factor authentication (2FA) adds an extra layer of security by requiring two different forms of verification before granting access. One is something you *know* (like your password), and the other is something you *have* (like a one-time code sent to your phone via SMS or a dedicated authentication app). This makes it extremely difficult for even those who have your password to gain access. Imagine trying to open a safe – you need the combination (password) and the key (one-time code). Without both, you’re locked out. The implementation typically involves the user entering their username and password, followed by the successful verification of the second factor. Upon successful verification of both factors, the system grants access to the user’s account. This process is crucial in preventing unauthorized access even if one of the factors is compromised.
Secure Login Attempt Flowchart
Imagine a flowchart depicting the following steps:
1. User enters credentials: The process begins with the user entering their username and password on the login page.
2. System verifies credentials: The system checks the database for a matching username and password.
3. 2FA Triggered: If the credentials match, the system triggers the second factor authentication process (e.g., sends a code to the user’s registered mobile number).
4. User enters 2FA code: The user receives the code and enters it into the designated field.
5. System verifies 2FA code: The system verifies the code against the one sent.
6. Access Granted/Denied: If both factors are verified, the system grants access; otherwise, access is denied, and potentially a lockout mechanism is triggered.
Transaction Processing within the System
Ah, the heart of the banking beast – transaction processing! Where the magic of money movement happens, albeit with significantly less glitter and slightly more regulatory compliance than one might expect from a magical money-making machine. Let’s delve into the surprisingly fascinating world of how your deposits, withdrawals, and interbank transfers actually work.
Deposit Transaction Processing
Processing a deposit is a surprisingly straightforward process, at least from a user’s perspective. The system first verifies the account number and the depositor’s identity, a crucial step to prevent Uncle Barry from accidentally depositing his life savings into your account (though we all secretly hope he does, don’t we?). Once verified, the deposited amount is scanned (or manually entered, for those charmingly old-fashioned institutions), added to the account balance, and a transaction record is created, complete with timestamps and all the other bureaucratic details that make accountants so happy. This record is then securely stored, ready for auditing and future reference. Should a discrepancy arise (for example, a teller accidentally adding an extra zero), reconciliation processes (detailed below) are initiated to ensure accuracy.
Withdrawal Transaction Processing, Including ATM Withdrawals
Withdrawals are the exciting part, the moment of truth! The system again verifies the account number and the customer’s identity (usually via PIN or signature, depending on the method). It then checks the available balance to ensure sufficient funds exist. If the balance is sufficient, the requested amount is deducted from the account, and the transaction is recorded. For ATM withdrawals, the process involves communication between the ATM, the bank’s network, and the central system. The ATM verifies the card and PIN, requests authorization from the central system, dispenses the cash, and updates the account balance. Security protocols are heavily involved at every step to protect against fraud, and yes, even the ATMs have their own personalities.
Transaction Discrepancy Resolution
Discrepancies happen, it’s a fact of life (and a testament to the fallibility of even the most sophisticated systems). These could be due to human error, system glitches, or even the occasional mischievous gremlin. The system employs a range of discrepancy resolution mechanisms, from simple reconciliation checks (comparing the total deposits and withdrawals against the account balance) to more sophisticated data analysis techniques. Investigative procedures might involve reviewing transaction logs, security footage (if applicable), and even contacting the customer to clarify any inconsistencies. The goal, of course, is to maintain the integrity of the system and ensure the accuracy of all account balances. Think of it as a highly organized game of financial whack-a-mole.
Online versus Offline Transaction Processing
Online transaction processing is fast, convenient, and available 24/7. It leverages the power of the internet to provide real-time updates and immediate access to account information. Offline processing, on the other hand, requires physical interaction with a bank branch or ATM and often involves a delay before the transaction is reflected in the account balance. While online processing offers speed and convenience, offline methods provide a level of security for those who are less comfortable with online banking. Each method has its own strengths and weaknesses.
Interbank Funds Transfer
Interbank funds transfers involve moving money between different banks. This requires cooperation between multiple institutions and often involves intermediary networks like SWIFT. The steps typically include:
- The sender initiates the transfer, providing the recipient’s account details and the transfer amount.
- The sender’s bank verifies the sender’s account balance and the recipient’s account details.
- The sender’s bank sends a transfer instruction to the recipient’s bank via a secure network.
- The recipient’s bank verifies the transfer instruction and credits the recipient’s account.
- Both banks update their respective transaction records.
The entire process involves a complex interplay of security protocols and communication networks to ensure the secure and timely transfer of funds. Think of it as a highly coordinated, multi-bank relay race, but with far less spandex.
Reporting and Analytics Capabilities

Our Bank Account Management System doesn’t just keep your money safe; it also generates reports that are so insightful, they’ll make your accountant weep with joy (or maybe just slightly less bored). We’re talking about a level of financial transparency that’s practically dazzling. Forget squinting at spreadsheets – this system makes data analysis a delightful experience.
This section details the various reporting and analytics features available to both account holders and bank management, demonstrating how data is leveraged for enhanced risk management and informed decision-making. We’ll also show you a sample report, because who doesn’t love a good, well-formatted table?
Account Holder Reports
Account holders receive regular and on-demand reports providing a clear picture of their financial activity. These reports are designed for simplicity and clarity, avoiding jargon that would make a tax lawyer blush. They empower account holders to easily monitor their transactions, balances, and overall financial health. Reports are available through the online banking portal and can be downloaded in various formats (PDF, CSV, etc.) for easy record-keeping.
Bank Management Reporting Features
Bank management benefits from a comprehensive suite of reporting tools designed to provide a holistic view of the bank’s performance and risk profile. These reports are crucial for strategic planning, regulatory compliance, and identifying potential areas for improvement. The system allows for customized reporting, enabling management to focus on specific metrics relevant to their operational needs. For instance, they can easily generate reports on loan defaults, customer acquisition costs, or the overall profitability of different branches. The system also produces regular compliance reports, saving countless hours of manual data gathering.
Data Analytics for Risk Management
Our system employs sophisticated data analytics techniques to proactively identify and mitigate potential risks. By analyzing historical transaction data, the system can detect unusual patterns that may indicate fraudulent activity. For example, a sudden surge in large international transfers from a low-activity account would trigger an alert. Similarly, the system monitors account balances and transaction frequencies to assess credit risk and identify potential defaults. This proactive approach helps to minimize financial losses and maintain the integrity of the banking system. Think of it as a financial superhero, always on guard.
Examples of Insightful Reports
The system can generate a wide variety of insightful reports. For example, a “Customer Segmentation Report” allows the bank to group customers based on their spending habits and demographics, enabling targeted marketing campaigns. A “Branch Performance Report” compares the efficiency and profitability of different branches, helping management optimize resource allocation. Furthermore, a “Fraud Detection Report” highlights suspicious transactions, allowing for timely intervention and prevention of losses. Finally, a “Regulatory Compliance Report” ensures that the bank adheres to all relevant regulations.
Sample Monthly Account Activity Report, Bank Account Management System
| Date | Description | Debit | Credit |
|---|---|---|---|
| 2024-03-01 | Starting Balance | 1500.00 | |
| 2024-03-05 | Grocery Shopping | 120.50 | |
| 2024-03-10 | Salary Deposit | 2500.00 | |
| 2024-03-15 | Rent Payment | 1000.00 | |
| 2024-03-20 | Utilities | 150.00 | |
| 2024-03-25 | Online Shopping | 75.00 | |
| 2024-03-31 | Ending Balance | 2454.50 |
Integration with Other Systems
Integrating a bank account management system with other systems is akin to orchestrating a finely-tuned banking symphony – each instrument (system) plays its part, creating a harmonious whole (efficient banking operations). A poorly integrated system, however, sounds like a cacophony of errors and delays, leaving customers and bank employees equally frustrated. Therefore, seamless integration is paramount.
The successful integration of a bank account management system relies heavily on well-defined APIs and robust security protocols. Think of APIs as the polite, well-mannered messengers carrying crucial information between different systems. They ensure that data flows smoothly and securely, without causing any undue chaos or security breaches. This integration allows for a more holistic view of customer financial health, streamlines internal processes, and enhances the overall customer experience.
API Functionalities for External System Integration
APIs (Application Programming Interfaces) are the unsung heroes of system integration. They act as bridges, enabling different systems to communicate and exchange data. Our system employs RESTful APIs, known for their simplicity and flexibility. These APIs provide endpoints for various operations, such as retrieving account balances, initiating transfers, and updating customer information. Each endpoint is meticulously documented, specifying the required input parameters, expected output formats, and error handling mechanisms. For example, an API call to retrieve account balance would require an account ID as input and return the current balance and available credit in a JSON format. Comprehensive error codes provide clear indications of any issues, simplifying troubleshooting and maintenance.
Security Considerations When Integrating with Third-Party Applications
Security is paramount, especially when dealing with sensitive financial data. Integrating with third-party applications necessitates stringent security measures. We employ robust authentication and authorization protocols, such as OAuth 2.0, to verify the identity of external systems and restrict access to sensitive data based on the principle of least privilege. Data encryption both in transit and at rest is implemented using industry-standard encryption algorithms (AES-256). Regular security audits and penetration testing are conducted to identify and address potential vulnerabilities. Furthermore, all API calls are logged and monitored for suspicious activity, enabling prompt detection and response to security threats. We adhere strictly to PCI DSS compliance standards for handling payment card data.
Examples of Potential Integrations and Their Benefits
Integrating the bank account management system with other systems offers numerous benefits. For instance, integration with a loan management system allows for automated loan repayments directly from customer accounts, reducing manual intervention and errors. Integration with a CRM system provides a unified view of customer interactions and financial information, enhancing personalized customer service. Another example is the integration with an accounting software which facilitates reconciliation and reporting, simplifying financial management for the bank. This integration leads to faster loan processing, improved customer satisfaction, and enhanced operational efficiency.
Data Flow Between Bank Account System and CRM System
Imagine a diagram showing two boxes, one labeled “Bank Account Management System” and the other “Customer Relationship Management (CRM) System.” Arrows connect the boxes, illustrating the data flow. An arrow from the Bank Account System points to the CRM system, carrying information such as account balance, transaction history, and customer demographics. Another arrow, going the other way, shows the CRM system sending updates on customer preferences and interaction history to the Bank Account System. This bidirectional flow ensures both systems have a comprehensive and up-to-date view of the customer, leading to improved personalization and customer service. For example, if a customer’s contact information changes in the CRM, that update is automatically reflected in the Bank Account Management System, preventing communication issues and maintaining data accuracy.
Scalability and Performance Considerations
Building a bank account management system that can handle the financial lives of millions (or even billions!) requires more than just a solid foundation; it needs the structural integrity of a skyscraper and the speed of a caffeinated cheetah. Let’s delve into the architectural acrobatics and performance prowess required to make this happen.
The architecture of a scalable bank account management system needs to be as flexible as a yoga instructor and as robust as a bank vault. We’re talking a microservices architecture, where different components (account management, transaction processing, reporting) operate independently but communicate seamlessly. This allows for individual scaling – if transaction processing gets swamped, you can boost *that* section without impacting account management. Think of it as having multiple specialized teams, each focusing on their part of the job, instead of one overwhelmed, overworked team.
System Architecture for Scalability
A distributed architecture, employing multiple servers and databases, is crucial. This allows for load balancing – distributing transactions across multiple servers to prevent any single server from becoming overloaded. Imagine a river splitting into multiple streams; each stream handles a portion of the water flow, preventing any one area from flooding. Furthermore, a cloud-based infrastructure offers immense scalability, allowing the system to dynamically adjust resources based on demand. Need more processing power during peak hours? The cloud provides it effortlessly.
Handling Peak Transaction Loads
Peak transaction loads, like the holiday shopping rush but for banking, require proactive strategies. Load balancing, as mentioned, is key. Caching frequently accessed data (like account balances) reduces database load. Think of it as keeping a frequently used cookbook on the counter instead of having to rummage through the cupboard every time. Message queues can buffer incoming transactions, preventing the system from being overwhelmed by sudden surges. This is like having a temporary holding area for packages during a delivery rush, ensuring smooth processing without delays.
Performance Monitoring and Optimization
Constant monitoring is essential. Real-time dashboards showing key performance indicators (KPIs) like transaction processing time and database response time provide immediate insights into system health. Regular performance testing, simulating peak loads, helps identify bottlenecks and areas for improvement. Imagine a thorough medical check-up for your system – catching problems early before they become major issues. Profiling tools pinpoint slow code sections, enabling targeted optimization. This is like a detective meticulously investigating a crime scene to identify the culprit – slow code.
Ensuring System Availability and Reliability
Redundancy is paramount. Having backup servers and databases ensures that if one component fails, the system continues to function. This is like having a spare tire in your car – you don’t want to be stranded on the side of the road. Disaster recovery plans Artikel procedures for restoring the system in case of major outages, such as natural disasters or cyberattacks. This is your emergency plan – knowing exactly what steps to take in a crisis. Regular backups are also crucial to ensure data can be restored if necessary. This is like regularly saving your work on a computer – you don’t want to lose all your progress.
Database Design’s Impact on Performance
Database design is not just about storing data; it’s about optimizing access to that data. Proper indexing ensures quick retrieval of information. Think of it as having a detailed index in a book, making it easy to find specific information. Database normalization reduces data redundancy, improving data integrity and query performance. This is like organizing your closet – getting rid of duplicate items and making it easier to find what you need. Choosing the right database technology (SQL, NoSQL) depends on the specific needs of the system. This is like selecting the right tool for the job – a hammer for nails, a screwdriver for screws.
Conclusive Thoughts
From the meticulous tracking of every transaction to the sophisticated security measures safeguarding your hard-earned cash, Bank Account Management Systems are the silent guardians of the financial realm. We’ve journeyed through the complexities of BAMS, uncovering the intricate mechanisms that ensure the smooth operation of modern banking. While the details may sometimes seem dry, the impact of these systems is anything but. They are the bedrock of our financial stability, a testament to human ingenuity, and a constant source of mild amusement for those who understand their inner workings. So next time you check your balance, take a moment to appreciate the complex symphony of code working tirelessly behind the scenes.
FAQs: Bank Account Management System
What happens if my bank’s system goes down?
Most banks have backup systems and disaster recovery plans. However, expect temporary disruptions to online and potentially in-person services.
How are my transactions protected from fraud?
Banks employ various security measures, including encryption, multi-factor authentication, and fraud detection systems to protect transactions. However, maintaining strong personal security practices remains crucial.
Can I access my account information from anywhere?
Most modern BAMS offer online and mobile access, allowing you to manage your account from virtually anywhere with an internet connection (provided your bank offers these services).
What if I suspect unauthorized activity on my account?
Contact your bank immediately to report suspicious activity. They have procedures to investigate and resolve such issues.