Business Continuity Planning (BCP) is more than just a checklist; it’s a strategic roadmap guiding organizations through unforeseen disruptions. From natural disasters to cyberattacks, BCP ensures the continued operation of critical business functions, minimizing downtime and protecting valuable assets. This proactive approach not only safeguards revenue and reputation but also demonstrates a commitment to stakeholders, fostering trust and confidence in the organization’s ability to weather any storm.
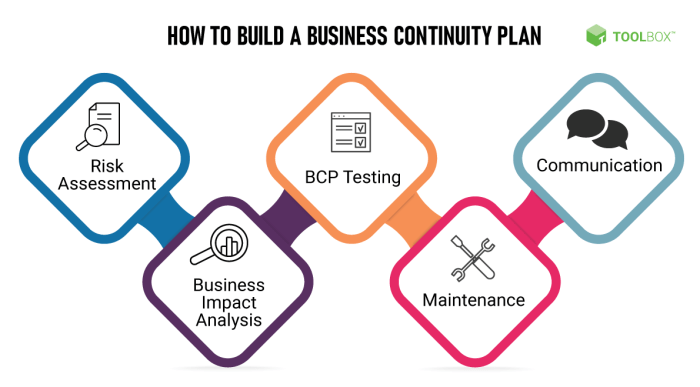
A well-defined BCP encompasses risk assessment, impact analysis, strategy development, recovery procedures, communication protocols, and rigorous testing. It’s a dynamic process, requiring regular review and updates to reflect evolving threats and business priorities. This detailed exploration delves into each component, providing practical guidance for building a resilient and adaptable BCP tailored to specific organizational needs.
Defining Business Continuity Planning (BCP)
Business Continuity Planning (BCP) is a holistic management process designed to enable an organization to prepare for, respond to, and recover from disruptive events that threaten its operations. It goes beyond simply restoring IT systems; it encompasses the entire organization, considering all aspects of its operations and ensuring the continued delivery of critical products and services. A well-defined BCP minimizes downtime, protects reputation, and safeguards the organization’s overall viability.
Business Continuity Planning Core Principles center around risk assessment, mitigation, and recovery. It’s a proactive approach, requiring the identification of potential threats, analysis of their impact, and the development of strategies to minimize those impacts. The process involves establishing clear responsibilities, documenting procedures, testing plans, and regularly reviewing and updating them to reflect changing circumstances. A key principle is the understanding that BCP is not a one-time project but an ongoing process of continuous improvement.
Key Objectives of a Robust BCP
A robust BCP aims to achieve several key objectives. These include minimizing the disruption caused by incidents, ensuring the safety of personnel, protecting critical assets, maintaining operational capabilities, restoring operations as quickly as possible, and preserving the organization’s reputation and market share. Success is measured by the speed and efficiency of recovery, the minimal loss incurred, and the continued satisfaction of stakeholders. For example, a well-executed BCP during a natural disaster would see minimal employee injury, rapid restoration of essential services, and sustained customer confidence.
Organizations Benefiting Most from BCP Implementation
Numerous organizations benefit from implementing a robust BCP. However, those in sectors with high levels of regulatory compliance, significant reliance on technology, and those with complex operations, or those whose disruption would have significant financial or societal consequences, benefit most. This includes financial institutions, healthcare providers, government agencies, and large manufacturing companies. For example, a hospital’s BCP ensures continued patient care during a power outage, while a bank’s BCP safeguards financial transactions during a cyberattack. Smaller businesses also benefit, though their plans may be less complex. The key is to tailor the plan to the organization’s specific needs and risks.
BCP vs. Disaster Recovery Planning (DRP)
While often used interchangeably, BCP and DRP are distinct but related concepts. Disaster Recovery Planning (DRP) focuses specifically on the recovery of IT systems and data after a disaster. It’s a subset of BCP. BCP, on the other hand, takes a broader perspective, encompassing all aspects of business operations, including human resources, supply chain, communications, and customer relations. Therefore, DRP addresses the technological aspects of recovery, while BCP encompasses the entire organizational response and recovery strategy. A comprehensive BCP will include a DRP as a component, but a DRP alone does not constitute a complete BCP. For instance, a DRP might detail the recovery of a company’s servers, while the BCP would also address how to maintain customer service and product delivery during the downtime.
Risk Assessment and Analysis
Effective Business Continuity Planning (BCP) hinges on a thorough understanding of potential threats and their impact on business operations. Risk assessment is the systematic process of identifying, analyzing, and prioritizing these risks, enabling proactive mitigation strategies. This process allows organizations to focus resources on the most critical vulnerabilities, maximizing the effectiveness of their BCP.
A comprehensive risk assessment involves identifying potential threats and vulnerabilities that could disrupt business operations. This includes considering both internal and external factors. Internal factors might involve equipment failures, employee errors, or inadequate security protocols. External factors could include natural disasters, cyberattacks, pandemics, or economic downturns. The assessment should consider the likelihood of each threat occurring and the potential impact on various aspects of the business, including financial losses, reputational damage, and legal liabilities.
Methods for Quantifying Risk Impact
Quantifying the impact of various risks is crucial for prioritizing mitigation efforts. Several methods can be employed, ranging from simple qualitative assessments to complex quantitative models. Qualitative methods might involve assigning risk levels (e.g., low, medium, high) based on expert judgment or historical data. Quantitative methods, on the other hand, involve assigning numerical values to the likelihood and impact of each risk, often using statistical analysis and financial modeling. For instance, a company might estimate the potential financial loss from a cyberattack based on the value of its data and the cost of recovery. A more sophisticated approach might use Monte Carlo simulation to model the uncertainty and variability involved.
Risk Assessment Matrix
A risk assessment matrix provides a visual representation of identified risks, allowing for easy prioritization. The matrix typically includes columns for risk description, likelihood of occurrence, potential impact, and planned mitigation strategies.
| Risk | Likelihood | Impact | Mitigation Strategy |
|---|---|---|---|
| Major Power Outage | Medium | High (Significant downtime, data loss) | Redundant power supply, generator backup |
| Cybersecurity Breach | High | High (Data loss, financial losses, reputational damage) | Robust cybersecurity measures, regular security audits, incident response plan |
| Key Personnel Loss | Low | Medium (Project delays, decreased productivity) | Cross-training, succession planning |
| Natural Disaster (Flood) | Low | High (Significant damage to facilities, business interruption) | Disaster recovery plan, offsite data backup, insurance |
Risk Prioritization
Once risks have been identified and assessed, they should be organized according to their severity and likelihood of occurrence. This allows organizations to focus their resources on the most critical risks. A common approach is to use a risk matrix to visually represent the risks, plotting them based on their likelihood and impact. Risks falling into the high-likelihood/high-impact quadrant require immediate attention and the development of robust mitigation strategies. Those in lower quadrants may still require attention, but the urgency might be lower, allowing for a phased approach to mitigation.
Business Impact Analysis (BIA)
A Business Impact Analysis (BIA) is a critical component of Business Continuity Planning (BCP). It systematically identifies and analyzes the potential consequences of disruptions to business operations, allowing organizations to prioritize resources and recovery strategies effectively. The BIA helps determine the impact of various disruptions on different business functions, ultimately informing the development of recovery time objectives (RTOs) and recovery point objectives (RPOs).
Steps Involved in Conducting a Thorough Business Impact Analysis
A comprehensive BIA involves a structured approach. First, key business functions are identified and documented, considering their interdependencies. Next, potential threats and their potential impact on each function are assessed. This assessment involves evaluating the likelihood and severity of each threat, considering factors such as frequency, duration, and potential financial, reputational, and legal consequences. Qualitative and quantitative data are gathered through interviews, surveys, and analysis of historical data. Finally, the analysis is documented, reviewed, and approved by relevant stakeholders. This process ensures that the BIA accurately reflects the organization’s operational realities and vulnerabilities.
Determining Maximum Tolerable Downtime (MTD) for Critical Business Functions
Maximum Tolerable Downtime (MTD) represents the maximum period a business function can be unavailable before causing unacceptable consequences. Determining MTD requires careful consideration of financial losses, reputational damage, legal liabilities, and the impact on customers and stakeholders. For instance, a financial institution might have a very low MTD for its online banking system, perhaps measured in minutes, due to the significant financial and reputational repercussions of extended downtime. In contrast, a less critical function might have a higher MTD, allowing for a more extended recovery period. MTD is often determined through a combination of quantitative analysis (e.g., calculating revenue loss per hour of downtime) and qualitative assessments (e.g., evaluating the impact on customer satisfaction and regulatory compliance).
Key Performance Indicators (KPIs) to Measure Business Impact
KPIs provide measurable indicators of business impact. Examples include: revenue loss per hour of downtime, customer churn rate following an incident, order fulfillment rate, percentage of critical systems operational, and the number of customer service calls received after a disruption. The choice of KPIs will depend on the specific business functions and the nature of potential disruptions. For a manufacturing company, KPIs might focus on production output and inventory levels. For a retail business, KPIs might concentrate on sales figures and customer traffic. These metrics provide concrete data to support the prioritization of recovery efforts.
Prioritized List of Critical Business Functions Based on Impact and Recovery Time Objectives (RTOs)
After conducting the BIA, a prioritized list of critical business functions is created. This list ranks functions based on their impact on the organization and their RTOs. Functions with high impact and short RTOs (meaning they require rapid recovery) are prioritized over functions with lower impact and longer RTOs. For example, a company might prioritize its core sales function (high impact, short RTO) over its internal communications function (lower impact, longer RTO). This prioritization guides resource allocation and recovery strategy development, ensuring that the most critical functions are restored first. This prioritization can be represented in a table, for example:
| Business Function | Impact (High/Medium/Low) | RTO (hours) | Priority |
|---|---|---|---|
| Order Processing | High | 4 | 1 |
| Customer Service | High | 8 | 2 |
| Marketing | Medium | 24 | 3 |
| Human Resources | Low | 72 | 4 |
Developing a BCP Strategy
Developing a robust Business Continuity Plan (BCP) strategy is crucial for ensuring business resilience. This involves identifying potential disruptions, assessing their impact, and implementing strategies to mitigate their effects, allowing the organization to continue operating, albeit perhaps at a reduced capacity, during and after an incident. A well-defined strategy ensures minimal downtime, protects critical assets, and safeguards the organization’s reputation.
The selection of a BCP strategy depends heavily on the nature of the business, the identified critical processes, and the resources available. There isn’t a one-size-fits-all solution; instead, organizations often combine several strategies to create a comprehensive approach.
BCP Strategy Options: Failover, Redundancy, and Backup
Several key strategies contribute to a robust BCP. Failover, redundancy, and backup represent distinct approaches, each with its strengths and weaknesses. Understanding their differences allows for informed decision-making in strategy development.
Failover mechanisms automatically switch operations to a secondary system in case of primary system failure. This could involve transferring data processing to a backup server, redirecting customer calls to an alternate call center, or shifting production to a secondary facility. A failover system is designed to be quick and seamless, minimizing disruption. For example, a company’s website might automatically switch to a mirrored site hosted in a different geographical location if the primary site experiences an outage.
Redundancy, in contrast, involves creating duplicate systems or processes. This ensures that even if one system fails, another is immediately available to take over. Redundancy can be applied to various aspects of the business, from IT infrastructure (multiple servers, network connections) to physical facilities (multiple warehouses). A bank, for instance, might have multiple ATMs connected to different networks to ensure uninterrupted service.
Backup strategies focus on data preservation and recovery. Regular data backups allow for restoration of lost information in case of a disaster. This includes not only electronic data but also physical documents and other crucial records. Different backup methods exist, including local backups, cloud backups, and offsite storage. A hospital regularly backing up patient records to a secure cloud service exemplifies this approach.
Designing a High-Level BCP Strategy
A comprehensive BCP strategy incorporates various essential elements to ensure its effectiveness. These elements work in concert to provide a holistic approach to business continuity.
A key component is a well-defined communication plan. This plan Artikels communication channels, responsibilities, and procedures for disseminating information both internally (to employees) and externally (to customers, suppliers, and stakeholders) during and after a disruptive event. Clear communication is crucial to minimize confusion and maintain operational efficiency. The plan should include designated spokespeople, pre-approved messaging, and multiple communication channels (email, phone, SMS).
Another crucial element is resource allocation. This involves identifying the resources required to maintain critical operations during a disruption and planning for their allocation. Resources include personnel, financial resources, equipment, and technology. The allocation plan should prioritize the most critical resources and ensure their availability when needed. A manufacturing company might pre-position essential spare parts at multiple locations to ensure continued production.
Incorporating Technology Solutions into the BCP Strategy
Technology plays a significant role in modern BCP strategies. Various technological solutions can enhance resilience and facilitate faster recovery.
Cloud computing offers several advantages for BCP. Cloud-based applications and data storage provide accessibility from various locations, ensuring business continuity even if the primary office is inaccessible. Disaster recovery as a service (DRaaS) is a specific cloud-based solution that replicates data and applications to a remote location, allowing for quick recovery in case of an outage.
Virtualization allows for the creation of virtual servers and desktops, enabling quick restoration of IT systems in case of hardware failure. This reduces downtime and maintains operational efficiency.
Automated systems, such as automated backups and system monitoring tools, reduce manual intervention and improve the speed and efficiency of recovery processes. These systems can automatically detect problems, initiate recovery procedures, and alert relevant personnel.
Finally, robust cybersecurity measures are vital to prevent disruptions caused by cyberattacks. These measures include firewalls, intrusion detection systems, and regular security audits. A strong cybersecurity posture is crucial to preventing data breaches and system disruptions.
Recovery Strategies and Procedures
Developing robust recovery strategies and procedures is paramount to ensuring business continuity. These strategies detail how your organization will restore critical functions and systems following a disruptive event. A well-defined plan minimizes downtime, reduces financial losses, and protects your reputation. This section Artikels the key components of effective recovery strategies.
Effective recovery procedures require a detailed understanding of your business’s critical functions and their dependencies. They should be specific, actionable, and regularly tested to ensure their effectiveness in a real-world scenario. The process involves outlining steps, assigning responsibilities, and identifying resources needed for recovery. These procedures should be readily accessible to relevant personnel and regularly reviewed and updated to reflect changes within the organization or its environment.
Detailed Recovery Procedures for Critical Business Functions
Recovery procedures should be created for each critical business function identified during the Business Impact Analysis (BIA). These procedures should specify the steps required to restore each function to an acceptable level of operation, including timelines, resources, and responsibilities. For instance, the recovery procedure for IT systems might involve activating a backup data center, restoring data from backups, and verifying system functionality. Similarly, a procedure for customer service might detail activating a temporary call center and communicating with customers about the disruption and its resolution.
Flowchart Illustrating Recovery Process for a Power Outage
The following flowchart depicts the steps involved in recovering from a power outage. This is a simplified example and should be adapted to reflect your organization’s specific needs and infrastructure.
Flowchart: Power Outage Recovery
[Start] –> [Detect Power Outage] –> [Activate Emergency Power System (UPS)] –> [Initiate Backup Generator] –> [Verify System Functionality] –> [Assess Damage] –> [Notify Relevant Personnel] –> [Restore Critical Systems] –> [Communicate with Stakeholders] –> [Transition to Normal Operations] –> [Post-Incident Review] –> [End]
* Detect Power Outage: Automated monitoring systems or manual checks identify the outage.
* Activate Emergency Power System (UPS): Uninterruptible Power Supply provides temporary power to critical systems.
* Initiate Backup Generator: The generator kicks in to provide sustained power.
* Verify System Functionality: Confirm critical systems are operating on backup power.
* Assess Damage: Determine the extent of any damage caused by the outage.
* Notify Relevant Personnel: Inform key personnel, including IT, management, and communications teams.
* Restore Critical Systems: Prioritize restoring essential systems and functions.
* Communicate with Stakeholders: Update customers, employees, and other stakeholders on the situation.
* Transition to Normal Operations: Gradually restore normal operations as power is fully restored.
* Post-Incident Review: Analyze the event to identify areas for improvement in future preparedness.
Testing and Validating Recovery Procedures
Regular testing is crucial to ensure the effectiveness of recovery procedures. This involves simulating various scenarios, such as power outages, natural disasters, or cyberattacks, to identify weaknesses and refine the plan. Testing can range from tabletop exercises, which involve discussing the procedures, to full-scale simulations, which involve actually implementing the procedures. The goal is to identify gaps and refine the plan to ensure it can withstand real-world challenges. Documentation of test results is essential to track progress and demonstrate the effectiveness of the plan.
Recovery Methods for Different Types of Disruptions
Different types of disruptions require different recovery methods. For example, a natural disaster might necessitate relocating operations to a backup facility, while a cyberattack might involve restoring data from backups and implementing enhanced security measures. Below are some examples:
Natural Disasters (e.g., Hurricane): Relocation to a pre-determined backup site; data backup and recovery; communication plan activation; employee safety protocols; insurance claims processing.
Cyberattacks (e.g., Ransomware): Data restoration from backups; system remediation; security protocols enhancement; incident response team activation; law enforcement notification (if necessary); legal counsel consultation.
Power Outages: Activation of backup power sources (generators, UPS); critical system prioritization; communication plan activation; employee notification.
Communication and Coordination
Effective communication is the bedrock of a successful business continuity plan. During a disruption, timely and accurate information flow prevents panic, ensures coordinated responses, and minimizes damage to reputation and operations. A well-defined communication strategy is crucial for keeping stakeholders informed, maintaining confidence, and facilitating a swift recovery.
A breakdown in communication can lead to confusion, delayed responses, and ultimately, a more significant impact on the business. Misinformation can spread rapidly, exacerbating the situation and hindering recovery efforts. Conversely, a robust communication plan ensures that everyone involved – from employees and customers to partners and regulatory bodies – receives the necessary information at the right time, enabling them to take appropriate actions.
Communication Plan Design
A comprehensive communication plan should clearly define roles, responsibilities, and communication channels. This plan should Artikel who is responsible for communicating what information to whom, using which methods, and by when. Consider designating a central communication hub or team responsible for coordinating information dissemination and ensuring consistent messaging. Pre-assigned roles reduce confusion and ensure accountability during a crisis. For example, the IT department might be responsible for communicating system outages, while the HR department addresses employee concerns. The CEO might be the primary spokesperson for external communications.
Stakeholder Information Methods
Keeping stakeholders informed during an incident requires a multi-faceted approach. Regular updates are vital, providing consistent and transparent information to alleviate anxiety and maintain confidence. The frequency and content of these updates should be tailored to the specific audience and the severity of the disruption. For instance, employees may need frequent updates on the situation and recovery efforts, while customers might require less frequent but more concise updates focusing on service impacts and restoration timelines. Methods for delivering these updates can include email, text messaging, phone calls, social media, and even pre-recorded video messages for wider dissemination. Transparency is key; acknowledging uncertainties while outlining the steps being taken to address them builds trust.
Communication Tools and Technologies
Various tools and technologies can facilitate effective crisis communication. Email and SMS messaging are readily available and effective for reaching large numbers of people quickly. However, in situations where phone lines are down or internet access is limited, alternative methods are crucial. Two-way radios, satellite phones, and dedicated crisis communication platforms offer resilience against infrastructure failures. Social media platforms can be leveraged for public announcements and updates, although careful management is required to avoid misinformation and maintain control of the narrative. Consider using a dedicated crisis communication platform that allows for centralized message creation and distribution, ensuring consistent messaging across all channels. Real-time collaboration tools, such as video conferencing software, can also help facilitate communication between teams and stakeholders during the crisis. For example, during Hurricane Katrina, the lack of a coordinated communication plan led to significant confusion and hampered rescue efforts. Contrast this with companies that utilize sophisticated crisis communication systems and have pre-planned communication strategies; they often recover more swiftly and efficiently.
Testing and Maintenance

A robust Business Continuity Plan (BCP) isn’t merely a document gathering dust on a shelf; it’s a living, breathing strategy that requires regular testing and maintenance to ensure its effectiveness in a real-world crisis. Without periodic reviews and simulations, the plan can become outdated, irrelevant, and ultimately, fail to achieve its intended purpose of protecting the business. This section Artikels the importance of testing and maintenance, different testing methodologies, documentation best practices, and a suggested schedule for maintaining a current and effective BCP.
Regular testing and maintenance are critical to validating the plan’s effectiveness and identifying areas for improvement. This iterative process ensures the BCP remains relevant to the evolving business landscape and technological advancements, strengthening the organization’s resilience to disruptions. Failure to test the plan adequately could lead to significant financial losses, reputational damage, and even business failure during a real emergency.
BCP Test Types
Different types of tests offer varying levels of complexity and realism, allowing organizations to progressively assess the plan’s efficacy. The choice of test type should depend on the organization’s size, resources, and the criticality of the business processes being tested.
- Tabletop Exercises: These involve a facilitated discussion among key personnel to walk through various scenarios and assess the plan’s response. This is a low-cost, low-resource method ideal for initial testing and regular review. Participants discuss their roles, responsibilities, and potential challenges without actually implementing the recovery procedures. For example, a tabletop exercise might simulate a server outage, prompting discussion on alternative data access methods and communication protocols.
- Functional Exercises: These tests involve activating a specific portion of the BCP, such as data recovery or system restoration. This allows for a more hands-on evaluation of the plan’s practical aspects. For example, a functional exercise might involve restoring a backup of critical data to a secondary server to test data recovery time objectives.
- Full-Scale Simulations: These are comprehensive tests that involve simulating a major disruption and executing the entire BCP. These are more resource-intensive but provide the most realistic assessment of the plan’s overall effectiveness. A full-scale simulation might involve relocating employees to an alternate worksite and activating all recovery procedures, mirroring a major disaster scenario like a widespread power outage.
Documenting Test Results and Improvements
Thorough documentation is essential for tracking progress, identifying weaknesses, and making necessary revisions to the BCP. This should include a detailed record of the test objectives, methodology, participants, scenarios tested, observed outcomes, and any identified gaps or areas for improvement. The documentation should also clearly Artikel the actions taken to address identified weaknesses, ensuring continuous improvement of the plan. For example, if a tabletop exercise reveals a communication breakdown, the documentation should specify the issue, the proposed solution (e.g., implementing a new communication system), and the timeline for implementation.
BCP Drill and Update Schedule
A regular schedule ensures the BCP remains relevant and effective. The frequency of testing and updates should be tailored to the organization’s risk profile and the criticality of its business processes. A suggested schedule might include:
- Annual Full-Scale Simulation: A comprehensive test to evaluate the entire BCP.
- Semi-Annual Tabletop Exercises: Focus on specific scenarios or business units.
- Quarterly Functional Exercises: Test specific recovery procedures, such as data backup and restoration.
- Ongoing Plan Updates: Regular review and updates to reflect changes in the business environment, technology, and personnel.
Training and Awareness

A comprehensive training and awareness program is crucial for the success of any Business Continuity Plan (BCP). Employees must understand their roles and responsibilities during a disruption to ensure a smooth and efficient recovery. This involves not only providing specific procedural training but also fostering a culture of preparedness and proactive risk management.
Effective training ensures that employees are equipped to handle their assigned tasks, minimizing downtime and potential losses. A well-structured program should cover various aspects of the BCP, from understanding potential threats to executing recovery procedures. Regular refresher training and awareness campaigns maintain preparedness and adapt the plan to evolving business needs.
Training Program Content
The training program should be modular and tailored to different employee roles and responsibilities. It should incorporate various learning methods to cater to diverse learning styles. For example, some modules might focus on specific procedures, while others could cover broader topics such as risk awareness and the importance of individual contributions to overall business resilience. A blended learning approach, combining online modules with hands-on workshops and simulations, can prove particularly effective.
Employee Role Education Materials
Clear and concise materials outlining individual roles and responsibilities during a disruption are essential. These materials should be readily accessible and easy to understand, even under stressful conditions. This could include role-specific checklists, contact lists, and step-by-step guides for critical tasks. The materials should also clearly define escalation paths and communication protocols. For instance, a checklist for IT personnel might include steps for data backup and system restoration, while a checklist for customer service representatives might Artikel procedures for informing customers and handling inquiries.
Methods for Raising BCP Awareness
Raising awareness of the importance of BCP should be an ongoing process, not a one-time event. Methods include regular newsletters, company-wide emails, interactive workshops, and inclusion of BCP elements in new employee orientation programs. Gamification techniques, such as quizzes or simulations, can also enhance engagement and knowledge retention. Furthermore, showcasing real-life examples of business disruptions and the successful application of BCP in similar organizations can powerfully illustrate the plan’s value. For example, a case study of a company that successfully recovered from a cyberattack using its BCP could serve as a compelling example.
Effective Training Methods for Different Employee Groups
Different employee groups require tailored training approaches. For instance, senior management might benefit from strategic-level training focusing on decision-making during a crisis, while operational staff might require more hands-on training on specific recovery procedures. Technical staff may need in-depth training on data recovery and system restoration. Consider using scenario-based training for all groups to simulate real-life situations and assess employee preparedness. For example, a simulated power outage scenario could test the effectiveness of the backup power system and the communication protocols established in the BCP. Regular drills and exercises are also essential to test the plan’s effectiveness and identify areas for improvement.
Final Review
Implementing a robust Business Continuity Plan is not merely a compliance exercise; it’s an investment in the long-term health and sustainability of an organization. By proactively identifying and mitigating risks, establishing clear recovery strategies, and fostering a culture of preparedness, businesses can navigate disruptions with confidence, minimizing losses and ensuring continued success. The framework Artikeld here provides a solid foundation for building a resilient organization capable of thriving in an unpredictable world.
FAQ Resource
What is the difference between BCP and Disaster Recovery Planning (DRP)?
BCP is a broader concept encompassing all aspects of maintaining business operations during disruptions, while DRP focuses specifically on recovering IT systems and data after a disaster.
How often should a BCP be tested?
The frequency of testing depends on the organization’s risk profile and criticality of its operations. Annual testing is generally recommended, with more frequent testing for high-risk scenarios.
Who should be involved in developing a BCP?
BCP development should involve a cross-functional team representing various departments and levels of the organization, including IT, operations, finance, and senior management.
What are the key metrics for measuring BCP effectiveness?
Key metrics include recovery time objectives (RTOs), recovery point objectives (RPOs), downtime, and cost of disruption.
How can we ensure employee buy-in for BCP initiatives?
Effective communication, clear roles and responsibilities, and regular training and awareness programs are crucial for ensuring employee buy-in and participation.