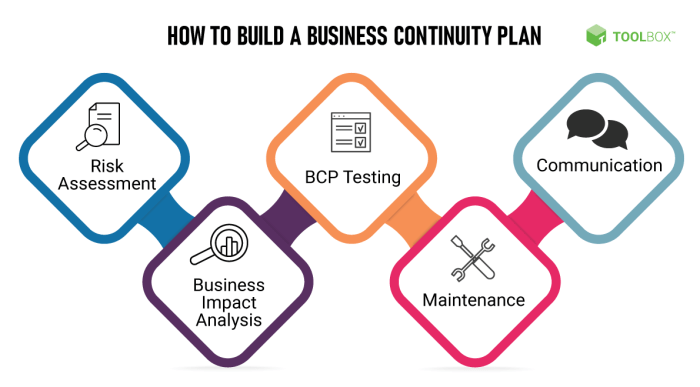
Business Continuity Planning Guide: Let’s face it, even the most meticulously planned businesses can get blindsided by a rogue asteroid (okay, maybe not an asteroid, but you get the picture). This guide isn’t about predicting the apocalypse; it’s about creating a robust, adaptable plan to ensure your business keeps humming along, even when things go sideways. We’ll explore risk assessment, recovery strategies, and communication protocols – all while keeping things surprisingly engaging. Think of it as a survival manual, but for your business, not a zombie invasion.
We’ll delve into the nitty-gritty of identifying potential threats, both internal (like that one employee who insists on using a password of “password123”) and external (like, say, a global pandemic). We’ll then equip you with the tools to assess the likelihood and impact of these threats, prioritize risks, and develop recovery strategies tailored to your specific needs. From choosing the right recovery solutions to mastering the art of effective communication during a crisis, this guide will have you prepared for almost anything (except maybe that asteroid).
Introduction to Business Continuity Planning
Let’s face it, nobody *wants* to think about their business imploding like a soufflé left unattended. But ignoring the possibility is a recipe for disaster, a business equivalent of walking a tightrope blindfolded while juggling chainsaws. That’s where Business Continuity Planning (BCP) comes in – your safety net, your emergency parachute, your incredibly well-organized escape route from impending doom.
Business Continuity Planning (BCP) is the process of creating a roadmap to keep your business operational during and after a disruptive event. Think of it as a meticulously crafted survival guide, detailing how to keep the lights on (literally and figuratively) when the unexpected happens. It’s not just about surviving; it’s about thriving, even amidst chaos. The size of your business doesn’t diminish the importance; a small startup facing a data breach needs a BCP just as much as a multinational corporation facing a natural disaster. In fact, a well-defined BCP can be the difference between bouncing back quickly and closing shop permanently.
The Importance of BCP Across Organizations, Business Continuity Planning Guide
BCP isn’t a luxury; it’s a necessity, regardless of whether you’re a solopreneur working from a home office or the CEO of a global conglomerate. Smaller organizations might focus on simpler, more streamlined plans, while larger organizations require more complex, multifaceted approaches. However, the underlying principle remains the same: to minimize disruption and ensure business survival. A small bakery facing a power outage needs a plan just as much as a large bank facing a cyberattack. The scale might differ, but the need for preparedness is universal. A robust BCP can help smaller businesses recover faster from setbacks, maintain customer trust, and avoid costly downtime, ultimately contributing to long-term success and growth. For larger organizations, a BCP is crucial for maintaining operational resilience, protecting reputation, and complying with regulatory requirements.
Examples of Disruptive Events
Let’s get real: the world isn’t always sunshine and rainbows. Disruptions can come in many forms, some predictable, others utterly unexpected. Think natural disasters like hurricanes or earthquakes, which can cripple infrastructure and supply chains. Then there are the less dramatic but equally disruptive events: cyberattacks that freeze your systems, power outages that shut down operations, or even a key employee suddenly leaving the company. A pandemic, like the one we recently experienced, highlighted the vulnerability of businesses without robust BCPs. These disruptions aren’t hypothetical scenarios; they’re realities that can severely impact any organization, regardless of its size or industry. Preparation is key.
Benefits of a Well-Defined BCP
Having a well-defined BCP is like having a secret weapon in your business arsenal. It doesn’t guarantee immunity from problems, but it significantly reduces the impact and accelerates recovery. The benefits are numerous: minimizing downtime and financial losses, maintaining customer confidence, ensuring regulatory compliance, improving employee morale (because a well-prepared team is a confident team), and protecting your hard-earned reputation. In short, a good BCP is an investment that pays off handsomely, protecting your business from the unexpected and allowing you to navigate challenges with grace (and maybe a little less panic). It’s the difference between scrambling in chaos and executing a well-rehearsed plan.
Risk Assessment and Analysis
Let’s face it, predicting the future is a fool’s errand (unless you’re a surprisingly accurate fortune teller, in which case, please share your secrets!). However, identifying potential threats to your business isn’t about predicting the apocalypse; it’s about sensible planning for the inevitable bumps in the road. This section will guide you through a systematic risk assessment, turning potential disasters into manageable challenges. Think of it as a preemptive strike against chaos, not a crystal ball gazing session.
Risk assessment isn’t just about identifying problems; it’s about understanding their potential impact. We’ll explore methods to quantify the likelihood and severity of these threats, allowing you to prioritize your efforts effectively. Imagine it as triage for your business – focusing your resources where they’ll do the most good. This proactive approach will help you build a more resilient and robust business continuity plan, transforming potential crises into opportunities for growth and resilience.
Identifying Potential Internal and External Threats
Identifying potential threats requires a comprehensive approach, examining both internal weaknesses and external pressures. Internal threats might include IT system failures, employee negligence, or insufficient training. External threats could range from natural disasters (earthquakes, floods, hurricanes – the usual suspects) to economic downturns, cyberattacks, or even a sudden global pandemic of a surprisingly contagious sneezing disease. A thorough review of your business operations, considering all aspects of your infrastructure and supply chain, is crucial to identifying these potential vulnerabilities. Remember, even seemingly minor issues can snowball into significant problems if left unchecked. A thorough risk assessment considers the big picture and the tiny details, because, let’s face it, sometimes the smallest things have the biggest impact.
Assessing Likelihood and Impact
Once you’ve identified potential threats, you need to evaluate their likelihood and potential impact. Likelihood refers to the probability of a threat occurring. This can be expressed qualitatively (low, medium, high) or quantitatively (e.g., a 10% chance of a power outage per year). Impact refers to the severity of the consequences if the threat materializes. This might be measured in terms of financial losses, reputational damage, or disruption to operations. For example, a minor IT glitch might have a low likelihood and low impact, while a major cyberattack could have a high likelihood and catastrophic impact (depending on your security measures, of course!). By carefully considering both likelihood and impact, you can accurately gauge the severity of each risk.
Designing a Risk Matrix
A risk matrix is a visual tool that helps you understand the relative severity of identified risks. It typically plots likelihood on one axis and impact on the other, creating a grid where each cell represents a different level of risk. For instance, a threat with high likelihood and high impact would fall into the high-risk quadrant, requiring immediate attention. A threat with low likelihood and low impact would fall into the low-risk quadrant, allowing you to allocate resources more strategically. The risk matrix provides a clear, concise representation of your risk profile, making it easier to prioritize your efforts. Think of it as a visual roadmap to risk management, guiding you towards a more resilient future.
Prioritizing Risks
Prioritizing risks is crucial for effective resource allocation. After assessing the likelihood and impact of each threat, you can rank them based on their overall severity. This allows you to focus your efforts on the most critical risks first, ensuring that your resources are used effectively. A prioritized list helps you to strategically allocate your resources, ensuring that you’re focusing on the threats that pose the greatest danger to your business. It’s like tackling the biggest fire first before worrying about the smaller embers.
| Risk | Likelihood | Impact | Priority |
|---|---|---|---|
| Major Cyberattack | High | Catastrophic | High |
| Natural Disaster (Flood) | Medium | High | High |
| Key Employee Departure | Medium | Medium | Medium |
| Minor IT Glitch | High | Low | Low |
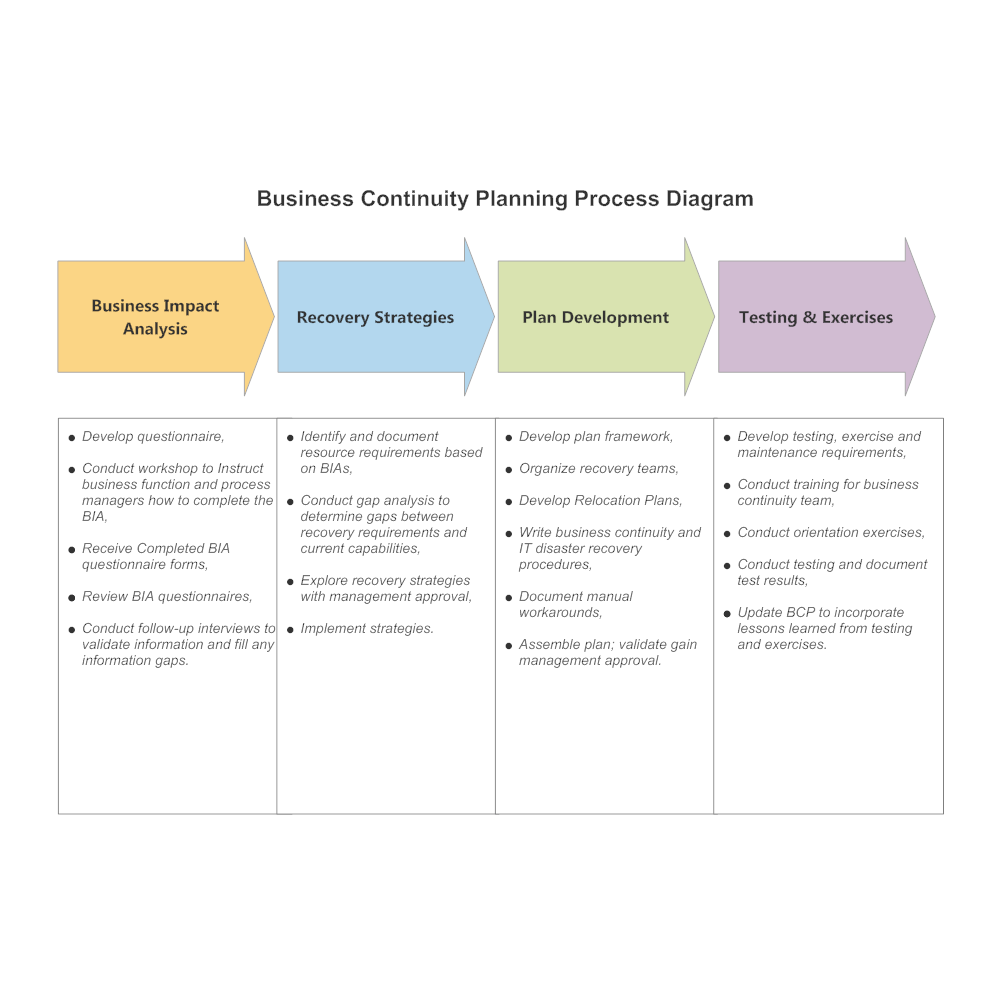
Business Impact Analysis (BIA)
The Business Impact Analysis, or BIA, isn’t just another corporate buzzword; it’s the superhero your business continuity plan desperately needs. Think of it as a crystal ball, but instead of predicting the future, it reveals the potential damage of disruptions – allowing you to strategically allocate resources and prioritize recovery efforts. Without a BIA, you’re essentially navigating a hurricane in a rowboat made of paperclips.
A thorough BIA meticulously examines your organization’s critical functions, assessing their vulnerability to various disruptions and quantifying the potential consequences. This process helps determine which functions need the most protection and what resources are necessary to ensure swift recovery. It’s a bit like a financial audit, but instead of examining your bank account, you’re examining the health of your entire business.
BIA Steps
Conducting a comprehensive BIA requires a methodical approach. Jumping in headfirst without a plan is like trying to bake a cake without measuring ingredients – you might get something edible, but it’s unlikely to be a masterpiece. A structured approach ensures you capture all critical information and avoid costly oversights.
- Identify Critical Business Functions: This involves pinpointing the core processes that are essential for your organization’s survival and success. Think of it as identifying the vital organs of your business. Without them, the whole operation starts to fail. Examples include customer service, order fulfillment, and payroll.
- Determine Maximum Tolerable Downtime (MTD): For each critical function, establish the maximum amount of downtime that can be tolerated before significant financial losses, legal repercussions, or reputational damage occur. This is a crucial step in prioritizing recovery efforts. For instance, an e-commerce platform might have a much lower MTD than a manufacturing plant that produces non-perishable goods.
- Analyze Potential Disruptions: Brainstorm potential disruptions that could impact your business functions. This includes natural disasters, cyberattacks, pandemics, and even employee absences. The more comprehensive your list, the better prepared you’ll be.
- Quantify Potential Impacts: For each disruption and critical function, estimate the financial losses, operational disruptions, and reputational damage that could result. This could involve calculating lost revenue, fines, or the cost of recovery. Consider using financial modeling tools to make these estimations more accurate.
- Develop Recovery Strategies: Based on the analysis, develop recovery strategies for each critical function, outlining the steps required to restore operations in the event of a disruption. This might include backup systems, disaster recovery sites, or alternative suppliers.
Key Business Functions for BIA Inclusion
The specific functions you include in your BIA will depend on your business model. However, some common examples include:
- Customer Service: Losing customer service capabilities can severely damage your reputation and lead to lost revenue. Think about the potential impact of a prolonged outage on your customer satisfaction scores.
- Order Fulfillment: Disruptions to order fulfillment can disrupt the supply chain and lead to customer dissatisfaction. Imagine the chaos if your online orders stop being processed for several days.
- Financial Operations: Disruptions to financial operations can lead to cash flow problems and regulatory non-compliance. This is where things can get really expensive, really quickly.
- Information Technology (IT): In today’s digital world, IT is the backbone of most businesses. A disruption can cripple your entire operation. Consider the impact of a ransomware attack on your data and systems.
- Human Resources (HR): While often overlooked, HR plays a critical role in maintaining business operations. Consider the impact of a sudden loss of key personnel on your ability to function.
Determining Maximum Tolerable Downtime (MTD)
Determining the MTD for each critical business function requires careful consideration of several factors. This isn’t a guessing game; it needs to be a data-driven decision. The consequences of getting this wrong can be severe.
MTD is often expressed in hours or days, and it represents the point beyond which the negative impacts of a disruption become unacceptable.
To determine MTD, consider the following:
- Financial Impact: Estimate the financial losses (lost revenue, fines, etc.) that would occur for each hour or day of downtime.
- Reputational Damage: Assess the potential damage to your reputation and brand image. A long outage could severely impact customer trust.
- Legal and Regulatory Compliance: Consider any legal or regulatory requirements that must be met. Non-compliance can lead to hefty fines.
- Competitive Advantage: Evaluate how much downtime your competitors could tolerate before losing market share. This can help inform your MTD.
For example, a hospital’s emergency room likely has an MTD measured in minutes, while a small retail store might have an MTD measured in days. The key is to establish a realistic and data-driven MTD for each critical function.
Developing Recovery Strategies: Business Continuity Planning Guide
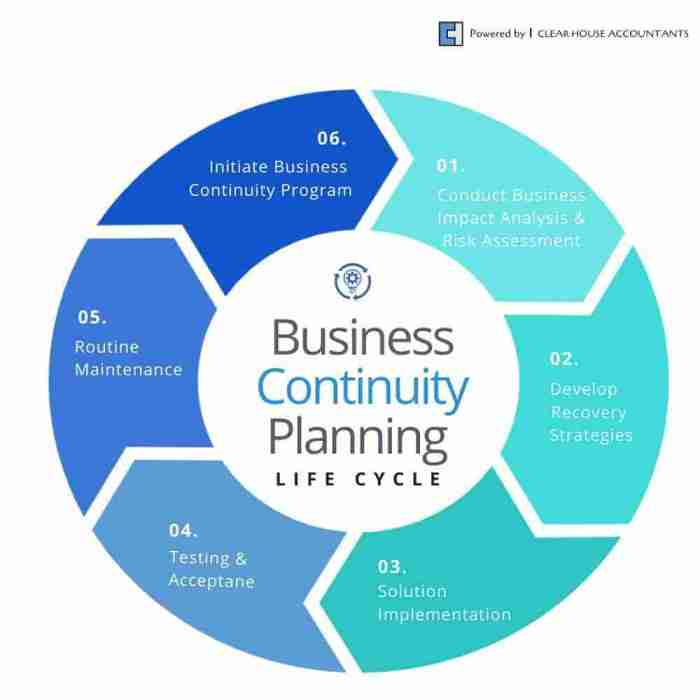
Developing robust recovery strategies is less about predicting the apocalypse (though that’s fun to imagine) and more about minimizing the damage when the inevitable happens. Think of it as having a really well-organized emergency kit, but for your entire business. A good recovery strategy ensures that even if your office is swallowed by a rogue sinkhole (it happens!), you can still keep the lights on – metaphorically speaking, of course.
Recovery strategies are your business’s safety net, catching you when things go wrong. They’re designed to get you back on your feet quickly and efficiently, minimizing downtime and damage. Choosing the right strategy requires a careful balancing act between cost and effectiveness, all while keeping your Business Impact Analysis (BIA) firmly in mind.
Backup and Recovery
Backup and recovery is the cornerstone of any effective recovery strategy. This involves regularly backing up critical data and systems to a secure location, allowing for restoration in the event of data loss or system failure. Think of it as creating a digital clone of your business – a slightly less creepy version, hopefully. Different backup methods exist, including full backups, incremental backups, and differential backups, each with varying storage space requirements and restoration times. A well-defined backup and recovery plan should include procedures for testing backups, ensuring data integrity, and recovering data to different environments. For example, a small business might use a cloud-based backup solution for simplicity and cost-effectiveness, while a large corporation might employ a more complex, multi-site backup strategy to ensure redundancy and business continuity.
Failover
Failover strategies involve switching to a redundant system or location in the event of a primary system failure. Imagine a perfectly choreographed dance where one system gracefully steps aside as the other smoothly takes over. This seamless transition minimizes disruption and keeps operations running. Failover can range from simple server redundancy to complex geographically dispersed data centers. The cost of implementing a failover system can vary dramatically depending on the complexity and scale of the system. For instance, a small e-commerce site might use a simple failover to a cloud-based server, while a financial institution would likely invest in a more sophisticated, geographically redundant system to maintain high availability and compliance with regulatory requirements.
Redundancy
Redundancy is all about having backups for backups. It’s the ultimate insurance policy, ensuring that even if one system fails, another is ready to take its place. This can involve redundant servers, network connections, power supplies, and even entire data centers. While redundancy adds to the initial cost, it significantly reduces the risk of prolonged downtime and data loss. Consider a hospital’s critical systems; redundancy is paramount to ensure patient safety and continuity of care. The cost of redundancy in such a critical environment is justified by the potentially catastrophic consequences of failure.
Recovery Strategy Prioritization Based on BIA
The Business Impact Analysis (BIA) provides the roadmap for prioritizing recovery strategies. It identifies critical business functions and their associated recovery time objectives (RTOs) and recovery point objectives (RPOs). These metrics dictate the level of investment and resources allocated to different recovery strategies. For example, a company might prioritize recovering its customer relationship management (CRM) system over its internal email system, given the greater impact of CRM downtime on revenue generation. This prioritization ensures that resources are focused on the most critical aspects of the business, maximizing the effectiveness of the recovery plan.
Recovery Strategy for a Natural Disaster Scenario
Let’s say a hurricane wipes out your primary office. A well-defined recovery strategy would involve activating your backup data center, perhaps located in a geographically separate region. Pre-arranged communication protocols would ensure employees can connect remotely and continue operations. Critical systems and data would be restored from backups, and temporary office space secured to facilitate a smooth transition back to normal operations. The recovery plan would include provisions for employee safety, communication, and logistical support, ensuring a swift and orderly response to the disaster. Regular drills and simulations would test the plan’s effectiveness and identify areas for improvement. This detailed, proactive approach minimizes disruption and protects the business’s reputation and financial stability.
Communication and Coordination Plan
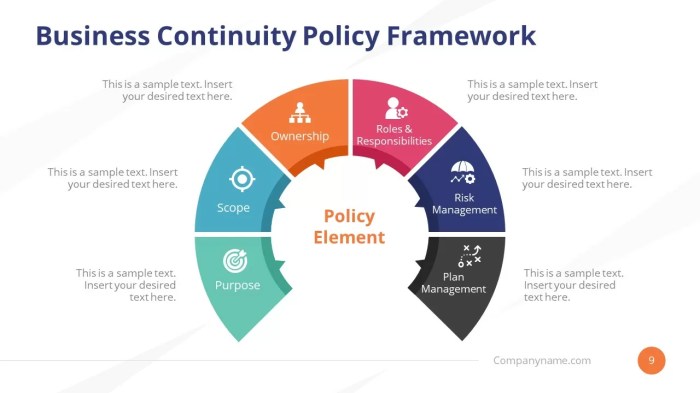
Effective communication is the lifeblood of any successful business continuity plan. Think of it as the nervous system of your organization – when things go sideways, clear and consistent communication is what keeps everyone informed, calm, and working together towards recovery. Without a robust communication plan, even the most meticulously crafted recovery strategies can crumble like a poorly constructed sandcastle in a hurricane.
A well-defined communication plan ensures that critical information reaches the right people at the right time, preventing chaos and fostering a sense of control during a crisis. This, in turn, minimizes disruption, protects your reputation, and speeds up the recovery process. Let’s face it, nobody wants to be scrambling for contact information while their business is literally falling apart.
Key Stakeholders and Communication Channels
Identifying key stakeholders and establishing clear communication channels is paramount. This involves listing all individuals and groups who need to be informed during a disruption, from employees and customers to suppliers, investors, and regulatory bodies. For each stakeholder group, you should define the most appropriate communication channels – email, phone, text message, social media, etc. – considering their preferences and the urgency of the information. For example, a critical security breach would necessitate immediate phone calls to key personnel, while a planned system outage could be communicated via email.
Disseminating Critical Information During an Emergency
Procedures for disseminating critical information during an emergency should be straightforward and easily accessible. This might involve pre-recorded emergency messages, automated email alerts, or a dedicated emergency communication system. Consider using multiple channels to ensure information reaches everyone, and prioritize clear, concise messaging to avoid confusion and panic. Think of it as a well-rehearsed play – everyone knows their lines and their cues. Regular drills and training exercises will ensure everyone understands their roles and responsibilities.
Managing and Tracking Communication During Recovery
A system for managing and tracking communication throughout the recovery effort is crucial. This could involve a central communication hub, such as a dedicated online portal or a shared communication platform, where all updates and information are logged and accessible to authorized personnel. This system should track the dissemination of information, ensuring accountability and transparency. Imagine a central dashboard showing the status of communication efforts – which messages have been sent, who has received them, and any outstanding issues. This helps maintain control and allows for rapid adjustments as needed. Such a system helps prevent duplicated efforts and ensures everyone is on the same page.
Testing and Maintenance
A well-crafted Business Continuity Plan (BCP) is like a finely tuned Swiss watch – precise, reliable, and (hopefully) never needing rescue. But even the most meticulously designed watch requires regular maintenance and the occasional vigorous shake-down. Testing your BCP isn’t just a good idea; it’s the difference between a smooth recovery and a chaotic scramble when disaster strikes. Regular testing ensures your plan is up-to-date, effective, and that your team knows how to use it – all before the pressure is on.
Regular testing of your BCP is paramount. Without it, your meticulously crafted plan becomes nothing more than a dusty document, gathering metaphorical cobwebs in a forgotten corner of your server. Think of it as a fire drill for your entire business operation – you wouldn’t skip those, would you? Testing allows you to identify weaknesses, refine procedures, and ensure everyone understands their roles and responsibilities. It’s about preparedness, not paranoia.
Testing Methodologies
Various methods exist to test the effectiveness of your BCP, each with its own advantages and level of disruption. Choosing the right approach depends on the scale of your operation, the complexity of your plan, and the resources available.
- Tabletop Exercises: These are low-key, discussion-based simulations. Participants gather around a table (or virtually) and walk through various scenarios, identifying potential bottlenecks and communication breakdowns. Think of it as a brainstorming session with a touch of simulated chaos. For example, imagine a scenario where your primary data center is knocked offline by a power outage. In a tabletop exercise, the team would discuss how to activate the backup system, how to communicate with clients, and how to restore critical services. This is relatively inexpensive and less disruptive than other methods.
- Full-Scale Drills: These are more involved simulations that mimic a real-world event. They involve activating parts or all of your BCP, potentially including relocating staff to a backup site, testing data recovery procedures, and engaging with external stakeholders. Consider a full-scale drill simulating a major cyberattack. This would involve activating your incident response plan, testing data backup and recovery procedures, and coordinating with law enforcement and cybersecurity experts. This method is more resource-intensive but provides a more realistic assessment of your preparedness.
- Partial Drills: These are a happy medium between tabletop exercises and full-scale drills. They focus on specific aspects of the BCP, allowing for targeted testing and refinement. For instance, a partial drill might focus solely on the data recovery process, or solely on the communication plan.
BCP Maintenance and Updates
Your business environment is dynamic; it changes constantly. New technologies emerge, regulations shift, and your own operations evolve. To maintain the relevance and effectiveness of your BCP, a dedicated maintenance and update plan is crucial. This isn’t a ‘set it and forget it’ kind of thing.
- Regular Reviews: Schedule regular reviews (e.g., annually or semi-annually) of the entire BCP. This ensures that the plan reflects the current state of your business and addresses any emerging risks.
- Triggered Updates: Trigger updates whenever significant changes occur within the business, such as a merger, acquisition, significant technological upgrade, or a major regulatory change. These events can dramatically impact your operational resilience.
- Designated Responsibility: Assign clear responsibility for BCP maintenance and updates to a specific individual or team. This ensures accountability and prevents the plan from becoming neglected.
Documenting Testing Results and Identifying Areas for Improvement
After each test, meticulously document the results. This isn’t about assigning blame; it’s about identifying areas for improvement. Think of it as a post-mortem for your plan, not for your team.
| Test Type | Date | Scenario | Observed Issues | Recommended Improvements | Action Items | Completion Date |
|---|---|---|---|---|---|---|
| Tabletop Exercise | October 26, 2024 | Power Outage at Primary Data Center | Communication delays between IT and Marketing teams | Implement a new communication protocol using a dedicated messaging platform | Implement new protocol; Training for all relevant personnel | November 30, 2024 |
Training and Awareness
A successful Business Continuity Plan (BCP) isn’t just a document gathering dust on a shelf; it’s a living, breathing strategy that relies heavily on the preparedness and knowledge of your employees. Think of your BCP as a finely tuned orchestra – without properly trained musicians (your employees), the performance (business continuity) will be a cacophony of chaos. Therefore, comprehensive training and awareness programs are not merely recommended, but absolutely crucial for effective BCP implementation. Failing to train your staff is like leaving the fire escape door locked during a fire drill – not a good look.
Employee training plays a vital role in ensuring a smooth transition during a disruption. Well-trained employees understand their roles, responsibilities, and the procedures they must follow to minimize downtime and maintain essential business operations. This understanding fosters confidence, reduces panic, and enables a swift, coordinated response. Imagine the difference between a well-rehearsed team handling a crisis versus a group of bewildered individuals scrambling in the dark. The former scenario is what we aim for.
Training Program Artikel
This training program Artikels key concepts and procedures, ensuring your team is well-equipped to navigate disruptions. The program is designed to be modular and adaptable to different roles and responsibilities within the organization. We’re aiming for a level of preparedness that would make even the most seasoned disaster movie director impressed.
- Module 1: Introduction to BCP – This module provides a general overview of the BCP, its purpose, and the importance of employee participation. It includes a fun, engaging quiz to test understanding and retention.
- Module 2: Understanding Your Role – This module focuses on individual roles and responsibilities during a disruption. Employees will learn their specific tasks and how they contribute to the overall continuity plan. A realistic scenario-based exercise will help solidify this knowledge.
- Module 3: Communication Protocols – This module covers communication procedures, including reporting channels, emergency contact information, and the use of designated communication tools. A mock emergency drill, complete with simulated communication failures and recoveries, will enhance learning.
- Module 4: Recovery Procedures – This module Artikels the steps to take during and after a disruption, including data backup and recovery, system restoration, and alternative work arrangements. A hands-on workshop involving practical application of these procedures will be invaluable.
- Module 5: Security and Compliance – This module covers relevant security protocols and compliance requirements during a business disruption. This ensures your business remains secure even in times of crisis.
Methods for Ensuring Employee Awareness
Maintaining ongoing employee awareness is crucial for the long-term success of the BCP. Regular reinforcement of key concepts and procedures is essential to prevent complacency and ensure everyone remains prepared. Think of it as regular maintenance on your BCP – vital for optimal performance.
- Regular refresher training sessions: Short, focused sessions held periodically to review key information and address any changes to the BCP.
- Interactive workshops and simulations: Hands-on activities that allow employees to practice their roles and responsibilities in a safe and controlled environment.
- Email reminders and newsletters: Periodic communications that highlight important information and remind employees of their responsibilities.
- Intranet resources and online training modules: Easily accessible resources that employees can refer to at any time.
- Gamification: Incorporating game mechanics into training to make learning more engaging and memorable.
Examples of Training Materials
Effective training materials should be engaging, informative, and easily accessible. A variety of formats cater to different learning styles. Think of it as a buffet of knowledge – something for everyone.
- Comprehensive BCP Manual: A detailed guide outlining the plan’s procedures, contact information, and roles and responsibilities. This manual should be clear, concise, and easily navigable, with plenty of visuals to avoid information overload.
- Interactive Presentations: Engaging presentations using slides, images, and videos to illustrate key concepts and procedures. Think of it as a captivating TED Talk about business continuity.
- Short Explainer Videos: Concise videos explaining specific procedures or aspects of the BCP. These videos should be short and to the point, focusing on one key aspect at a time. Think of them as short, impactful commercials for preparedness.
- Scenario-Based Training Modules: Interactive modules that simulate real-world scenarios, allowing employees to practice their responses in a safe environment. These modules should be challenging yet realistic, pushing employees to think critically and problem-solve effectively.
- Tabletop Exercises: Simulated exercises that involve a small group of employees discussing potential scenarios and developing response strategies. These are ideal for reinforcing teamwork and communication skills in a low-pressure environment.
Technology Considerations
Let’s face it, in today’s digital age, your business is only as resilient as its technology. A robust technology strategy isn’t just a nice-to-have; it’s the backbone of any successful business continuity plan. Without it, you’re essentially playing business Jenga with a whole lot of expensive dominoes.
Technology plays a pivotal role in ensuring business continuity by providing the tools and infrastructure necessary to maintain operations during and after a disruptive event. This involves safeguarding critical data, applications, and infrastructure, enabling swift recovery, and minimizing downtime. Think of it as your digital life raft in a stormy sea of unforeseen circumstances.
Key Technological Components Requiring Protection and Recovery
Protecting your critical technological assets is paramount. Failure to do so can lead to significant financial losses, reputational damage, and even legal repercussions. Imagine the chaos if your customer database vanished into the digital ether! This section details the crucial components that need your unwavering attention.
- Data: This includes customer information, financial records, intellectual property, and operational data. Think of it as the lifeblood of your business – without it, you’re essentially a body without a soul (or a business without a bottom line).
- Applications: These are the software programs your business relies on daily. From CRM systems to accounting software, their unavailability can grind operations to a halt. Imagine trying to run a bakery without an oven – not a pretty picture.
- Hardware: This encompasses servers, workstations, network equipment, and other physical components. A hardware failure can cripple your entire IT infrastructure, leaving you stranded in a digital desert.
- Infrastructure: This includes your network, internet connectivity, and data centers. A disruption here can impact all aspects of your operations, potentially leading to widespread chaos and customer dissatisfaction.
Disaster Recovery Solutions
Disaster recovery isn’t about hoping for the best; it’s about planning for the worst. Investing in robust disaster recovery solutions is an investment in your business’s future. It’s like having a spare tire for your business vehicle – you hope you never need it, but you’ll be eternally grateful when you do.
- Cloud Computing: Cloud-based solutions offer scalability, redundancy, and accessibility. Think of it as having a digital backup of your entire business, stored safely in a secure, offsite location. Major players like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) offer a range of services to help you achieve this.
- Data Backups: Regular data backups are crucial. This is your insurance policy against data loss. Employing the 3-2-1 backup rule (three copies of data, on two different media, with one copy offsite) is a good starting point. It’s better to be overly cautious than to regret it later.
- Data Replication: Replicating your data to a secondary location ensures business continuity in case of a primary site failure. It’s like having a mirror image of your business, ready to take over seamlessly if needed.
Technological Safeguards to Mitigate Risks
Implementing appropriate technological safeguards is crucial to mitigating risks and ensuring business continuity. These measures act as your digital shield, protecting your business from various threats. Think of them as your business’s digital bodyguards.
- Firewall and Intrusion Detection Systems (IDS): These systems protect your network from unauthorized access and malicious attacks. They’re like the bouncers at a nightclub, keeping the undesirables out.
- Antivirus and Antimalware Software: These programs protect your systems from viruses, malware, and other threats. They’re your digital immune system, fighting off infections before they can cause damage.
- Data Encryption: Encrypting sensitive data protects it from unauthorized access, even if it’s stolen or lost. It’s like putting your valuables in a safe – even if someone breaks in, they won’t be able to access your treasures.
- Regular Security Audits and Penetration Testing: Regular security assessments help identify vulnerabilities and weaknesses in your systems. It’s like a yearly check-up for your business’s digital health.
Legal and Regulatory Compliance
Navigating the legal landscape of business continuity might seem like traversing a minefield blindfolded while juggling flaming torches, but fear not! Understanding and adhering to relevant laws and regulations is not only crucial for avoiding hefty fines and reputational damage, but also for ensuring the smooth and legal operation of your business during and after a disruption. This section will illuminate the path to legal compliance within your Business Continuity Plan (BCP).
The implications of non-compliance can range from minor inconveniences to major catastrophes. Imagine the fallout from a data breach that violates GDPR regulations – hefty fines, damaged customer trust, and potential legal battles. Failing to meet industry-specific regulations, like HIPAA for healthcare providers, could lead to severe penalties and the loss of licenses. Essentially, non-compliance is a recipe for disaster, both financially and reputationally. It’s like forgetting to put the lid on a pot of boiling water – you’re bound to get burned.
Relevant Legal and Regulatory Requirements
Identifying relevant legal and regulatory requirements is the first step in ensuring compliance. This involves a thorough review of all applicable laws and regulations impacting your specific industry and geographical location. This could include data protection laws (like GDPR or CCPA), industry-specific regulations (like HIPAA or SOX), and general business regulations (like those related to employment law or environmental protection). Failing to conduct this comprehensive review is akin to building a house on a foundation of sand – eventually, everything will crumble.
Implications of Non-Compliance
Non-compliance can result in a wide range of consequences, including significant financial penalties, legal action, reputational damage, and even business closure. For example, a company failing to comply with data protection regulations could face substantial fines and a loss of customer trust. In some cases, non-compliance can lead to criminal charges. The cost of non-compliance often far outweighs the cost of implementing robust compliance measures. It’s like choosing to ignore a nagging toothache – eventually, it will require a far more extensive and costly solution.
BCP and Legal Obligations
A well-structured BCP can be a powerful tool for demonstrating compliance with legal and regulatory obligations. By outlining procedures for data backup and recovery, ensuring business continuity in the event of a disaster, and documenting compliance efforts, organizations can proactively mitigate risks and demonstrate their commitment to legal compliance. It’s like having a detailed roadmap that shows regulators you’ve thought of everything and are prepared for anything.
Methods for Ensuring Compliance
Several methods can ensure ongoing compliance with relevant regulations. Regular audits, employee training programs, and the implementation of robust internal control systems are crucial. Staying informed about changes in legislation and incorporating these changes into your BCP is equally vital. This continuous process of review and update is like regularly servicing your car – preventative maintenance prevents costly breakdowns down the road. Think of it as your legal and regulatory “tune-up”.
Final Summary
So, there you have it – your comprehensive Business Continuity Planning Guide. While we can’t guarantee immunity from every potential disaster (sorry, we can’t control rogue asteroids), we *can* guarantee that with a well-defined plan, your business will be better equipped to navigate the inevitable bumps in the road. Remember, a little preparation goes a long way in ensuring your business’s long-term success and peace of mind. Now go forth and conquer (the challenges, not the world – unless you’re feeling ambitious).
Key Questions Answered
What’s the difference between Business Continuity Planning and Disaster Recovery?
Disaster Recovery focuses on restoring IT systems after a disruption, while Business Continuity Planning is a broader strategy encompassing all aspects of keeping the business operational, including non-IT functions.
How often should my BCP be tested?
The frequency of testing depends on your risk profile and industry regulations. At a minimum, annual testing is recommended, with more frequent testing for critical functions.
Who should be involved in creating a BCP?
A cross-functional team representing key business areas, IT, and senior management is essential for a comprehensive and effective plan.
What if my business is too small for a BCP?
Even small businesses benefit from a BCP. A simple plan addressing key risks can significantly mitigate disruption and ensure survival.