Business Continuity Planning Guide: Let’s face it, disasters happen. Whether it’s a rogue asteroid (unlikely, but hey, we’re planning!), a cyberattack orchestrated by mischievous kittens, or a sudden, inexplicable surge in demand for novelty rubber chickens, a robust business continuity plan is your secret weapon against chaos. This guide will walk you through creating a plan that’s not just effective, but also surprisingly entertaining (we promise).
We’ll cover everything from identifying potential threats (think disgruntled employees with access to the coffee machine) to developing recovery strategies that are as resilient as a cockroach in a nuclear fallout shelter. We’ll delve into risk assessment, business impact analysis, and communication plans so clear and concise, even your grandma could understand them. Prepare to be amazed by the power of preparedness!
Introduction to Business Continuity Planning
Let’s face it, nobody *wants* to think about their business going belly up. But ignoring the potential for disaster is like ignoring a rogue elephant charging towards your perfectly curated office – it’s not a good look. Business Continuity Planning (BCP) isn’t about being a doom and gloom merchant; it’s about being prepared, proactive, and frankly, rather clever. It’s about ensuring your business can weather the storm, whatever that storm may be, and emerge smelling of roses (or at least, not smelling of burnt toast).
Business continuity is the ability of an organization to continue delivering products or services at acceptable predefined levels following a disruptive incident. Its importance? Well, let’s just say the alternative isn’t pretty. A lack of robust planning can lead to significant financial losses, reputational damage, loss of market share, and even complete business failure. In short, it can turn your meticulously crafted business empire into a pile of rubble faster than you can say “Act of God.”
Potential Consequences of Inadequate Planning
The consequences of lacking a robust business continuity plan are as varied as the disruptions themselves, but they all boil down to one thing: significant pain. Financial losses can range from minor inconveniences to utter bankruptcy, depending on the severity and duration of the disruption. Reputational damage can be equally devastating, with customers losing faith and partners jumping ship faster than rats abandoning a sinking vessel. Losing market share to more prepared competitors is another common consequence, as is the potential for legal repercussions and regulatory penalties. Imagine the headlines: “[Company Name] Collapses After Failing to Plan for a Simple Power Outage!” Not exactly a career highlight reel.
Examples of Business Disruptions and Their Impact
Let’s get specific. Imagine a hurricane wiping out your primary data center (data centers, much like cats, are surprisingly prone to flooding). Or a cyberattack crippling your IT systems, leaving you unable to process orders or access crucial customer information. Perhaps a key employee unexpectedly quits, leaving a critical knowledge gap. Or maybe a global pandemic forces a sudden and unexpected shift to remote work, exposing weaknesses in your communication and collaboration infrastructure. Each scenario has the potential to cause significant disruption, and the impact varies depending on the preparedness of the business. A well-prepared business might experience a minor inconvenience; an unprepared one might face a complete collapse.
Best Practices for Establishing a Strong Business Continuity Foundation
Building a solid BCP foundation isn’t rocket science (though it might feel like it sometimes). It starts with a thorough risk assessment, identifying potential threats and vulnerabilities. Next, develop recovery strategies for each identified risk, focusing on critical business functions. Regular testing and updates are crucial – a plan that gathers dust is about as useful as a chocolate teapot. Finally, ensure that your plan is communicated effectively to all employees, so everyone knows their role in the event of a disruption. Think of it as a well-rehearsed fire drill, but instead of fire, it’s a rogue elephant (or a pandemic, or a cyberattack… you get the idea).
Risk Assessment and Analysis
Let’s face it, running a business is a bit like tightrope walking on a unicycle – exhilarating, but potentially disastrous. A robust risk assessment isn’t just a box-ticking exercise; it’s your safety net. This section will guide you through identifying, analyzing, and prioritizing those potential pitfalls that could send your carefully balanced business tumbling. Think of it as your pre-flight checklist before taking off on the entrepreneurial rollercoaster.
Identifying and analyzing potential threats is the first step in securing your business’s future. Failing to do so is like sailing without a map – you might reach your destination, but the journey will be significantly more perilous and potentially fruitless. This process involves a systematic approach to pinpoint vulnerabilities and assess their potential impact. We’ll explore a variety of methods to ensure a comprehensive understanding of your risk landscape.
Potential Threats to Business Operations
Identifying potential threats requires a wide-ranging perspective. Consider the full spectrum of possibilities, from the seemingly obvious to the surprisingly subtle. This isn’t about predicting the future (though wouldn’t that be handy?), but rather about proactively considering what *could* go wrong. A thorough assessment should include natural disasters (floods, earthquakes, hurricanes – you get the picture), cyberattacks (ransomware, phishing scams, data breaches – the digital dark arts), pandemics (let’s just say, we’ve all had some experience with this one!), and various other operational disruptions (supplier issues, equipment failures, even a rogue stapler). Don’t forget about the less dramatic but equally disruptive events, like a key employee leaving unexpectedly or a sudden shift in market demand.
Methodology for Assessing Likelihood and Impact
Once you’ve identified your potential threats, it’s time to quantify them. This involves assessing the likelihood of each threat occurring and the potential impact if it does. Likelihood can be estimated using historical data, industry benchmarks, and expert opinions. Impact can be measured by considering financial losses, reputational damage, operational downtime, and legal repercussions. For example, a highly likely but low-impact threat might be a minor power outage, while a low-likelihood but high-impact threat could be a major cyberattack resulting in significant data loss.
Risk Matrix for Prioritizing Threats
Now for the fun part: organizing your threats into a visual representation. A risk matrix is a simple yet powerful tool to prioritize threats based on their likelihood and impact. Typically, this is a two-by-two matrix, with likelihood on one axis and impact on the other. Each threat is plotted on the matrix, allowing you to quickly identify high-priority risks that require immediate attention. For example, a threat with high likelihood and high impact would fall into the “critical” quadrant, demanding immediate mitigation strategies. A threat with low likelihood and low impact would be considered low priority, but still worth noting. Think of it as a game of risk management Tetris, fitting all the threats into their appropriate severity levels.
Potential Business Vulnerabilities
This involves a detailed examination of your business’s internal workings. Are your systems adequately secured? Do you have robust backup and recovery plans? Are your supply chains resilient? Do you have a clear succession plan for key personnel? Identifying these weaknesses is crucial, as they represent entry points for many of the threats you’ve already identified. This process often involves reviewing existing policies, procedures, and technology infrastructure. Consider engaging external experts to conduct a thorough vulnerability assessment – a fresh pair of eyes can often spot things you might miss.
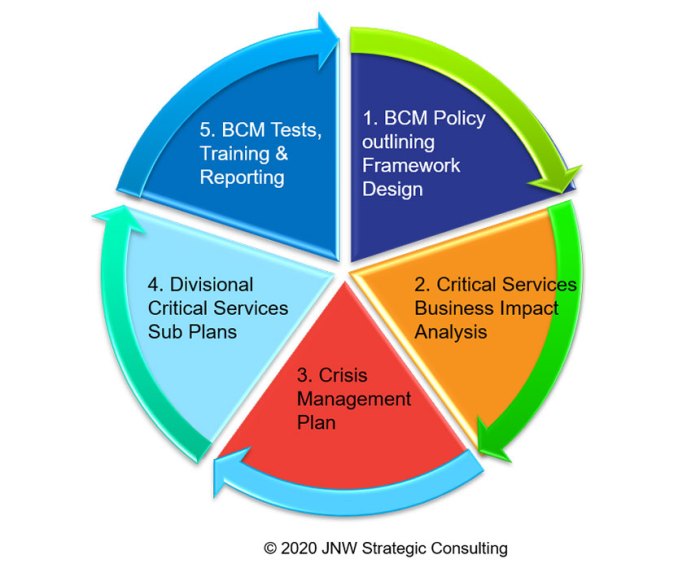
Business Impact Analysis (BIA)
Let’s face it, nobody *wants* to think about what happens when the metaphorical (or literal!) fan hits the proverbial (or actual!) ceiling. But a Business Impact Analysis (BIA) isn’t about dwelling on disaster; it’s about strategically preparing for the inevitable hiccup, the unexpected wrench in the works, the… well, you get the picture. A BIA is your roadmap to navigating disruption, ensuring your business can weather the storm and emerge, not just unscathed, but possibly even stronger.
The purpose of a BIA is to identify critical business functions, assess their vulnerabilities, and determine the potential impact of disruptions. Think of it as a pre-emptive strike against chaos. The process involves systematically evaluating each function, pinpointing its dependencies (both internal and external), and quantifying the potential financial, operational, and reputational losses should things go sideways. It’s a bit like a financial health check, but for your entire operation. The better you understand your weaknesses, the better prepared you are to strengthen them.
Critical Business Function Identification and Dependency Mapping
This stage involves identifying your business’s most crucial functions – the ones that, if disrupted, would significantly impact your bottom line or ability to operate. This might include things like customer service, order fulfillment, payroll processing, or even the seemingly mundane (but critically important) function of keeping the coffee machine running. For each function, you’ll map out its dependencies – the other functions, systems, or resources it relies on. For instance, order fulfillment depends on inventory management, shipping, and payment processing. A disruption in any of these dependencies will impact the main function. Consider using a simple, yet effective, flowchart to visualize these dependencies. A visual representation will often illuminate hidden connections and potential vulnerabilities you might not otherwise spot.
Quantifying the Impact of Disruptions
Now for the slightly less fun part: quantifying the impact. This involves estimating the financial losses, potential legal ramifications, and reputational damage associated with disruptions to each critical function. For example, a disruption to your customer service function could lead to lost sales, increased customer churn, and negative online reviews. Consider using metrics such as revenue loss per hour of downtime, cost of recovery, and potential fines for non-compliance. Don’t be afraid to get creative here. If a key supplier is down, what’s the cost of finding a replacement, including expedited shipping? A well-defined process can make all the difference in the world.
Prioritized List of Critical Business Functions
Once you’ve identified and quantified the impact of disruptions on your critical business functions, it’s time to prioritize them. This will help you focus your resources on the areas that need the most attention. The prioritization is often based on a combination of factors, including the potential financial impact, the likelihood of disruption, and the recovery time objective (RTO) and recovery point objective (RPO). Let’s use a table to illustrate this.
| Function | Dependency | Recovery Time Objective (RTO) | Recovery Point Objective (RPO) |
|---|---|---|---|
| Customer Service | Phone System, CRM Software, Staff | 4 hours | 24 hours |
| Order Fulfillment | Inventory Management, Shipping, Payment Processing | 24 hours | 72 hours |
| Payroll Processing | HR System, Banking System | 24 hours | 24 hours |
| Website | Server, Internet Connection, Content Management System | 1 hour | 1 hour |
Remember, RTO is the maximum tolerable downtime before significant business impact occurs, while RPO is the maximum acceptable data loss in the event of a disruption. These are crucial for determining resource allocation and recovery strategies. The prioritization will guide your efforts to mitigate risks and ensure business continuity.
Developing a Recovery Strategy
So, you’ve identified your risks and the potential impact of a disruption. Congratulations! You’ve navigated the treacherous waters of risk assessment and now you’re ready for the thrilling next step: developing a recovery strategy. Think of this as your business’s escape plan from a fiery dragon (or, you know, a less dramatic event like a power outage). The goal is to get back on your feet as quickly and smoothly as possible, minimizing disruption and preventing a complete meltdown.
This section details the strategies for recovering critical business functions after a disruption. We’ll explore redundancy, failover mechanisms, and the creation of a detailed recovery plan, ensuring your business can weather any storm (metaphorically speaking, of course. Actual storms require a separate, equally well-crafted plan).
Redundancy and Failover Mechanisms, Business Continuity Planning Guide
Redundancy and failover mechanisms are the unsung heroes of business continuity. They’re like having a backup singer ready to step in when the lead vocalist loses their voice (or their internet connection). Redundancy involves creating duplicate systems or processes so that if one fails, another is immediately available. Failover mechanisms automatically switch to the backup system when the primary system goes down. This seamless transition minimizes downtime and ensures business continuity. Imagine a company’s database replicated across multiple servers in different geographical locations. If one server crashes, the others instantly take over, ensuring uninterrupted access to crucial data. This prevents a catastrophic data loss and maintains business operations without a hitch.
Recovery Plan Design
A well-designed recovery plan is more than just a list of “to-dos”; it’s a meticulously crafted roadmap guiding your business back to stability after a disruption. This plan should include detailed procedures for each critical function, outlining the steps to be taken, the personnel responsible, and the resources required. It’s crucial to regularly test and update this plan to ensure its effectiveness and relevance. Consider a scenario where a major software system fails. The recovery plan should detail the steps to restore the system, including restoring data from backups, notifying affected users, and reassigning tasks to ensure minimal disruption to workflows. This plan should be a living document, regularly updated to reflect changes in technology, personnel, and business processes.
Examples of Recovery Strategies
Choosing the right recovery strategy depends on factors such as the criticality of the function, the acceptable downtime, and the budget. Here are some common options:
- Hot Site: A fully equipped and operational facility ready to take over immediately. It’s like having a fully furnished apartment waiting for you if your own home burns down (again, metaphorically speaking). This option minimizes downtime but is the most expensive.
- Cold Site: A basic facility with essential infrastructure but lacking operational equipment. It’s like having an empty apartment – you’ll need to bring your own furniture and get it up and running. This option is the cheapest but requires more time to become operational.
- Warm Site: A compromise between hot and cold sites. It has some basic equipment and infrastructure pre-configured, reducing setup time compared to a cold site. Think of it as a partially furnished apartment – you have some furniture, but you might need to add a few things to make it fully functional. This provides a balance between cost and recovery time.
Communication and Coordination Plan
Let’s face it, during a crisis, clear communication isn’t just a good idea – it’s the difference between a controlled descent and a catastrophic freefall. A well-defined communication plan is your lifeline, ensuring everyone stays informed, coordinated, and (hopefully) relatively calm amidst the chaos. Think of it as your business’s emergency broadcast system, but with less static and more actionable information.
Effective communication during a crisis minimizes confusion, prevents misinformation from spreading faster than wildfire, and allows for a quicker, more efficient recovery. It’s about getting the right information to the right people at the right time – a deceptively simple goal that requires meticulous planning. Imagine trying to herd cats during a hurricane; a solid communication plan is your herding stick.
Communication Plan Roles and Responsibilities
This section Artikels the crucial roles and responsibilities within your communication plan. It’s not about assigning blame, but about ensuring clear lines of accountability and preventing the dreaded “it wasn’t my job” syndrome. We’ll define key personnel and their specific tasks.
- Communication Manager: The point person for all communication-related activities, responsible for overseeing the entire plan’s execution. Think of them as the conductor of your communication orchestra.
- Spokesperson: The designated individual who interacts with external stakeholders (media, customers, etc.). This person needs to be calm, collected, and capable of delivering information clearly and concisely, even under pressure.
- Internal Communication Team: A group responsible for disseminating information to employees. This team should be readily available to answer questions and provide support.
- Technical Support Team: Ensures the smooth operation of communication channels and systems. They’re the IT heroes who keep the lines open.
Notification Procedures
Establishing clear notification procedures is paramount. Think of it as creating a well-rehearsed fire drill, but for a wider range of potential disasters. The speed and efficiency of your notifications will directly impact the effectiveness of your response.
| Stakeholder Group | Notification Method | Example |
|---|---|---|
| Employees | Email, SMS, Internal Messaging System | Automated email alert with instructions and contact information. |
| Customers | Website updates, Email, SMS, Social Media | Website banner alerting customers of temporary service disruptions, with estimated restoration time. |
| Stakeholders (Investors, Regulators) | Email, Phone Calls, Press Releases | Formal press release announcing the incident and outlining the company’s response. |
Maintaining Communication Channels
Maintaining open communication channels during a disruption is crucial, even if it’s just to say, “We’re working on it!” This requires redundancy and backup plans. Consider it like having a spare tire – you hope you never need it, but you’re glad you have it when you do.
This involves identifying potential points of failure and implementing alternative communication methods. For example, having a backup satellite phone system if regular phone lines are down, or utilizing social media platforms for updates if email servers are inaccessible. A diverse communication strategy acts as a safety net. Remember, silence breeds anxiety; consistent communication, even if it’s just to acknowledge the disruption, builds trust and confidence.
Testing and Maintenance
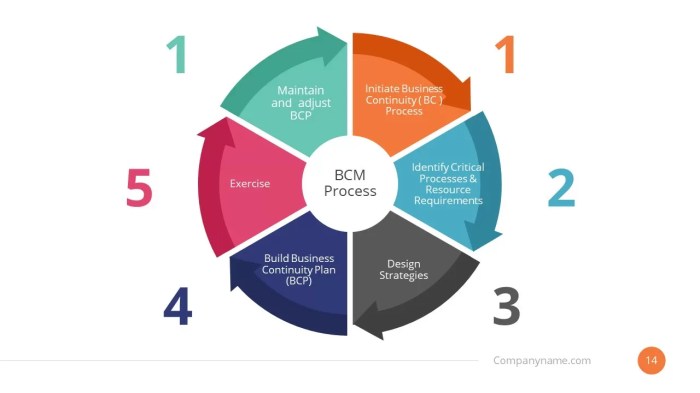
A well-crafted Business Continuity Plan (BCP) is like a finely tuned Swiss watch – beautiful in its complexity, but utterly useless if it’s never wound. Regular testing and maintenance are not mere suggestions; they are the lifeblood of a successful BCP, ensuring it remains relevant, effective, and ready to spring into action when disaster strikes (or, let’s be honest, when the coffee machine breaks down). Without consistent upkeep, your meticulously crafted plan becomes nothing more than a dusty tome gathering cobwebs in a forgotten corner.
Regular testing and maintenance ensure the BCP remains a dynamic, living document capable of navigating the ever-shifting sands of operational challenges. This process validates assumptions, identifies gaps, and refines procedures, ensuring the plan is truly resilient and fit for purpose. Ignoring this crucial step is akin to buying a fire extinguisher and never checking if it’s actually charged – a potentially disastrous oversight.
Types of Testing
Different testing methods provide various levels of realism and engagement, allowing organizations to assess their preparedness at different scales. The choice of testing method depends on the complexity of the plan, available resources, and the organization’s risk tolerance. It’s a bit like choosing the right tool for the job – a tiny screwdriver won’t fix a broken engine, and vice versa.
| Test Type | Description | Advantages | Disadvantages |
|---|---|---|---|
| Tabletop Exercises | A facilitated discussion involving key personnel walking through various disaster scenarios. Participants analyze responses and identify potential weaknesses. | Cost-effective, relatively low time commitment, good for initial testing and identifying gaps. | Lacks the realism of a full-scale simulation; reliance on participant memory and recall. |
| Full-Scale Simulations | A complete, real-world test of the BCP, often involving multiple departments and external stakeholders. This may include activating actual recovery procedures and relocating to a secondary site. | Provides a comprehensive assessment of plan effectiveness; identifies unforeseen challenges and bottlenecks. | Expensive, time-consuming, requires significant resources and coordination. |
Documenting Test Results and Identifying Areas for Improvement
After each test, a thorough documentation process is crucial. This isn’t just about ticking boxes; it’s about learning from the experience. Think of it as a post-mortem for your BCP – identifying what went well, what went wrong, and how to improve for next time. A well-documented test provides valuable insights into the plan’s strengths and weaknesses, paving the way for targeted improvements and adjustments.
A standardized reporting format should be used, including a detailed description of the scenario tested, a record of actions taken, identification of successes and failures, and a list of recommended improvements. This documentation serves as a historical record, tracking the evolution of the BCP and demonstrating a commitment to continuous improvement. Imagine it as a detailed case study of your BCP’s performance under pressure, providing invaluable data for future iterations.
Scheduling Regular Plan Reviews and Updates
The business landscape is constantly changing, making regular plan reviews and updates essential. Think of your BCP as a living organism; it needs regular nourishment and adjustments to survive and thrive. A rigid, outdated plan is practically useless in a dynamic environment.
A formal schedule should be established, with regular reviews (e.g., annually) and updates as needed (e.g., after significant changes in the business, technology, or regulatory environment). These reviews should include a comprehensive assessment of the plan’s relevance, effectiveness, and alignment with the organization’s current objectives and risk profile. Consider scheduling these reviews alongside other relevant business planning cycles to streamline the process and maximize efficiency. For example, reviewing the BCP concurrently with the annual risk assessment could create synergies and efficiency.
Training and Awareness
Let’s face it, a Business Continuity Plan (BCP) gathering dust on a shelf is about as useful as a chocolate teapot in a hurricane. To truly be effective, your BCP needs to be ingrained in the very DNA of your organization. This means a robust training and awareness program is not just a nice-to-have, it’s a must-have – the life raft in the stormy seas of disaster.
A well-structured training program ensures everyone knows their role in keeping the business afloat during a crisis. Imagine the chaos if, during a power outage, everyone just stares blankly at their darkened screens, waiting for instructions that never come! This section Artikels how to avoid such a scenario and create a team ready for anything.
Employee Training Program Design
The design of your training program should be as unique as your business. Consider your organization’s size, structure, and the specific risks you face. A small, tightly-knit team will require a different approach than a large multinational corporation. The key is to make the training engaging, relevant, and memorable. Think interactive workshops, not dull PowerPoint presentations. Role-playing scenarios can be particularly effective – allowing employees to practice their responses in a safe environment. For example, simulate a server failure and have employees practice their recovery procedures. This hands-on approach makes the training far more impactful than simply reading a manual. Consider incorporating quizzes and games to test comprehension and retention. Remember, the goal is to transform your employees from passive readers of the BCP to active participants in its execution.
Business Continuity Plan Educational Materials
Creating effective educational materials is key to fostering understanding and buy-in. Forget lengthy, jargon-filled manuals – aim for clear, concise, and easily digestible information. Use infographics, short videos, and even comic strips to explain complex concepts in an engaging way. Imagine a short, animated video demonstrating the step-by-step process of activating the emergency communication system – far more memorable than a dense paragraph of instructions. Remember to tailor the materials to different levels of understanding, ensuring that everyone, from the CEO to the newest intern, can grasp the essentials.
Promoting Plan Awareness and Importance
Don’t let your BCP become a forgotten document. Regular reminders are crucial. Consider incorporating BCP awareness into regular team meetings, newsletters, and company-wide announcements. Use real-life examples (both internal and external) to illustrate the importance of the plan. For instance, discussing how a competitor handled a similar crisis – highlighting their successes and failures – can be a powerful learning tool. A well-placed poster in the break room might seem small, but it can be a constant, subtle reminder of the plan’s existence and importance. The goal is to create a culture of preparedness, where the BCP is not seen as a theoretical document, but a practical tool essential for the business’s survival.
Best Practices for Employee Preparedness
Regular drills and exercises are paramount. Think fire drills, but for every conceivable crisis. These drills should test the plan’s effectiveness and identify areas for improvement. Feedback from these exercises should be actively sought and incorporated into the plan. Furthermore, provide employees with readily available resources – such as a quick-reference guide or a dedicated contact person – to ensure they can access the necessary information quickly and easily during a crisis. Consider establishing a buddy system, pairing experienced employees with newer ones, to foster knowledge sharing and mentorship. This collaborative approach builds a strong, resilient team, ready to face any challenge. Regular refresher training, perhaps annually or bi-annually, keeps everyone up-to-date and engaged, preventing the BCP from becoming outdated or irrelevant.
Technology Considerations
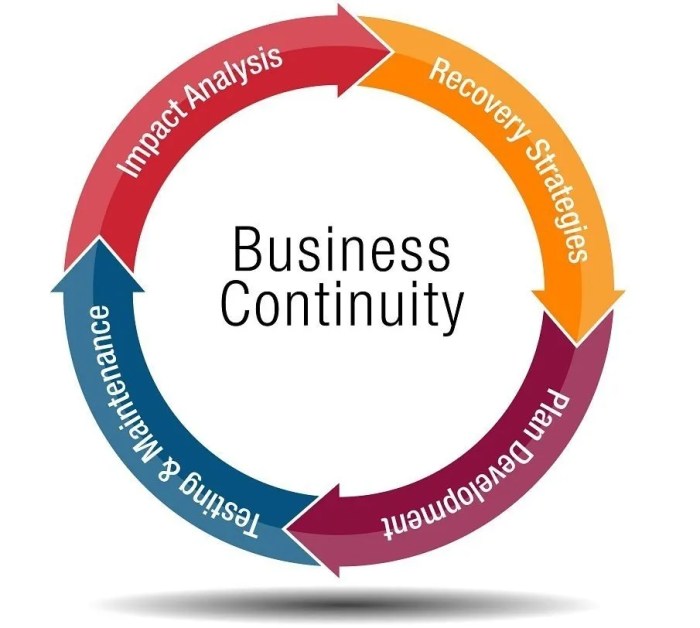
Let’s face it, in today’s digital age, your business is only as resilient as its technology. A robust technology infrastructure isn’t just a nice-to-have; it’s the lifeblood of business continuity. Without it, you’re facing a potential disaster of epic proportions – think less “mild inconvenience” and more “apocalyptic data loss.” So, buckle up, because we’re about to explore how technology can be your knight in shining armor (or at least your very dependable IT guy).
Technology plays a pivotal role in supporting business continuity by enabling rapid recovery from disruptions, minimizing downtime, and ensuring the continued availability of critical business functions. Imagine a world without instant communication, secure data storage, or the ability to seamlessly switch operations to a remote location. Sounds… chaotic, right? That’s why a well-planned technology strategy is paramount to surviving – and thriving – during unexpected events.
Cloud Computing for Enhanced Recovery
Cloud computing offers a powerful arsenal of tools for enhancing recovery capabilities. By migrating critical applications and data to the cloud, businesses can access their resources from anywhere with an internet connection, ensuring operational continuity even if their primary office is rendered unusable (think sudden alien invasion, or, you know, a slightly less dramatic power outage). The scalability and redundancy inherent in cloud services also provide a safety net, allowing businesses to quickly scale resources up or down based on demand, ensuring smooth operations even under pressure. For example, a retail company could leverage cloud-based point-of-sale systems to continue processing transactions during a natural disaster, minimizing revenue loss and maintaining customer satisfaction.
Data Backup and Disaster Recovery Strategies
Think of data backups as your business’s insurance policy against the inevitable. Regular, comprehensive data backups are crucial for restoring operations after a disruption. Multiple backup copies stored in geographically diverse locations (e.g., on-site, off-site, and cloud-based) further enhance resilience. Disaster recovery plans, which detail the steps to restore systems and data after a major incident, should be meticulously crafted and regularly tested. A well-defined plan might involve restoring data from a cloud-based backup to a secondary data center, ensuring minimal downtime. Consider a scenario where a company’s primary server room is flooded. With a robust backup and recovery strategy, they could be back online within hours, rather than weeks.
Protecting Critical Data and Systems
Protecting your critical data and systems requires a multi-layered approach. This includes implementing robust security measures such as firewalls, intrusion detection systems, and encryption to safeguard against unauthorized access and cyberattacks. Regular security audits and vulnerability assessments help identify and address potential weaknesses before they can be exploited. Access control mechanisms, including role-based access control (RBAC), limit access to sensitive data based on individual roles and responsibilities, minimizing the risk of data breaches. For instance, a financial institution might use multi-factor authentication and encryption to protect customer data, preventing unauthorized access and ensuring compliance with regulations.
Securing Technology Infrastructure Against Disruptions
Securing your technology infrastructure involves more than just firewalls and antivirus software. It encompasses a holistic approach to risk management, including physical security measures to protect hardware from theft or damage, redundancy planning to ensure system availability during outages, and comprehensive disaster recovery plans to guide recovery efforts. Regular testing of backup and recovery procedures ensures that plans are effective and that personnel are adequately trained. Consider a scenario where a company experiences a power outage. Having redundant power sources, such as generators, and a well-defined plan for switching to them can minimize downtime and prevent data loss.
Legal and Regulatory Compliance: Business Continuity Planning Guide
Navigating the legal landscape of business continuity might seem like traversing a minefield blindfolded while juggling flaming bowling pins, but fear not! A well-structured plan can transform this potentially perilous journey into a surprisingly smooth stroll. This section will illuminate the critical interplay between your business continuity plan and the legal and regulatory requirements that govern your operations.
Understanding the legal and regulatory requirements related to business continuity is paramount to avoiding hefty fines and potential lawsuits. Failure to comply can result in anything from minor inconveniences to major disruptions, even potentially leading to the demise of your business. Therefore, a robust plan must explicitly address these obligations, ensuring compliance and mitigating potential legal risks.
Relevant Legal and Regulatory Requirements
Identifying relevant legislation is the first step. This involves a thorough review of all applicable laws and regulations at the local, national, and international levels. Consider industry-specific regulations, data protection laws (like GDPR or CCPA), environmental regulations, and any sector-specific compliance mandates. For example, a financial institution will have far more stringent requirements than a small bakery. A comprehensive checklist, regularly updated, is crucial for staying ahead of the curve. Think of it as your legal “to-do” list for disaster preparedness.
Addressing Compliance Obligations in the Business Continuity Plan
The business continuity plan should explicitly detail how the organization will maintain compliance with all relevant laws and regulations during and after a disruptive event. This isn’t just about ticking boxes; it’s about demonstrating a proactive commitment to legal adherence. For instance, if your company handles sensitive personal data, the plan must Artikel procedures for maintaining data security and privacy even in the face of a system failure or cyberattack. This might include procedures for secure data backup and recovery, and notification protocols in case of a data breach. The plan should also clearly identify responsible parties for compliance and the escalation path for any issues.
Potential Legal Implications of Business Disruptions
Business disruptions can have far-reaching legal consequences. Consider contract breaches, failure to meet regulatory deadlines, liability for damages, and potential lawsuits from customers or partners. For example, a delay in fulfilling a crucial contract due to a natural disaster could lead to significant legal battles and financial penalties. The plan should proactively address these potential issues, outlining strategies for mitigating risk and managing legal liabilities. This might involve having pre-negotiated contract clauses addressing force majeure events or maintaining robust insurance coverage.
Procedures for Ensuring Compliance
Implementing robust procedures is key to maintaining ongoing compliance. This includes regular audits of the plan itself to ensure it aligns with current regulations and best practices. Training programs for employees on their roles and responsibilities in maintaining compliance are also essential. Consider regular reviews of relevant legislation and incorporating any necessary updates into the plan. Think of it as a continuous improvement cycle, always refining and updating your legal defense against disruptions. Regular testing of the plan’s effectiveness in maintaining compliance is crucial to ensure its viability and readiness. Consider a scenario-based exercise simulating a specific regulatory challenge to test the effectiveness of the procedures.
Last Word
So, there you have it: your roadmap to surviving the inevitable business hiccups (and maybe even the asteroid). Remember, a well-crafted business continuity plan isn’t just about avoiding catastrophe; it’s about seizing opportunities amidst adversity. Think of it as a high-stakes game of business Jenga – the more prepared you are, the higher the tower you can build, and the more impressive your resilience will be. Now go forth and conquer (or at least, maintain operations).
General Inquiries
What’s the difference between RTO and RPO?
RTO (Recovery Time Objective) is the maximum tolerable downtime after a disaster. RPO (Recovery Point Objective) is the maximum acceptable data loss.
How often should I test my business continuity plan?
Regular testing is crucial! Aim for at least annual tabletop exercises and periodic full-scale simulations, frequency depending on your risk profile.
What if my plan doesn’t cover every possible scenario?
No plan is perfect. Focus on covering the most likely and impactful threats. Regular review and updates are key to adapting to changing circumstances.
Who should be involved in creating the plan?
Involve key personnel from various departments, including IT, operations, management, and legal. Cross-functional collaboration is essential.