Disaster Recovery Planning Checklist: Let’s face it, the apocalypse (or at least a minor office meltdown) might not be *quite* as glamorous as Hollywood portrays. But proper planning? That’s where the real drama – and surprisingly, humor – lies. This checklist isn’t just about avoiding data loss; it’s about ensuring your business survives the inevitable unexpected events, whether it’s a rogue meteor or a spilled latte short-circuiting the server. Think of it as your insurance policy against the digital dark ages – only infinitely more entertaining.
This guide walks you through everything from identifying potential disasters (yes, even rogue staplers count) to crafting a foolproof recovery strategy. We’ll explore backup methods, business continuity, and even the surprisingly complex art of communicating a crisis to stakeholders without accidentally triggering mass panic. Get ready to laugh, learn, and ultimately, be prepared for anything (almost anything).
Defining Disaster Recovery Planning
Disaster recovery planning (DRP), in its simplest form, is a meticulously crafted blueprint outlining how an organization will respond to and recover from disruptive events, ranging from a spilled latte on a crucial server (yes, it happens!) to a full-blown, Hollywood-style catastrophe. It’s less about predicting the apocalypse and more about mitigating the mayhem when the unexpected strikes.
A comprehensive DRP is not merely a good idea; it’s a vital lifeline for any organization that values its data, reputation, and continued existence. Think of it as the organization’s emergency insurance policy, but instead of paying out cash, it pays out operational continuity. Without a robust plan, even minor incidents can snowball into major crises, causing significant financial losses, reputational damage, and potential legal repercussions. Imagine the chaos of trying to rebuild your business from scratch after a ransomware attack, with no clear path forward. Not pretty.
The Importance of a Comprehensive Disaster Recovery Plan
A comprehensive DRP minimizes downtime, protects critical data, and ensures business continuity. It provides a structured approach to handling emergencies, reducing the chaos and confusion that often accompany unexpected events. A well-defined plan allows for faster recovery times, preventing prolonged disruptions that can severely impact revenue and customer relationships. Consider a major bank experiencing a system failure; the longer the outage, the greater the financial losses and erosion of public trust. A solid DRP helps mitigate such risks.
Potential Consequences of Inadequate Disaster Recovery Planning
The absence of a proper DRP or a poorly executed one can lead to devastating consequences. Financial losses can be astronomical, ranging from lost revenue to hefty fines for regulatory non-compliance. Reputational damage can be equally severe, with customers losing trust and partners reconsidering their relationships. Furthermore, legal repercussions are a real possibility, particularly if data breaches or other regulatory violations occur. The infamous 2017 Equifax data breach, resulting from a failure to patch known vulnerabilities, serves as a stark reminder of the high stakes involved. Millions of records were compromised, leading to billions of dollars in losses and lasting reputational harm.
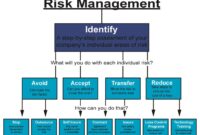
Stages of a Disaster Recovery Process
A typical disaster recovery process unfolds in several key stages, best visualized in a flowchart. Imagine this flowchart as a detailed map guiding you through the treacherous terrain of a disaster. Each step is crucial, and neglecting any of them could lead to significant setbacks.
The flowchart would depict the following stages, connected by arrows indicating the sequential flow:
1. Prevention & Mitigation: This initial stage involves implementing measures to prevent disasters and reduce their impact. Think firewalls, backups, and employee training. This phase is all about proactive defense, minimizing the chances of a disaster occurring in the first place.
2. Disaster Detection & Notification: This is the moment the alarm bells go off. Automated systems and human monitoring should quickly identify the disaster and alert relevant personnel. Think of it as the emergency response team getting the call.
3. Activation of the Disaster Recovery Plan: Once a disaster is confirmed, the pre-defined plan is activated, triggering pre-planned procedures and assigning roles and responsibilities. This is the crucial step where the well-rehearsed plan goes into action.
4. Recovery: This stage involves restoring systems, data, and operations to a functional state. Think of this as rebuilding the castle after the dragon attack.
5. Post-Disaster Review: After the dust settles, a thorough review analyzes the effectiveness of the response, identifies areas for improvement, and updates the plan accordingly. This is crucial for continuous improvement and future preparedness. It’s about learning from mistakes and strengthening the defenses.
Identifying Potential Disasters and Risks
Let’s face it, disaster recovery planning isn’t exactly a picnic in the park. It’s more like planning a picnic in a hurricane-prone zone, while simultaneously juggling chainsaws and a plate of exquisitely delicate petit fours. But fear not, intrepid business owner! This section will help you identify the potential calamities that could send your carefully constructed business empire tumbling down like a stack of poorly balanced Jenga blocks. We’ll then arm you with the knowledge to mitigate these risks, turning potential disaster into a mildly inconvenient hiccup.
Identifying potential disasters and their associated risks is crucial for effective disaster recovery planning. Failing to do so is akin to setting sail without a map – you might reach your destination, but the journey will likely be significantly longer, and considerably more terrifying. A thorough risk assessment allows for proactive measures, transforming reactive firefighting into a well-orchestrated preventative dance.
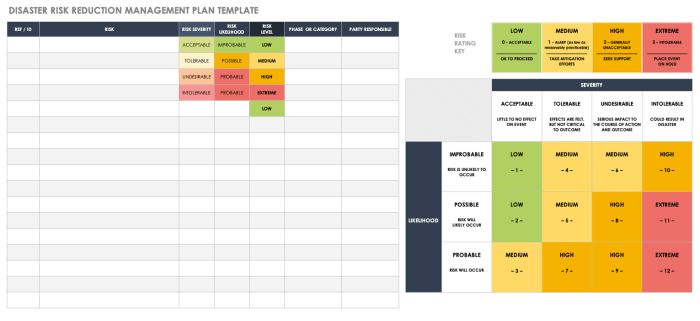
Common Disaster Types and Associated Risks
Five common types of disasters impacting businesses are natural disasters, cyberattacks, power outages, equipment failures, and human error. Each presents unique challenges and necessitates tailored mitigation strategies. Ignoring these risks is akin to leaving your front door unlocked while shouting to the world about your expensive jewelry collection. Let’s not do that.
| Disaster Type | Risk | Likelihood | Impact |
|---|---|---|---|
| Natural Disasters (e.g., floods, earthquakes) | Data loss due to physical damage to servers and infrastructure | Medium | High |
| Cyberattacks (e.g., ransomware, DDoS attacks) | Data breaches, system downtime, financial losses | High | High |
| Power Outages (e.g., extended blackouts) | Data loss, business interruption, reputational damage | Medium | Medium |
| Equipment Failures (e.g., server crashes, hardware malfunctions) | System downtime, data corruption, lost productivity | Medium | Medium |
| Human Error (e.g., accidental data deletion, misconfiguration) | Data loss, system instability, security breaches | High | Medium |
Mitigation Strategies for Identified Risks
Effective mitigation strategies are paramount. They are the safety net that catches you when the unexpected happens, preventing a complete freefall into the abyss of business oblivion. Think of them as your highly trained, caffeinated disaster-response ninjas, ever-vigilant and ready to spring into action.
For natural disasters, consider offsite backups and geographically dispersed data centers. For cyberattacks, robust security measures, regular security audits, and employee training are vital. Power outages can be mitigated with uninterruptible power supplies (UPS) and backup generators. Regular maintenance and redundancy are key for equipment failures. Finally, for human error, rigorous procedures, access controls, and employee training can significantly reduce risk. These strategies aren’t just good ideas; they are the difference between a smoothly running business and a spectacular, albeit preventable, meltdown.
Data Backup and Recovery Strategies
Data backup and recovery – the unsung heroes of disaster recovery planning. Think of them as your digital insurance policy, protecting your precious data from the inevitable (and sometimes hilariously avoidable) calamities that befall even the most technologically savvy organizations. Without a robust strategy, you’re playing digital roulette, and the odds are not in your favor.
Data backup strategies are as varied as the types of data themselves, but some core methods consistently prove their worth. Choosing the right approach involves a delicate balance between speed, storage space, and the level of protection needed. Getting this wrong can be akin to building a castle out of marshmallows – charming, but utterly vulnerable to the slightest breeze (or rogue intern).
Data Backup Methods: Full, Incremental, and Differential
The world of data backup isn’t a simple “copy and paste” operation. Different methods offer varying levels of efficiency and protection, each with its own strengths and weaknesses. Understanding these nuances is crucial for creating a backup strategy that’s both effective and, dare we say, elegant.
- Full Backup: This is the complete copy of all your data. Think of it as creating a pristine, untouched master copy. It’s time-consuming but provides a complete restoration point. Imagine it as meticulously recreating the Mona Lisa, brushstroke by brushstroke.
- Incremental Backup: This only backs up the data that has changed since the last full or incremental backup. It’s like only documenting the changes made to a manuscript since the last revision, saving time and storage space. However, restoring from incremental backups requires restoring the full backup first, then each subsequent incremental backup.
- Differential Backup: This backs up all data that has changed since the last *full* backup. It’s a middle ground between full and incremental backups, offering a faster restore time than incremental backups while requiring less storage space than full backups. Think of it as taking notes on a meeting, recording all changes since the initial draft.
Cloud-Based versus On-Premise Backup Solutions
The age-old debate: cloud or on-premise? The choice depends heavily on your organization’s specific needs, budget, and risk tolerance. Each option offers unique advantages and disadvantages, making the decision a strategic one rather than a simple preference.
| Feature | Cloud-Based | On-Premise |
|---|---|---|
| Cost | Subscription-based, potentially lower upfront costs | Higher upfront costs, ongoing maintenance expenses |
| Scalability | Easily scalable to meet changing needs | Requires significant planning and investment for scalability |
| Accessibility | Accessible from anywhere with an internet connection | Limited to the physical location of the backup server |
| Security | Relies on the cloud provider’s security measures | Security responsibility lies solely with the organization |
Testing Data Restoration Processes, Disaster Recovery Planning Checklist
Testing your data recovery process isn’t just a good idea; it’s a necessity. Regular testing ensures that your backup strategy works as intended and that your team is prepared to handle a real-world disaster. Imagine a fire drill – you don’t want to discover flaws in your evacuation plan during an actual fire!
- Establish a testing schedule: Regular testing, ideally including simulated disasters, is key.
- Restore a sample of data: Test the restoration process with a representative subset of your data to verify its integrity and completeness.
- Document the process: Keep detailed records of your testing procedures, results, and any issues encountered. This documentation will be invaluable in future recovery efforts.
- Involve your team: Engage your IT team in the testing process to ensure they are familiar with the procedures and can effectively execute them during a real emergency.
Data Recovery from Complete System Failure
The worst-case scenario: a complete system failure. While not ideal, having a well-defined recovery plan can significantly reduce downtime and data loss. Think of this plan as your escape route from a burning building – you want it to be clear, concise, and well-rehearsed.
- Activate your disaster recovery plan: This involves notifying key personnel and initiating the predetermined recovery procedures.
- Assess the damage: Determine the extent of the system failure and identify the affected data.
- Restore from backups: Utilize your chosen backup method (full, incremental, differential) to restore the affected data to a functional system.
- Verify data integrity: After restoration, carefully check the restored data to ensure its accuracy and completeness. This is crucial to prevent data loss or corruption.
- Resume operations: Once data integrity is verified, gradually resume normal operations, monitoring the system for any further issues.
Business Continuity Planning
Let’s face it, disasters are rarely punctual. They barge in uninvited, wreaking havoc on our carefully crafted schedules and, more importantly, our businesses. Business Continuity Planning isn’t about predicting the apocalypse (though that would be a handy skill); it’s about creating a roadmap to navigate the choppy waters of unexpected events, ensuring your business can still float – and ideally, even thrive – when the unexpected happens. It’s all about minimizing disruption and maximizing resilience. Think of it as your business’s emergency escape plan, but with less screaming and more strategic thinking.
Business continuity planning focuses on identifying critical business functions that must remain operational during and after a disaster. This goes beyond simply keeping the lights on; it’s about maintaining the core processes that keep your business alive and kicking. We’re talking about those essential functions that directly impact your revenue, customer relationships, and overall survival. Ignoring this step is like sailing a ship without a map – you might reach land eventually, but the journey will be far more perilous and unpredictable.
Critical Business Functions During a Disaster
Maintaining essential business operations during a crisis requires a clear understanding of what absolutely *must* continue functioning. This isn’t a popularity contest; it’s a survival strategy. For example, a hospital’s critical function is patient care, while an e-commerce company’s might be order fulfillment and customer service. Identifying these core functions allows you to prioritize resources and efforts effectively. Failing to do so is like trying to rebuild a house by starting with the wallpaper – you’ll end up with a very pretty ruin.
- Customer Support: Maintaining communication channels to address customer concerns and provide updates.
- Financial Operations: Ensuring access to funds and managing financial transactions.
- Data Management: Protecting and accessing critical data through backup and recovery systems.
- Supply Chain Management: Maintaining the flow of essential goods and services.
- Communication Systems: Establishing clear and reliable communication channels for internal and external stakeholders.
Maintaining Essential Operations During Prolonged Outages
A prolonged outage can be a real nail-biter, but with a well-defined plan, you can mitigate the damage. This involves identifying alternative locations, systems, and resources to ensure business continuity. Think of it as having a backup plan for your backup plan. For instance, a company could utilize cloud-based systems for data storage and access, allowing operations to continue even if their primary office is inaccessible. A well-stocked emergency kit for employees working from home is also a vital component. Let’s face it, nobody wants to be caught without coffee during a crisis.
Alternative Work Arrangements for Employees
When the office is off-limits, your employees still need to work. Consider remote work options, utilizing tools like video conferencing, project management software, and secure communication platforms. The 2020 pandemic provided a crash course in remote work for many businesses, showcasing the effectiveness of these arrangements. However, ensuring employees have the necessary equipment and training is crucial for a smooth transition. Imagine trying to perform surgery with a rusty spoon – not ideal.
Communication Protocols for Crisis Management
Clear and consistent communication is paramount during a crisis. Establish a communication tree, designating key personnel responsible for disseminating information to employees, customers, and stakeholders. Utilize multiple communication channels, such as email, SMS, and phone calls, to ensure everyone receives updates. This isn’t about flooding inboxes; it’s about providing timely and accurate information to keep everyone informed and on the same page. Imagine trying to fight a fire with mismatched hoses – chaotic and ineffective. Consider pre-recorded messages for frequently asked questions to manage information flow efficiently.
Technology and Infrastructure Considerations
Let’s face it, your IT infrastructure isn’t just a collection of blinking lights and whirring fans; it’s the lifeblood of your organization. A well-planned disaster recovery strategy needs to treat this lifeblood with the respect it deserves – think less “Weekend at Bernie’s” and more “Mission: Impossible” level precision. Ignoring this crucial aspect is akin to leaving your front door unlocked while on vacation – tempting fate, and potentially leading to a very messy situation.
Protecting your technology and infrastructure is paramount to a successful recovery. This involves identifying critical components, implementing redundancy, and leveraging virtualization to ensure business continuity even in the face of unforeseen circumstances. Failing to do so could leave your organization resembling a beached whale – stranded, vulnerable, and attracting unwanted attention (like angry customers).
Essential Hardware and Software Components
Identifying the essential hardware and software components that require protection is the first, and arguably most important, step. This isn’t just about listing everything; it’s about prioritization. Think of it like a triage in a hospital – you deal with the life-threatening injuries first. Similarly, you need to identify the systems that are absolutely critical for your core business functions. This could include servers hosting your primary applications, databases containing crucial customer information, network equipment enabling communication, and even specialized software applications that are irreplaceable. A thorough inventory, categorized by criticality, is essential. Consider factors like single points of failure; if a single piece of hardware or software failing brings down the entire system, that’s a major red flag.
Redundancy and Failover Systems
Redundancy and failover systems are your insurance policy against catastrophic events. Redundancy means having backups of everything crucial – think of it as having a spare tire in your car, but for your entire IT infrastructure. Failover systems are the mechanisms that automatically switch to these backups when the primary systems fail. This isn’t just about having a second server; it’s about a seamlessly integrated system that ensures minimal downtime. Imagine a bank’s ATM network; if one ATM goes down, the system automatically routes transactions to another, ensuring uninterrupted service. This is the power of a well-designed redundancy and failover strategy. The goal is to minimize the disruption caused by a disaster.
The Role of Virtualization in Disaster Recovery
Virtualization is a game-changer in disaster recovery. By creating virtual copies of your servers and applications, you can easily spin up new instances in a different location in case of a disaster. Think of it as having a digital clone of your entire IT infrastructure ready to go at a moment’s notice. This significantly reduces recovery time and minimizes data loss. A company like Amazon, with its vast cloud infrastructure, relies heavily on virtualization to ensure its services remain available even in the face of significant outages. Their ability to rapidly provision new virtual instances demonstrates the power of this technology in disaster recovery.
Resilient Network Architecture Diagram
[Imagine a diagram here showing a resilient network architecture. The diagram would depict multiple data centers interconnected via redundant network links. Each data center would have its own servers, storage, and network equipment, with failover mechanisms in place. A geographical diversity is shown, with data centers located in separate geographical regions to protect against regional disasters. The diagram would clearly show how traffic is routed and how failover mechanisms ensure continuous operation in the event of a failure in one location. This could also include cloud integration, illustrating the use of cloud services for backup and disaster recovery.]
Testing and Maintenance of the Plan
Let’s face it, a disaster recovery plan gathering dust on a shelf is about as useful as a chocolate teapot in a hurricane. Regular testing and maintenance are not just good practice; they’re the lifeblood of a truly effective plan. Think of it as a fire drill for your entire business – a little inconvenient in the short term, but potentially life-saving in the long run. Without regular testing, your plan is nothing more than a well-intentioned fantasy.
Regular testing and drills are crucial for identifying weaknesses and ensuring the plan’s effectiveness in a real-world scenario. These exercises allow your team to practice their roles, identify bottlenecks in the process, and refine the plan based on real-time feedback. The goal isn’t to create a perfect plan on the first try, but to continuously improve it through iterative testing and refinement. This proactive approach minimizes disruptions and maximizes the chances of a successful recovery should disaster strike. It’s like a dress rehearsal for the most important performance of your company’s life.
Conducting a Full-Scale Disaster Recovery Simulation
A full-scale simulation involves a comprehensive test of the entire disaster recovery plan. This isn’t a simple “let’s see if the backup works” exercise; it’s a meticulously planned event that mimics a real-world disaster. This might involve shutting down systems in a controlled environment, relocating staff to a secondary site, and restoring data from backups. The simulation should cover all aspects of the plan, from communication protocols to data restoration procedures. Think of it as a “dress rehearsal” for the apocalypse – better to find flaws in a controlled setting than during an actual crisis. Consider including a timeline, role assignments for each participant, and clear communication channels to ensure a smooth and effective simulation. The goal is to identify and rectify any shortcomings before a real disaster occurs. For example, a large financial institution might simulate a complete server failure at their primary data center, forcing them to switch to their backup facility and restore all critical systems and data. The success of this simulation would be measured by the speed and efficiency of the recovery, and the minimal disruption to their clients’ access to services.
Metrics for Evaluating Disaster Recovery Plan Effectiveness
Several key metrics can be used to assess the effectiveness of a disaster recovery plan. These metrics provide objective data to gauge the plan’s strengths and weaknesses. The goal is not just to recover, but to recover quickly, efficiently, and with minimal disruption to business operations.
- Recovery Time Objective (RTO): The maximum acceptable downtime before systems and data must be restored. For example, an e-commerce company might have an RTO of four hours, while a hospital might have a much lower RTO, perhaps measured in minutes.
- Recovery Point Objective (RPO): The maximum acceptable data loss in the event of a disaster. This is often expressed as a time interval, such as “no more than 24 hours of data loss”.
- Work Recovery Time (WRT): The time it takes to restore business operations to a functional level after a disaster. This metric takes into account not only system recovery but also the time needed for staff to resume their duties.
- Mean Time To Recovery (MTTR): The average time it takes to recover from a specific failure. This is a useful metric for tracking improvements over time.
These metrics provide a quantitative assessment of the plan’s performance, allowing for objective evaluation and continuous improvement. Tracking these metrics over multiple simulations allows for the identification of trends and the implementation of corrective actions. Imagine a scenario where the initial RTO was 8 hours, but after a simulation, it was reduced to 4 hours. This clearly demonstrates the positive impact of testing and refinement.
Routine Maintenance and Updates of the Disaster Recovery Plan
Maintaining a disaster recovery plan is an ongoing process. It’s not a “set it and forget it” type of deal. Regular updates are essential to ensure the plan remains relevant and effective.
- Annual Review: A comprehensive review of the entire plan, including all procedures, contact information, and technology used.
- Quarterly Updates: Review and update contact information, technology changes, and any relevant regulatory changes.
- Post-Incident Review: After any incident, even a minor one, conduct a thorough review of the plan’s effectiveness and identify areas for improvement.
- Technology Updates: As technology changes, update the plan to reflect the latest hardware, software, and cloud services.
- Staff Training: Regularly train staff on the disaster recovery plan, ensuring everyone understands their roles and responsibilities.
By implementing this maintenance checklist, organizations can ensure that their disaster recovery plan remains a dynamic and effective tool, ready to meet any challenge. Regular maintenance ensures that the plan stays current, accurate, and relevant, minimizing the impact of any future disruptions. Think of it as regular car maintenance; small, preventative measures can prevent major breakdowns later on.
Communication and Stakeholder Management
Effective communication is the lifeblood of any successful disaster recovery plan. Think of it as the emergency broadcast system for your business – except instead of zombies, you’re battling data loss and operational disruptions. A well-defined communication strategy ensures everyone knows their role, reducing chaos and maximizing the speed of recovery. Without it, you’re essentially playing a game of telephone during a hurricane, and nobody wants that.
Communication protocols should be established for both internal and external stakeholders, covering all stages of a disaster, from initial detection to full recovery. This involves clearly defined roles, responsibilities, and escalation paths. Imagine a well-oiled machine, each part working in perfect harmony to restore operations – that’s the goal of a robust communication strategy.
Communication Protocols for Internal and External Stakeholders
Establishing clear communication protocols is paramount. Internal protocols should detail how information will be disseminated to employees, including emergency contact information, meeting points, and work-from-home procedures. External protocols should Artikel communication with clients, partners, and regulatory bodies, ensuring transparency and maintaining trust. For example, a pre-recorded message detailing the situation and next steps could be deployed to customers via phone and email, preventing widespread panic and misinformation. A dedicated media relations team should be prepared to handle press inquiries, maintaining a consistent message and controlling the narrative.
Examples of Effective Communication Strategies During a Crisis
During a crisis, simple, clear, and concise communication is key. Avoid jargon and technical terms. Think of using a system of color-coded alerts (green for all clear, yellow for potential issue, red for major incident) to rapidly convey the severity of the situation. Regular updates, even if there’s no significant change, help maintain calm and demonstrate that the situation is being actively managed. For instance, a large financial institution might use a tiered alert system, with different levels of detail for employees, clients, and regulators based on their need-to-know. Real-time updates through a dedicated internal communication platform (like Slack or Microsoft Teams) can ensure swift dissemination of information and facilitate immediate problem-solving.
Importance of Training Employees on Disaster Recovery Procedures
Training employees is not just a box to tick; it’s an investment in your organization’s resilience. Regular drills and simulations allow employees to familiarize themselves with the procedures and identify potential weaknesses in the plan. Think of it as a fire drill, but for data loss. The more prepared your employees are, the smoother the recovery process will be. For example, a tabletop exercise where employees role-play different scenarios can identify communication gaps and areas for improvement. Regular refresher training ensures that even new employees are up-to-speed on the procedures.
Key Stakeholders and Their Roles in the Disaster Recovery Process
A well-defined list of key stakeholders and their responsibilities is crucial for effective disaster recovery. This list should be readily accessible and regularly updated. Consider a table for clear visual representation.
| Stakeholder | Role | Contact Information |
|---|---|---|
| IT Department | Lead technical recovery efforts, restore systems and data. | [Contact Details] |
| Executive Team | Make critical decisions, allocate resources, communicate with external stakeholders. | [Contact Details] |
| Communications Team | Manage internal and external communications, maintain consistent messaging. | [Contact Details] |
| Legal Department | Ensure compliance with regulations, handle legal aspects of the recovery. | [Contact Details] |
| Clients/Customers | Receive updates on service disruptions and recovery progress. | [Contact Details] |
Legal and Regulatory Compliance: Disaster Recovery Planning Checklist

Navigating the legal landscape of disaster recovery might seem as daunting as escaping a collapsing skyscraper in a business suit, but fear not! With careful planning, you can avoid the legal equivalent of a building implosion. Proper disaster recovery planning isn’t just about getting your business back online; it’s about ensuring you’re compliant with the myriad of laws and regulations that govern your industry and data.
This section will clarify the legal and regulatory requirements pertinent to disaster recovery, emphasizing the critical role of data security and privacy. We’ll explore how to meet industry-specific regulations and provide a checklist of legal considerations to integrate into your disaster recovery plan. Think of it as your legal escape route from a potential data catastrophe.
Relevant Legal and Regulatory Requirements
Understanding applicable laws and regulations is paramount. These vary significantly based on industry, location, and the type of data handled. For example, healthcare organizations must comply with HIPAA, financial institutions with GLBA, and companies handling personal data in Europe with GDPR. Failure to comply can result in hefty fines, reputational damage, and even legal action. A thorough review of relevant legislation is crucial, and consulting legal counsel is highly recommended. This isn’t a game of chance; it’s a game of compliance.
Data Security and Privacy in Disaster Recovery
Data security and privacy are not mere afterthoughts; they are cornerstones of a robust disaster recovery plan. Protecting sensitive information during and after a disaster is critical. This involves implementing robust encryption, access controls, and data loss prevention measures. Consider the potential reputational damage and legal ramifications of a data breach following a disaster – it’s far more costly than preventative measures. Think of data security as your emergency fire extinguisher for sensitive information.
Compliance with Industry-Specific Regulations
Meeting industry-specific regulations is non-negotiable. Different sectors have unique legal obligations. For instance, the financial services industry faces stricter regulations concerning data backup and recovery times compared to, say, a bakery. Understanding and adhering to these sector-specific rules is essential to avoid penalties and maintain customer trust. This isn’t a one-size-fits-all scenario; it’s about tailoring your plan to your specific industry’s needs.
Legal Considerations for Disaster Recovery Plans
A comprehensive disaster recovery plan should include a dedicated section addressing legal and regulatory compliance. Here’s a list of essential legal considerations:
- Identification of all applicable laws and regulations.
- Data security and privacy protocols.
- Incident response procedures, including notification protocols in case of a data breach.
- Data retention policies, especially in the context of disaster recovery.
- Legal hold procedures for relevant data during and after a disaster.
- Designation of responsible individuals for legal compliance within the disaster recovery process.
- Regular review and updates of the plan to reflect changes in legislation.
Ignoring these legal aspects is akin to driving a car without brakes – potentially disastrous. A well-defined legal framework within your disaster recovery plan will not only protect your business but also ensure its longevity.
Conclusive Thoughts

So, there you have it: your comprehensive guide to navigating the treacherous waters of disaster recovery. Remember, a well-crafted plan isn’t just about mitigating risk; it’s about ensuring business continuity with minimal disruption and maximum comedic relief (where applicable, of course). With this checklist in hand, you’re not just prepared for disaster – you’re practically anticipating it with a well-stocked emergency snack drawer and a wry smile. Now go forth and conquer…or at least, survive the next power outage.
Expert Answers
What if my disaster recovery plan is too complicated?
Simplicity is key! A complex plan is often ignored. Prioritize essential functions and keep it concise. If it’s too complicated to understand, it’s too complicated to implement.
How often should I test my disaster recovery plan?
Regular testing is crucial! Aim for at least annual full-scale simulations and more frequent smaller tests of individual components. Think of it as a fire drill, but for your digital assets.
What’s the role of employees in disaster recovery?
Employee training is paramount. They are your first responders. Clearly defined roles and responsibilities, coupled with regular training, are essential for a smooth recovery process.
What about ransomware attacks?
Ransomware is a serious threat. Your plan should include strategies for detection, prevention (like regular updates and strong passwords!), and recovery, including potentially paying the ransom (a last resort decision, weighed carefully against the cost of recovery).