Disaster Recovery Planning Checklist: Let’s face it, the apocalypse (or at least a minor IT meltdown) might not be *quite* as cinematic as Hollywood portrays, but it’s still something you want to be prepared for. This checklist isn’t about stocking up on canned goods and duct tape (though, that’s a good idea too!), but rather about securing your business’s digital survival. We’ll navigate the treacherous waters of risk assessment, recovery strategies, and the surprisingly thrilling world of data backups, all while keeping a lighthearted (yet professional) tone.
This guide offers a comprehensive approach to disaster recovery planning, covering everything from identifying potential threats and vulnerabilities to implementing robust recovery strategies and procedures. We’ll delve into the nuances of various backup strategies, the importance of offsite data storage, and the critical role of regular testing and maintenance. Think of it as your digital life raft – essential equipment for navigating the stormy seas of unexpected events. And yes, we’ll even address those pesky legal and compliance requirements, because even superheroes need to follow the rules (mostly).
Defining Disaster Recovery Planning
Let’s face it, even the most meticulously planned business can be blindsided by a rogue asteroid (unlikely, but hey, we’re planning for *disasters*). Disaster Recovery Planning (DRP) isn’t about predicting the apocalypse; it’s about having a sensible, well-rehearsed plan to get back on your feet when the unexpected inevitably happens. Think of it as your business’s emergency escape route, but instead of a fire, it’s a ransomware attack or a hurricane.
Disaster recovery planning involves creating a comprehensive strategy to minimize the impact of disruptive events on your business operations. A robust DRP Artikels procedures for data backup, system recovery, and business continuity, ensuring minimal downtime and data loss. It’s not just about technology; it encompasses your people, processes, and physical assets. Ignoring it is like leaving your front door unlocked and hoping for the best.
Core Components of a Comprehensive Disaster Recovery Plan
A solid DRP is like a well-oiled machine – each part is crucial for smooth operation. Key components include a detailed risk assessment (identifying potential threats), a business impact analysis (determining the impact of various disruptions), recovery strategies (defining how to restore operations), testing and training (ensuring the plan works), and communication protocols (keeping everyone informed during a crisis). Without these, your plan is just a fancy document gathering dust.
Types of Disasters a Business Might Face
Disasters aren’t limited to natural calamities. They can range from the predictable (power outages, hardware failures) to the more dramatic (cyberattacks, terrorist acts, pandemics). Even something seemingly minor, like a disgruntled employee deleting crucial data, can cause significant disruption. It’s crucial to consider a wide spectrum of potential problems, from the mundane to the apocalyptic.
Disaster Recovery Strategies
Several strategies exist for recovering from disasters, each with its own strengths and weaknesses. Let’s examine a few:
- Hot Site: A fully operational duplicate of your primary data center, ready to take over instantly. Think of it as a luxurious spare apartment, fully furnished and ready for immediate occupancy. However, it comes with a hefty price tag for constant maintenance.
- Cold Site: A basic facility with power and connectivity, requiring significant setup time before becoming operational. Imagine a bare apartment – you have the space, but you need to furnish it before moving in. It’s cheaper than a hot site but significantly slower in recovery.
- Cloud-Based: Leveraging cloud services for data backup and disaster recovery. This offers scalability, cost-effectiveness, and accessibility. It’s like having a digital storage unit in the cloud – readily available, but you need a reliable internet connection.
Comparison of Disaster Recovery Strategies
| Strategy | Advantages | Disadvantages | Cost |
|---|---|---|---|
| Hot Site | Immediate recovery, minimal downtime | High cost, ongoing maintenance | High |
| Cold Site | Low cost, minimal ongoing maintenance | Significant setup time, longer downtime | Low |
| Cloud-Based | Scalable, cost-effective, accessible | Reliance on internet connectivity, potential vendor lock-in | Medium |
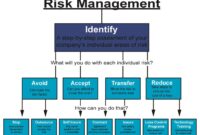
Assessing Risks and Vulnerabilities

Preparing for disaster is like preparing for a particularly flamboyant and unpredictable party: you need to know who might show up (the threats), what they might do (the impact), and how much champagne you need to keep things under control (your resources). Assessing risks and vulnerabilities is all about identifying those uninvited guests and planning your defense accordingly, before the punch bowl overflows with chaos.
Identifying potential threats to business operations and data integrity requires a thorough examination of your entire operation. Think of it as a meticulous search for potential weak points in your fortress, from the leaky roof (inadequate security protocols) to the suspiciously friendly guard dog (untrusted third-party vendors). This process involves scrutinizing every aspect of your business, from hardware and software to employee training and physical security. Ignoring even a small crack can lead to a catastrophic flood of problems.
Business Impact Analysis (BIA) Methods
A Business Impact Analysis (BIA) isn’t just about ticking boxes; it’s about understanding the very soul of your business. It’s a deep dive into how various disruptions would affect your operations, revealing which parts of your business are most vulnerable and the potential consequences of their failure. Common BIA methods include questionnaires, interviews with key personnel, and the use of specialized software to model various scenarios and estimate potential financial losses. For example, a BIA for an e-commerce company might reveal that a 24-hour outage of their website could lead to a significant loss in sales and customer trust. Another example could be a manufacturing company where a disruption to their supply chain could halt production, incurring losses in production and potential penalties to customers. These assessments are crucial in determining the priority and urgency of various recovery strategies.
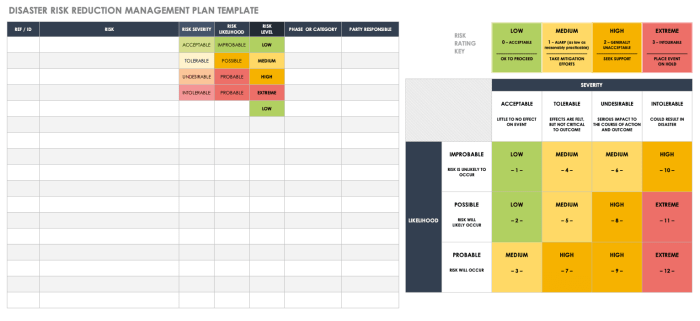
Risk Assessment Matrix
Once you’ve identified the potential threats, it’s time to prioritize them. This is where the risk assessment matrix comes in – a handy tool that helps you visualize the likelihood and impact of each threat. This matrix typically uses a scale (e.g., low, medium, high) for both likelihood and impact, allowing you to easily see which threats require immediate attention. For instance, a threat with high likelihood and high impact (like a major power outage for a data center) would be ranked higher than a threat with low likelihood and low impact (like a minor software glitch). This prioritization helps focus resources on the most critical risks, preventing you from wasting time and money on less pressing issues.
Common Vulnerabilities in IT Infrastructure and Business Processes
Let’s face it, vulnerabilities are everywhere, lurking like mischievous gremlins in your perfectly ordered systems. Common IT infrastructure vulnerabilities include outdated software, insecure network configurations, and lack of proper access controls. In business processes, vulnerabilities often stem from inadequate training, poor documentation, and a lack of contingency planning. For example, a reliance on a single point of failure (a single server holding all critical data) is a significant vulnerability. Similarly, a lack of regular data backups could lead to irreparable data loss in the event of a disaster. These vulnerabilities, if left unaddressed, can turn a minor inconvenience into a major catastrophe.
Developing Recovery Strategies and Procedures

Ah, recovery strategies – the phoenix rising from the ashes of IT disaster! Let’s face it, no plan is perfect, but a well-thought-out strategy can significantly reduce the time it takes to get back on your feet after a catastrophic event. Think of it as your emergency escape plan, but for your entire business, and with far fewer screaming children.
Developing robust recovery strategies involves more than just hoping for the best. It requires meticulous planning, regular testing, and a dash of gallows humor to get you through the inevitable hiccups. This section will delve into the nitty-gritty of creating procedures that will keep your business afloat even when the metaphorical (or literal) Titanic hits an iceberg.
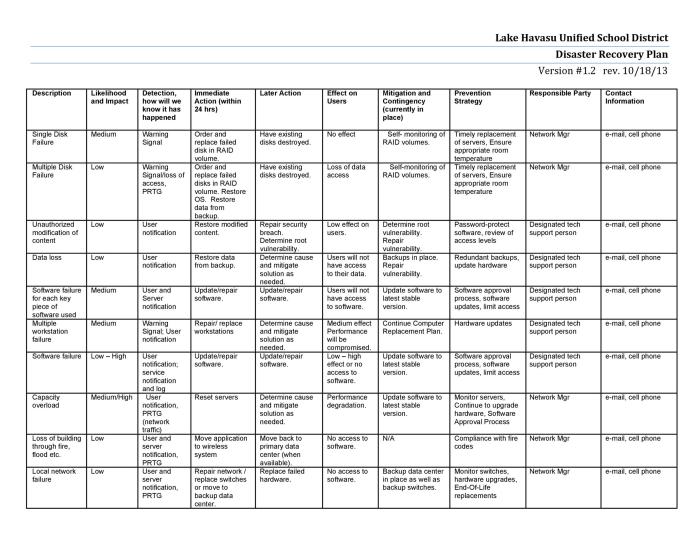
Step-by-Step Recovery Procedure for a Critical Business Application
A well-defined, step-by-step procedure is crucial for restoring critical business applications. Imagine your customer relationship management (CRM) system going down – the horror! To avoid such a scenario, a detailed recovery plan is essential. This plan should include steps for identifying the problem, isolating the issue, implementing the recovery, and verifying the system’s functionality. Consider including screenshots or diagrams to illustrate the process for clarity. For example, a step-by-step procedure for restoring a CRM system might involve verifying backup integrity, restoring the database to a test environment, performing functional tests, and finally, deploying the restored system to the production environment. Each step should have a designated owner and an estimated completion time.
Data Backup Restoration Checklist
Regular backups are only half the battle. The other half is knowing how to restore them without pulling your hair out. This checklist ensures a smooth and efficient restoration process, minimizing downtime and data loss.
- Verify backup integrity before initiating the restore process.
- Identify the appropriate backup to restore based on the recovery point objective (RPO).
- Select the appropriate restore method (full, incremental, or differential).
- Follow the vendor’s instructions for restoring the data.
- Verify data integrity after the restore process is complete.
- Test application functionality after data restoration.
- Document the entire restoration process for future reference.
Communication and Notification Procedures, Disaster Recovery Planning Checklist
Communication is key, especially during a crisis. Imagine trying to coordinate a response to a major outage with everyone yelling into walkie-talkies – chaos! Clear communication protocols are essential for keeping everyone informed and working together effectively. These procedures should Artikel communication channels, notification lists, and escalation procedures. For instance, a tiered notification system, using email, SMS, and phone calls for escalating urgency, ensures timely alerts to all stakeholders.
Establishing Clear Roles and Responsibilities
A well-defined disaster recovery team, with clearly defined roles and responsibilities, is crucial. Think of it as a well-oiled machine – each part has its specific function and works in harmony with others. Avoid the “everyone does everything” approach; this leads to confusion and inefficiency. A simple organizational chart outlining roles (e.g., team leader, communication officer, technical support) and their respective responsibilities can significantly improve the effectiveness of the disaster recovery process. Regular training and drills will ensure team members are prepared to act swiftly and efficiently during a real crisis.
Testing and Maintenance of the Plan
Let’s face it, a disaster recovery plan gathering dust on a shelf is about as useful as a chocolate teapot in a hurricane. To ensure your meticulously crafted plan doesn’t become a monument to wasted effort, rigorous testing and regular maintenance are absolutely crucial. Think of it as a yearly MOT for your business’s survival – you wouldn’t drive a car without one, would you?
Regular testing and updates ensure your plan remains a dynamic, living document, not a static relic of the past. This involves more than just a cursory glance; it requires a dedicated approach encompassing various testing methods and a commitment to ongoing refinement. Neglecting this aspect can leave your organization vulnerable when disaster strikes, transforming a well-intentioned plan into a costly liability.
Methods for Testing the Disaster Recovery Plan
Testing your disaster recovery plan isn’t just about ticking boxes; it’s about identifying weaknesses before they become catastrophic failures. Different testing methods offer varying levels of intensity and realism, allowing you to tailor your approach to your specific needs and resources. From low-impact tabletop exercises to full-blown simulations, the goal is to expose vulnerabilities and refine your procedures.
Tabletop Exercises: These involve a group discussion, simulating a disaster scenario. Participants work through the plan, identifying potential bottlenecks and areas for improvement. Think of it as a low-stakes dress rehearsal – a chance to identify potential wardrobe malfunctions (or procedural flaws) before the big show. For example, a tabletop exercise might simulate a server failure, forcing the team to walk through the process of restoring data from backups and switching to a redundant system. This allows for collaborative problem-solving and identification of communication gaps without the expense and disruption of a full-scale simulation.
Full-Scale Simulations: These are more involved, often requiring the relocation of personnel to a secondary site and the actual use of backup systems. This is the ultimate test, allowing you to identify any hidden flaws in your plan. Imagine a full-scale simulation as the real deal, albeit in a controlled environment. A company might simulate a complete data center outage, forcing them to activate their backup systems and recover critical applications and data at a secondary location. This allows for a thorough test of the entire plan, identifying potential problems with network connectivity, data restoration times, and overall operational efficiency.
Schedule for Regular Reviews and Updates
A disaster recovery plan isn’t a “set it and forget it” kind of thing. Regular reviews and updates are essential to ensure it remains relevant and effective. Think of it as a living document that needs regular nourishment.
A realistic schedule might include annual full reviews, with quarterly updates to address changes in technology, personnel, or business operations. Significant events, such as system upgrades or mergers, should trigger immediate plan updates. Consider implementing a version control system to track changes and ensure everyone is working with the most up-to-date version. This prevents confusion and ensures that everyone is on the same page.
Best Practices for Maintaining Accurate Documentation
Accurate and up-to-date documentation is the backbone of a successful disaster recovery plan. Imagine trying to build a house without blueprints – chaos! Maintaining accurate documentation ensures everyone knows their role and responsibilities.
Centralized document storage using a version-controlled system is key. Regular audits of the documentation, involving cross-checking with IT and business units, ensure accuracy and completeness. Clearly defined roles and responsibilities, contact information, and step-by-step procedures are all vital components of effective documentation. Think of it as a well-organized toolbox – everything has its place, and you know exactly where to find it when you need it.
Importance of Regular Training for Disaster Recovery Team Members
A disaster recovery plan is only as good as the people who implement it. Regular training ensures team members are familiar with their roles, responsibilities, and the plan’s procedures.
Training should be conducted at least annually, incorporating both theoretical and practical exercises. This could involve tabletop exercises, simulations, or even just reviewing the plan and discussing potential scenarios. Regular refresher courses keep everyone informed about any updates or changes to the plan, ensuring everyone remains proficient and prepared for a real-world disaster. Consider using interactive training methods, like online modules or simulations, to make the learning process engaging and effective. Remember, a well-trained team is the best insurance policy against disaster.
Data Backup and Recovery
Data backup and recovery – the unsung heroes of disaster recovery planning. Think of it as your digital insurance policy, ensuring that even if catastrophe strikes (and let’s face it, it probably will, Murphy’s Law and all that), your precious data survives to fight another day. A well-defined backup and recovery plan is not just about having backups; it’s about having a robust, tested, and easily executed plan to get your data back online quickly and efficiently, minimizing downtime and preventing a complete meltdown.
Data backup strategies are varied, each with its own strengths and weaknesses. Choosing the right one depends on factors such as the volume of data, the frequency of changes, the recovery time objective (RTO), and the recovery point objective (RPO). Getting this wrong can lead to tears, lost productivity, and potentially, the wrath of your boss.
Data Backup Strategies
Different backup methods offer varying levels of efficiency and recovery speed. A full backup copies all data, creating a complete image. While simple, it’s time-consuming. Incremental backups copy only the data that has changed since the last full or incremental backup, saving time and storage space. Differential backups copy all data that has changed since the last full backup. This method is a happy medium between full and incremental backups, offering a faster recovery time than full backups but requiring more storage space than incremental backups. Imagine it like this: a full backup is like repainting your entire house; an incremental backup is like touching up a chipped paint spot; and a differential backup is like repainting an entire room. The choice depends on your needs and tolerance for recovery time versus storage space.
Designing a Data Backup and Recovery Plan
A comprehensive data backup and recovery plan should Artikel the what, when, where, and how of data protection. This includes specifying the backup strategy (full, incremental, or differential), the frequency of backups (daily, weekly, etc.), the storage media (tapes, disks, cloud storage), and the retention policy (how long backups are kept). For example, a plan might dictate daily incremental backups, weekly full backups, with backups stored both on-site and off-site, and retained for a minimum of 90 days. A critical element is defining roles and responsibilities. Who is responsible for performing backups? Who handles restoration? Clearly defining these responsibilities prevents confusion and delays during a recovery.
Offsite Data Storage and Replication
Offsite storage is crucial. Imagine your primary data center going up in flames (hopefully not literally!). Having a copy of your data stored in a geographically separate location ensures business continuity. Replication goes a step further by automatically mirroring data to a secondary location, offering near-instant recovery. This is like having a spare tire for your data – it might seem unnecessary until you really need it.
Verifying Data Integrity After Recovery
After a recovery, verifying data integrity is paramount. This involves checking that the restored data is complete, accurate, and free from corruption. Techniques include comparing checksums of the original and restored data or running database integrity checks. Failing to verify data integrity could lead to inaccurate information, which could be far more disastrous than the initial event. Think of it as double-checking your work – it might seem tedious, but it’s essential to ensure the accuracy and reliability of your restored data.
Business Continuity Planning Integration
Disaster recovery planning (DRP) and business continuity planning (BCP) are like two peas in a pod, but one’s a bit more… dramatic. DRP focuses on getting your IT systems back online after a catastrophe, think rescuing your precious data from a fiery inferno (metaphorically, of course, unless you’re truly unlucky!). BCP, on the other hand, takes a broader view, encompassing all aspects of your business operations, ensuring you can keep the metaphorical lights on, even if the power grid goes kaput. It’s about keeping the business ticking, even if it’s on a slightly wonky rhythm.
Integrating DRP into a comprehensive BCP strategy is like adding the final, delicious cherry on top of a perfectly baked cake. A robust BCP considers various scenarios – not just IT failures, but also natural disasters, pandemics, even rogue office hamsters chewing through vital cables. DRP, as a crucial component, ensures the technological backbone remains functional, allowing other BCP strategies to effectively kick in. This synergistic approach minimizes disruption, keeps clients happy, and prevents your business from becoming a cautionary tale in a management textbook.
Disaster Recovery’s Role in Minimizing Disruption
A well-integrated DRP significantly reduces downtime during a disaster. Imagine a scenario where a major hurricane slams into your headquarters. BCP Artikels alternative work locations, communication strategies, and even temporary supply chains. But without a functioning IT infrastructure – the realm of DRP – your employees are essentially working in the dark ages. DRP ensures that critical systems, data, and applications are quickly restored, enabling a swift return to operational normalcy. The faster the recovery, the less revenue is lost, and the less likely customer loyalty is compromised. Consider the case of a major bank; their DRP ensures that ATMs remain functional even during a widespread power outage, minimizing customer frustration and maintaining confidence.
Aligning Disaster Recovery and Business Objectives
To ensure alignment, DRP objectives must directly support overall business goals. For instance, if a key business objective is maintaining 99.9% uptime, the DRP should include recovery time objectives (RTOs) and recovery point objectives (RPOs) that reflect this target. A company prioritizing rapid recovery might invest in cloud-based solutions and redundant data centers, whereas a smaller business might opt for a more cost-effective, albeit slower, recovery method. Each approach must be tailored to the specific needs and risk tolerance of the business. Consider a small e-commerce business – their DRP might prioritize the rapid restoration of their online store, even if some less critical systems experience a slightly longer downtime.
Technology Considerations
Disaster recovery isn’t just about having a backup plan; it’s about having a backup plan that can actually *work* when the metaphorical (or literal!) you-know-what hits the fan. This means seriously considering the technology that underpins your entire recovery strategy. Ignoring this aspect is like trying to build a house of cards in a hurricane – it’s not going to end well.
The technological landscape plays a pivotal role in ensuring a swift and seamless recovery. From virtualization to cloud computing, the right tools can significantly reduce downtime and data loss. Conversely, outdated or poorly integrated technologies can exacerbate the situation, transforming a minor inconvenience into a full-blown catastrophe. Let’s dive into the specifics.
Virtualization and Cloud Computing in Disaster Recovery
Virtualization allows you to create virtual copies of your servers and applications, effectively creating backups that can be quickly spun up in the event of a disaster. This offers significant advantages in terms of speed and resource efficiency. Imagine needing to physically replace a server during a crisis – that’s a logistical nightmare! With virtualization, you can have a replacement server running within minutes. Cloud computing takes this a step further, offering scalable, on-demand resources that can be accessed from anywhere with an internet connection. This removes the reliance on physical infrastructure, providing a highly resilient and flexible recovery solution. For example, a company experiencing a fire at its primary data center could quickly migrate its operations to a cloud-based environment, minimizing downtime and ensuring business continuity.
Failover and Failback Mechanisms
Failover mechanisms are your automated escape routes. These systems automatically switch operations to a backup system when the primary system fails. Think of it as a high-tech version of a backup generator, but for your entire IT infrastructure. The implementation typically involves redundant systems and robust network configurations. Failback, on the other hand, is the process of returning operations to the primary system once it’s been repaired or restored. This requires careful planning and testing to ensure a smooth transition. A well-designed failover and failback system should be transparent to end-users, minimizing disruption during the entire process. For example, a bank might use a failover system to instantly redirect customer transactions to a backup server during a power outage, preventing service interruptions.
Technology Considerations for Different Disaster Types
The technology required for disaster recovery varies depending on the nature of the disaster. A natural disaster like a hurricane requires different considerations than a cyberattack or a hardware failure. For example, a hurricane might necessitate geographically diverse backups and robust communication systems, while a cyberattack necessitates strong security protocols and incident response plans. Hardware failure, on the other hand, might be mitigated by redundant components and automated failover systems. The key is to tailor your technology strategy to the specific risks your organization faces.
Essential Technologies for Effective Disaster Recovery
A robust disaster recovery plan needs the right tools. Here’s a list of essential technologies:
- Redundant Servers and Network Infrastructure: Having backup systems ready to take over instantly is crucial. This ensures that if one system fails, another is immediately available to maintain operations.
- Data Backup and Replication Systems: Regular, automated backups are non-negotiable. Replication ensures that data is available in multiple locations, reducing the risk of total data loss.
- Virtualization Software: Allows for quick creation and deployment of virtual machines, enabling rapid recovery.
- Cloud Computing Platforms: Provides scalable and resilient infrastructure for disaster recovery operations.
- Disaster Recovery as a Service (DRaaS): Outsourcing disaster recovery management to a specialized provider can simplify the process and reduce the burden on internal IT teams.
- Network Monitoring and Alerting Systems: Provides real-time visibility into network performance, enabling proactive identification and resolution of potential issues.
- Security Information and Event Management (SIEM) Systems: Crucial for detecting and responding to cyberattacks, a major cause of data loss.
Legal and Compliance Requirements
Navigating the legal landscape of disaster recovery might seem like traversing a minefield blindfolded, but fear not! With the right preparation, you can avoid the explosive consequences of non-compliance and emerge victorious. This section Artikels the essential legal and regulatory considerations to ensure your disaster recovery plan doesn’t just protect your business, but also keeps you on the right side of the law.
Understanding legal and regulatory requirements concerning data protection and disaster recovery is crucial for maintaining operational continuity and avoiding hefty fines (or worse!). Compliance isn’t just about ticking boxes; it’s about demonstrating a commitment to responsible data handling and safeguarding sensitive information. This includes adhering to industry standards and best practices, which can vary depending on your industry, location, and the type of data you handle.
Relevant Legal and Regulatory Frameworks
Data protection laws, such as GDPR (General Data Protection Regulation) in Europe and CCPA (California Consumer Privacy Act) in the US, mandate specific procedures for handling personal data, including data backups and recovery. Failure to comply can result in significant financial penalties and reputational damage. Other regulations, like HIPAA (Health Insurance Portability and Accountability Act) in the US for healthcare data, and industry-specific standards (like PCI DSS for payment card data), further define the legal requirements for data security and disaster recovery. Understanding these regulations is paramount, and seeking legal counsel is highly recommended to ensure full compliance.
Compliance with Industry Standards and Best Practices
Adherence to industry standards and best practices, such as those established by NIST (National Institute of Standards and Technology) or ISO (International Organization for Standardization), demonstrates a proactive approach to risk management and strengthens your organization’s security posture. These frameworks provide comprehensive guidelines for developing and implementing robust disaster recovery plans, including data security measures, incident response procedures, and business continuity strategies. Following these best practices not only mitigates legal risks but also enhances the effectiveness of your disaster recovery efforts. For example, ISO 27001 provides a framework for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). This includes aspects crucial to disaster recovery, like data backup and recovery procedures.
Data Security and Privacy Procedures During Recovery
Maintaining data security and privacy throughout the recovery process is paramount. This involves implementing strict access controls, encryption protocols, and data sanitization procedures. All recovery activities should be meticulously documented, and access to sensitive data should be limited to authorized personnel only. For example, encrypting backup data both at rest and in transit significantly reduces the risk of data breaches during a recovery operation. Regular security audits and penetration testing can further identify vulnerabilities and ensure the effectiveness of implemented security controls. Imagine the scene: your data center is underwater, but your meticulously encrypted backups are safely stored in the cloud – a testament to well-executed data security protocols.
Documentation for Compliance Demonstration
Comprehensive documentation is essential for demonstrating compliance with legal and regulatory requirements. This includes policies, procedures, risk assessments, audit reports, incident response logs, and training records. Maintaining a well-organized and up-to-date documentation repository is crucial for demonstrating compliance during audits or investigations. For instance, a detailed incident response plan outlining steps to take in case of a data breach, along with documented evidence of its execution, would be invaluable in proving your organization’s commitment to data protection. Consider this documentation as your legal shield – it protects you from potential repercussions and showcases your dedication to responsible data handling.
Last Point: Disaster Recovery Planning Checklist
So, there you have it – a journey through the sometimes-scary, often-tedious, but ultimately essential world of disaster recovery planning. While the prospect of a major disaster might seem daunting, a well-structured plan armed with this checklist will transform fear into a manageable, and perhaps even slightly amusing, challenge. Remember, preparation is key. A little proactive planning can save you a whole lot of heartache (and possibly your business!). Now go forth and conquer those potential disasters! (But maybe keep some extra batteries handy, just in case.)
Question Bank
What’s the difference between a hot site and a cold site?
A hot site is a fully operational backup facility ready to go immediately. A cold site is a shell – it has the space and infrastructure, but needs equipment and data to be set up.
How often should I test my disaster recovery plan?
Regular testing is crucial! Aim for at least annual full-scale or tabletop exercises, with more frequent smaller tests of individual components.
What if my disaster recovery plan doesn’t cover *this* specific event?
Even the best plans can’t anticipate everything. The key is to have a flexible plan that allows for adaptation and improvisation. Regular reviews and updates are vital.
What’s the role of insurance in disaster recovery?
Insurance provides financial protection against losses, but it doesn’t replace a robust disaster recovery plan. Consider it a safety net, not a primary strategy.