Operational risk, the ever-present shadow lurking within every organization, threatens efficiency, profitability, and even survival. Understanding and mitigating these risks is no longer a luxury; it’s a necessity in today’s interconnected and volatile business landscape. This guide delves into the multifaceted nature of operational risk, exploring its origins, assessment, mitigation, and the crucial role of operational resilience.
From identifying potential vulnerabilities across diverse industries to implementing robust mitigation strategies and fostering a culture of risk awareness, we’ll examine practical approaches and best practices. We’ll also consider the impact of technological advancements and globalization on operational risk, emphasizing the need for proactive and adaptable risk management frameworks.
Defining Operational Risk
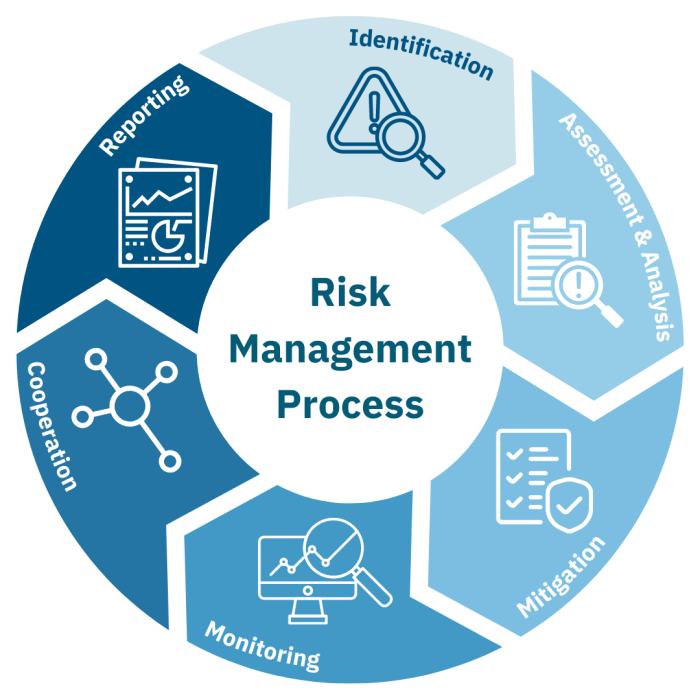
Operational risk is the risk of losses resulting from inadequate or failed internal processes, people, and systems, or from external events. It encompasses a wide range of potential disruptions, from minor inconveniences to catastrophic failures, impacting an organization’s ability to achieve its objectives. These losses can be financial, reputational, or even lead to legal liabilities. Understanding and mitigating operational risk is crucial for the long-term sustainability and success of any organization.
Operational risk differs significantly from other types of risk. Financial risk, for instance, relates to losses arising from market fluctuations, credit defaults, or liquidity issues. Strategic risk concerns the potential for failure due to poor business decisions or ineffective strategies. Compliance risk focuses on the potential for legal or regulatory penalties due to non-compliance. Operational risk, while often intertwined with these other risks, is distinct in its focus on internal processes and controls.
Operational Risk Characteristics and Evolution
Operational risk possesses several key characteristics. It’s inherently difficult to quantify precisely, as many contributing factors are often intangible or unpredictable. The impact of operational risk events can vary greatly, ranging from minor disruptions to significant financial losses and reputational damage. Moreover, the landscape of operational risk is constantly evolving. Technological advancements, globalization, and increasing regulatory scrutiny all contribute to new and emerging threats. For example, the rise of cyber threats has significantly increased operational risk for businesses of all sizes, requiring new and adaptive mitigation strategies. The increasing reliance on complex interconnected systems amplifies the potential impact of a single point of failure, highlighting the interconnected nature of operational risks and the need for holistic risk management. The COVID-19 pandemic serves as a stark reminder of the unpredictable nature of operational risk, demonstrating how unforeseen external events can severely disrupt operations and supply chains.
Distinguishing Operational Risk from Other Risk Types
A comparison table can effectively illustrate the differences between operational, financial, strategic, and compliance risks:
| Risk Type | Source | Examples | Impact |
|---|---|---|---|
| Operational Risk | Internal processes, people, systems, external events | System failures, fraud, human error, natural disasters | Financial losses, reputational damage, legal liabilities, business disruption |
| Financial Risk | Market fluctuations, credit defaults, liquidity issues | Interest rate changes, currency fluctuations, loan defaults | Financial losses, reduced profitability |
| Strategic Risk | Poor business decisions, ineffective strategies, competitive pressures | Market entry failures, product failures, loss of market share | Reduced profitability, loss of market position, business failure |
| Compliance Risk | Non-compliance with laws and regulations | Data breaches, violations of environmental regulations, anti-trust violations | Fines, penalties, legal action, reputational damage |
Identifying Operational Risk Sources
Operational risk, stemming from inadequate or failed internal processes, people, and systems, or from external events, poses a significant threat to organizations across various sectors. Understanding the diverse sources of these risks is crucial for effective mitigation strategies. This section will explore common operational risk sources across different industries and examine the emerging challenges posed by technological advancements and globalization.
Identifying operational risk sources requires a systematic approach. It involves analyzing internal processes, external factors, and the interaction between them. A comprehensive risk assessment should consider both the likelihood and potential impact of each identified risk.
Categorization of Operational Risk Sources Across Industries
The following table categorizes common operational risk sources across several industries. Note that these are not exhaustive, and the specific risks and their relative importance will vary depending on the size, complexity, and specific activities of an organization.
| Industry | Risk Source | Description | Mitigation Strategy |
|---|---|---|---|
| Finance | Fraud | Internal or external fraudulent activities, such as embezzlement, identity theft, or market manipulation. | Robust internal controls, employee background checks, fraud detection systems, and regular audits. |
| Healthcare | Data breaches | Unauthorized access to or disclosure of sensitive patient information, leading to reputational damage and legal liabilities. | Strong cybersecurity measures, employee training on data privacy, and incident response plans. |
| Manufacturing | Equipment malfunction | Failures in machinery or equipment leading to production downtime, product defects, and potential safety hazards. | Regular equipment maintenance, preventative measures, and robust quality control processes. |
| Finance | Regulatory non-compliance | Failure to adhere to relevant laws and regulations, resulting in fines, penalties, and reputational damage. | Comprehensive compliance programs, regular training for employees, and effective monitoring systems. |
| Healthcare | Medical errors | Mistakes in diagnosis, treatment, or medication administration, leading to patient harm and legal action. | Improved training protocols, standardized procedures, and robust quality assurance programs. |
| Manufacturing | Supply chain disruptions | Interruptions in the supply of raw materials or components, leading to production delays and increased costs. | Diversification of suppliers, robust inventory management, and contingency planning. |
Emerging Operational Risks Driven by Technological Advancements and Globalization
Technological advancements and globalization introduce new and evolving operational risks. The interconnected nature of global supply chains and the increasing reliance on technology create vulnerabilities that require proactive risk management strategies.
For example, the increasing reliance on cloud computing introduces risks related to data security and system availability. Cyberattacks targeting cloud-based systems can disrupt operations, compromise sensitive data, and lead to significant financial losses. Similarly, the rise of artificial intelligence and machine learning introduces new ethical and legal considerations, as well as potential risks related to algorithmic bias and system failures.
Globalization increases the complexity of supply chains, making them more vulnerable to disruptions caused by geopolitical events, natural disasters, or pandemics. The interconnectedness of global markets also means that operational risks in one part of the world can quickly spread to others.
Examples of Operational Risk Events and Their Consequences
Numerous examples illustrate the severity and potential impact of operational risk events. Consider the 2012 Knight Capital Group trading error, where a software glitch resulted in the firm losing $440 million in a matter of minutes. This highlighted the significant financial consequences that can arise from inadequate testing and oversight of technological systems.
Another example is the 2017 Equifax data breach, which exposed the personal information of 147 million people. This incident resulted in significant financial losses for Equifax, as well as reputational damage and legal liabilities. The breach underscored the importance of robust cybersecurity measures and effective data protection practices.
These examples demonstrate that operational risks can have far-reaching consequences, impacting not only the organization’s financial performance but also its reputation, customer relationships, and even its legal standing. Proactive risk management is therefore crucial for mitigating these potential impacts.
Assessing Operational Risk
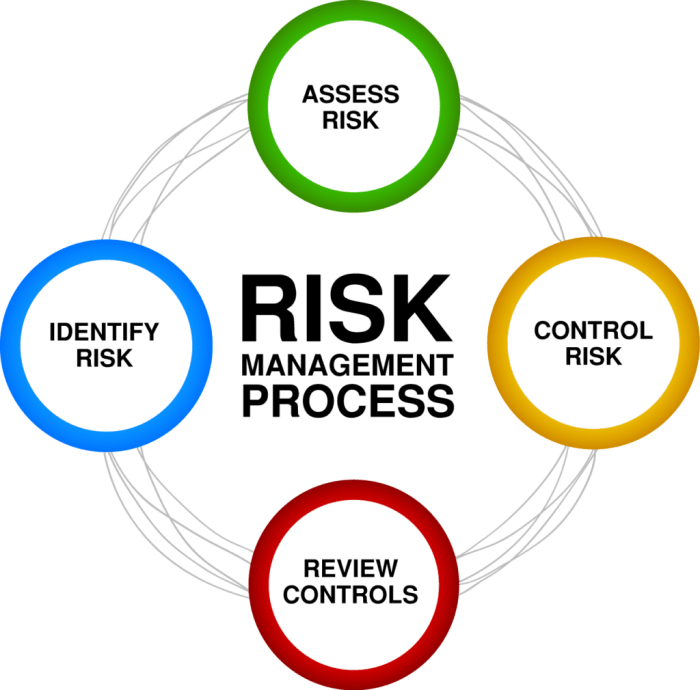
Assessing operational risk involves understanding the likelihood and potential impact of operational disruptions. This process is crucial for developing effective mitigation strategies and ensuring business continuity. A robust assessment considers both qualitative and quantitative factors, providing a comprehensive view of the organization’s vulnerability.
Various methods exist for assessing and quantifying operational risk, each with its strengths and weaknesses. The choice of method depends on factors such as the organization’s size, complexity, risk appetite, and available resources. A combination of qualitative and quantitative techniques is often employed to achieve a balanced and comprehensive assessment.
Qualitative Operational Risk Assessment Methods
Qualitative methods rely on expert judgment and experience to assess operational risks. They are often used when quantitative data is scarce or unreliable. These methods are valuable for identifying potential risks and prioritizing them based on their perceived likelihood and impact. They are particularly useful in the early stages of risk assessment, providing a framework for further quantitative analysis.
Common qualitative methods include:
- Risk workshops and brainstorming sessions: These bring together experts from different departments to identify and discuss potential risks.
- Checklists and questionnaires: These structured tools help systematically identify potential risks based on industry best practices and historical data.
- Scenario analysis: This involves considering various potential events and their potential impact on the organization.
- SWOT analysis: This examines the organization’s strengths, weaknesses, opportunities, and threats to identify potential operational risks.
Quantitative Operational Risk Assessment Methods
Quantitative methods use numerical data to measure and quantify operational risks. These methods provide a more precise assessment of risk, allowing for more informed decision-making. However, they often require significant data collection and analysis, and the accuracy of the results depends on the quality of the data used.
Common quantitative methods include:
- Loss databases: These databases contain historical data on operational losses, which can be used to estimate the frequency and severity of future losses. For example, a bank might use a loss database to estimate the frequency and severity of fraud losses.
- Statistical modeling: This involves using statistical techniques to model the probability and impact of operational risks. This could involve developing a model to predict the likelihood of a system failure based on historical data.
- Monte Carlo simulation: This technique uses random sampling to simulate the potential outcomes of operational risks, providing a range of possible losses. For example, a company could use Monte Carlo simulation to estimate the potential financial impact of a supply chain disruption.
Framework for Evaluating Likelihood and Impact
A common framework for evaluating operational risks involves creating a matrix that assesses both the likelihood and impact of identified risks. This matrix typically uses a scale to rank both likelihood (e.g., low, medium, high) and impact (e.g., low, medium, high, catastrophic). The combination of likelihood and impact determines the overall risk level, guiding prioritization and resource allocation.
For example, a risk with high likelihood and high impact would be considered a high-priority risk requiring immediate attention. Conversely, a risk with low likelihood and low impact might be considered a low priority.
| Likelihood | Low Impact | Medium Impact | High Impact | Catastrophic Impact |
|---|---|---|---|---|
| Low | Low | Medium | High | High |
| Medium | Medium | Medium-High | High | Critical |
| High | High | High | Critical | Critical |
Comparison of Risk Assessment Methodologies
Different methodologies offer varying strengths and weaknesses. Qualitative methods are efficient for initial risk identification and prioritization, but lack the precision of quantitative approaches. Quantitative methods offer precise measurements but rely heavily on data availability and quality, and may not capture all qualitative aspects of risk. A balanced approach using both is often the most effective.
For instance, a qualitative assessment might reveal a vulnerability in a new software system, while a quantitative analysis could estimate the potential financial losses associated with a system failure.
Implementing Risk Mitigation Strategies
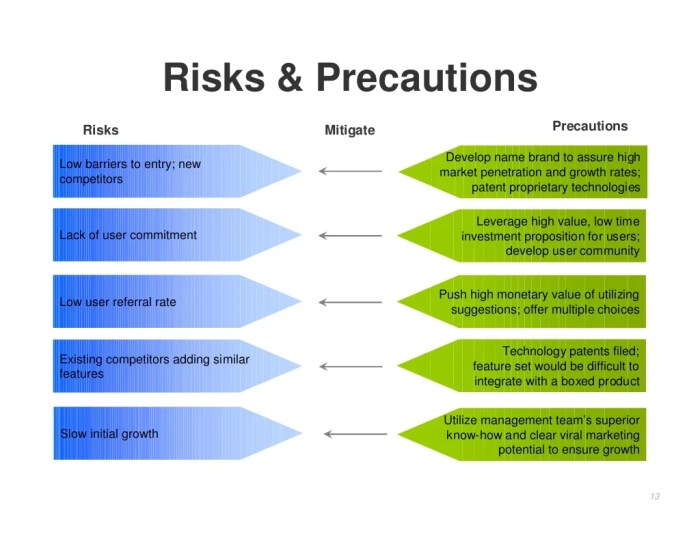
Effective operational risk mitigation requires a proactive and comprehensive approach, encompassing both preventative and reactive strategies. A well-structured program minimizes the likelihood of operational failures and ensures swift, effective responses when incidents do occur. This involves a combination of robust controls, technological advancements, and a strong risk culture within the organization.
Implementing effective risk mitigation strategies involves a multi-faceted approach that balances proactive prevention with reactive responses to incidents. The aim is to reduce the frequency and severity of operational risks, ultimately protecting the organization’s assets, reputation, and profitability.
Preventative Risk Mitigation Strategies
Preventative measures focus on proactively reducing the likelihood of operational risks occurring. These strategies aim to identify and address vulnerabilities before they can be exploited. A strong emphasis on prevention is significantly more cost-effective in the long run than dealing with the aftermath of an operational failure.
- Robust Internal Controls: Implementing strong internal controls, such as segregation of duties, authorization matrices, and regular audits, minimizes the risk of fraud, errors, and unauthorized activities. For example, a bank might implement a four-eyes principle for large transactions, requiring two authorized individuals to approve each one.
- Employee Training and Awareness: Regular training programs educating employees on operational risks, compliance procedures, and security best practices significantly reduce human error. For example, training on phishing scams can prevent employees from falling victim to cyberattacks.
- Process Improvement and Automation: Streamlining processes and automating repetitive tasks reduces the chance of manual errors and increases efficiency. For example, automating invoice processing can reduce errors and delays.
- Vendor Risk Management: Thoroughly vetting and monitoring third-party vendors to ensure they meet required security and compliance standards mitigates risks associated with outsourcing. For example, conducting regular security audits of key vendors.
- Business Continuity and Disaster Recovery Planning: Developing comprehensive plans to ensure business continuity in the event of disruptions, such as natural disasters or cyberattacks, minimizes downtime and financial losses. This includes having backup systems and data recovery plans.
Reactive Risk Mitigation Strategies
Reactive measures focus on responding effectively to operational risk events that have already occurred. The goal is to minimize the impact and prevent similar incidents in the future. A well-defined incident response plan is crucial for effective reactive mitigation.
- Incident Response Plan: A detailed plan outlining steps to be taken in the event of an operational incident, including communication protocols, investigation procedures, and remediation strategies. For example, a plan outlining how to respond to a data breach, including notification procedures and legal compliance.
- Loss Control and Damage Mitigation: Implementing measures to minimize the impact of an operational loss, such as containing the damage, recovering lost data, and communicating with affected parties. For example, implementing a crisis communication plan to address a product recall.
- Post-Incident Review and Analysis: Conducting thorough reviews of operational incidents to identify root causes, learn from mistakes, and implement corrective actions to prevent recurrence. For example, conducting a root cause analysis of a system failure to identify weaknesses in the system design.
The Role of Technology in Enhancing Operational Risk Management
Technology plays a crucial role in enhancing operational risk management by providing tools and capabilities to improve efficiency, accuracy, and control. This includes leveraging data analytics to identify patterns and predict potential risks, automating processes to reduce human error, and implementing advanced security measures to protect against cyber threats.
- Data Analytics and Predictive Modeling: Utilizing data analytics to identify trends, patterns, and anomalies in operational data to predict potential risks and proactively mitigate them. For example, using machine learning to detect fraudulent transactions.
- Automation and Robotics Process Automation (RPA): Automating repetitive tasks to reduce human error, improve efficiency, and free up staff for more strategic activities. For example, automating invoice processing or customer service requests.
- Cybersecurity Technologies: Implementing advanced cybersecurity measures, such as intrusion detection systems, firewalls, and encryption, to protect against cyber threats and data breaches. For example, implementing multi-factor authentication to secure access to sensitive systems.
- Real-time Monitoring and Alerting Systems: Implementing systems that monitor operational processes in real-time and provide alerts when potential problems arise, enabling swift intervention. For example, monitoring system performance metrics to detect potential outages.
Implementing a Comprehensive Operational Risk Mitigation Program
Implementing a successful operational risk mitigation program requires a structured approach involving several key steps. A phased implementation allows for a manageable rollout and allows for adjustments based on learnings along the way.
- Risk Assessment and Identification: Conduct a thorough assessment of the organization’s operational risks, identifying potential sources and their likelihood and impact.
- Strategy Development: Develop a comprehensive risk mitigation strategy that Artikels specific preventative and reactive measures for each identified risk.
- Implementation and Resource Allocation: Implement the chosen mitigation strategies, allocating the necessary resources (personnel, technology, budget) to ensure effectiveness.
- Monitoring and Evaluation: Regularly monitor the effectiveness of the mitigation strategies, using key performance indicators (KPIs) to track progress and identify areas for improvement.
- Continuous Improvement: Continuously review and refine the risk mitigation program based on lessons learned, changes in the business environment, and emerging risks.
Monitoring and Reporting
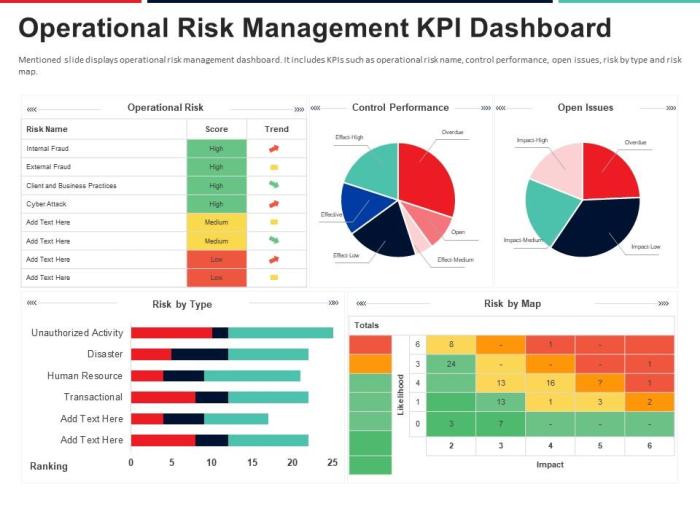
Effective monitoring and reporting are crucial for ensuring that operational risk mitigation strategies remain relevant and effective. A robust system allows for proactive identification of emerging risks, assessment of the effectiveness of controls, and timely responses to potential threats. This section Artikels the key components of such a system.
Establishing Key Risk Indicators (KRIs) involves a careful selection of metrics that provide early warning signals of potential operational risk events. These indicators should be specific, measurable, achievable, relevant, and time-bound (SMART). Regular monitoring of these KRIs enables proactive risk management and facilitates timely interventions.
Key Risk Indicator (KRI) Establishment
The process of establishing KRIs begins with a thorough understanding of the organization’s operational risks. This involves reviewing existing risk assessments, analyzing historical data on operational losses, and consulting with subject matter experts across various departments. Once potential risks are identified, appropriate KRIs can be selected. For example, a bank might use the number of customer complaints as a KRI for operational risk in its customer service department, while a manufacturing company might track the number of production line stoppages as a KRI for operational risk related to equipment malfunction. The frequency of monitoring should be tailored to the nature and severity of the risk. High-impact, high-frequency risks might require daily monitoring, while others might only need to be reviewed monthly or quarterly.
Operational Risk Event Tracking and Reporting System
A well-designed system for tracking and reporting operational risk events should capture key details about each event, including the date, time, location, type of event, root cause, impact, and corrective actions taken. This information can be collected through various channels, such as incident reports, internal audits, and regulatory examinations. The system should allow for the aggregation and analysis of this data to identify trends and patterns in operational risk events. A centralized database, potentially linked to a reporting dashboard, can facilitate efficient data management and reporting. The system should also include features for tracking the effectiveness of implemented mitigation strategies. For example, tracking the reduction in customer complaints after implementing a new customer service training program would demonstrate the success of a mitigation strategy.
Communicating Operational Risk Information
Effective communication of operational risk information is essential for fostering a strong risk culture within the organization. This involves tailoring communication to the specific needs and understanding of different stakeholder groups. Senior management requires high-level summaries of key risks and mitigation efforts, while operational staff need more detailed information relevant to their specific roles and responsibilities. Regular reporting, including both scheduled reports and ad-hoc updates on significant events, should be implemented. Visualizations, such as charts and graphs, can be highly effective in communicating complex information concisely. Transparency and open communication are key to building trust and ensuring that operational risk management is taken seriously across the organization. For example, regular updates to the board of directors on key risk indicators and significant events can demonstrate a commitment to effective risk management.
Operational Resilience

Operational resilience goes beyond simply managing operational risks; it’s about the ability of an organization to withstand and recover from disruptions, continuing to deliver critical services and functions. In today’s interconnected and volatile business environment, characterized by increasing frequency and severity of disruptions (cyberattacks, natural disasters, pandemics, etc.), operational resilience is no longer a luxury but a necessity for survival and sustained success. A resilient organization can absorb shocks, adapt to change, and emerge stronger from adversity.
Operational resilience ensures business continuity and minimizes the impact of disruptions on stakeholders, including customers, employees, and investors. It’s a proactive approach that anticipates potential threats and develops robust strategies to mitigate their impact, safeguarding the organization’s reputation, financial stability, and long-term viability.
Key Elements of Building Operational Resilience
Building operational resilience requires a holistic and integrated approach, encompassing several key elements. These elements work in concert to create a robust and adaptable organization capable of withstanding and recovering from a wide range of disruptions.
Business continuity planning (BCP) and disaster recovery (DR) are fundamental components of operational resilience. BCP focuses on maintaining essential business functions during and after a disruption, while DR specifically addresses the recovery of IT systems and data. Effective BCP and DR plans require thorough risk assessments, clear communication protocols, robust technology infrastructure, and regular testing and updates. They should Artikel detailed procedures for various scenarios, ensuring a swift and coordinated response to minimize downtime and operational losses. Beyond BCP and DR, other critical elements include robust IT infrastructure, diverse supply chains, skilled and adaptable workforce, and strong governance and oversight.
Scenario Illustrating the Importance of Operational Resilience
Imagine a major financial institution experiencing a widespread ransomware attack that cripples its core banking systems. Without robust operational resilience measures, the consequences could be catastrophic. Customer transactions would be halted, leading to significant financial losses and reputational damage. Employee access to critical systems would be disrupted, impacting productivity and potentially leading to data breaches. Regulatory scrutiny and potential fines would further exacerbate the situation. However, an organization with a well-defined operational resilience strategy, including a comprehensive BCP and DR plan, would be better equipped to handle the crisis. The institution might have redundant systems and data backups, allowing for a quick recovery. Its communication protocols would ensure timely updates to customers and stakeholders. Pre-established escalation procedures would facilitate a swift and coordinated response from IT, security, and management teams. The organization’s ability to quickly recover and resume operations would minimize the long-term impact of the attack, protecting its financial stability, reputation, and customer trust.
Human Factors in Operational Risk
Human error is a significant driver of operational risk events across various industries. Understanding the role of human factors is crucial for effective risk mitigation. This section explores the impact of human error, strategies for improving employee preparedness, and methods for cultivating a robust safety culture.
Human error contributes significantly to operational risk events through various mechanisms, including negligence, mistakes, and violations of established procedures. These errors can stem from a multitude of factors, such as inadequate training, fatigue, stress, poor communication, and a lack of awareness regarding risk management protocols. The consequences can range from minor inconveniences to catastrophic failures, impacting financial performance, reputation, and even safety. For instance, a simple data entry error could lead to significant financial losses, while a lapse in safety procedures might result in a workplace accident.
The Role of Human Error in Operational Risk Events
Human error manifests in numerous ways within an operational context. These errors can be categorized as slips (unintended actions), lapses (memory failures), mistakes (errors in planning or decision-making), and violations (deliberate deviations from procedures). The impact of each error type varies depending on the context and the criticality of the task. For example, a slip in data entry might be easily corrected, while a mistake in a critical process could have far-reaching consequences. Effective risk management necessitates understanding these different error types and designing systems and processes that minimize their occurrence and impact.
Strategies for Improving Employee Training and Awareness
Comprehensive training programs are essential for mitigating human-related operational risks. These programs should go beyond basic procedural training and encompass risk awareness, decision-making skills, and effective communication techniques. Simulations and scenario-based training can provide valuable experience in handling real-world situations. Regular refresher courses and updates on new procedures or technologies are also vital to maintain employee competency and keep them informed about evolving risk landscapes. Furthermore, providing clear and accessible resources, such as checklists, guidelines, and readily available support, can reduce the likelihood of errors.
Methods for Fostering a Culture of Safety and Risk Awareness
Creating a culture of safety and risk awareness requires a multifaceted approach. Open communication channels should be established to encourage employees to report near misses and incidents without fear of retribution. This information can then be used to identify areas for improvement and prevent future occurrences. Regular safety meetings and awareness campaigns can reinforce safety protocols and promote a shared commitment to risk mitigation. Leadership must actively champion safety initiatives and demonstrate a clear commitment to a culture where safety is prioritized above all else. Recognizing and rewarding safe behaviors can also incentivize employees to prioritize safety in their daily work. A strong safety culture is not just about compliance; it’s about fostering a mindset where everyone feels empowered to identify and address potential risks.
Regulatory Compliance and Operational Risk
Effective operational risk management is inextricably linked to regulatory compliance. Meeting regulatory requirements not only avoids penalties but also fosters a robust risk management culture, ultimately contributing to a more resilient and stable organization. This section explores the relationship between regulatory compliance and operational risk mitigation.
Regulatory requirements related to operational risk management vary significantly across jurisdictions, reflecting differing priorities and levels of financial market development. These regulations often mandate specific risk management frameworks, internal controls, and reporting procedures. Compliance with these regulations demonstrates a commitment to sound risk management practices and can enhance an organization’s reputation and stakeholder confidence.
Regulatory Frameworks Addressing Operational Risk
Several key regulatory frameworks globally address operational risk. These frameworks often overlap and share common principles, but their specific requirements and enforcement mechanisms differ. For example, the Basel Committee on Banking Supervision (BCBS) provides guidelines for banks on operational risk management, influencing regulatory approaches worldwide. These guidelines encourage a comprehensive approach, encompassing risk identification, assessment, mitigation, and monitoring. Similarly, the Dodd-Frank Act in the United States, introduced in response to the 2008 financial crisis, includes provisions aimed at strengthening operational risk management within financial institutions. Other jurisdictions have implemented their own tailored regulations, reflecting their unique financial landscapes and risk profiles. For instance, the European Union’s regulatory framework for financial institutions encompasses directives and regulations that specifically address operational risk. These regulations often require institutions to maintain robust internal control systems, conduct regular risk assessments, and implement effective mitigation strategies. Failure to comply with these regulations can result in significant financial penalties and reputational damage.
Compliance and Effective Operational Risk Mitigation
Compliance with regulations acts as a catalyst for effective operational risk mitigation. The process of adhering to regulatory standards often necessitates a thorough review and strengthening of internal controls, risk assessment processes, and reporting mechanisms. This enforced scrutiny identifies vulnerabilities and weaknesses in existing systems, prompting organizations to proactively address potential risks. Furthermore, regulatory compliance fosters a culture of accountability and transparency within an organization. By establishing clear expectations and responsibilities for risk management, compliance promotes a more disciplined approach to risk identification and mitigation. The need to document risk assessment processes, mitigation strategies, and monitoring activities strengthens an organization’s overall risk management framework. This enhanced transparency also improves communication and collaboration across different departments, contributing to a more holistic and effective risk management approach. Finally, regular audits and inspections conducted by regulatory bodies provide independent validation of an organization’s risk management practices, further strengthening the effectiveness of its operational risk mitigation efforts.
Ending Remarks

Effectively mitigating operational risk requires a holistic approach, encompassing proactive identification, thorough assessment, strategic mitigation, and continuous monitoring. By understanding the diverse sources of operational risk, implementing robust strategies, and fostering a culture of risk awareness, organizations can significantly enhance their resilience, protect their assets, and ensure long-term sustainability. The journey towards operational excellence is a continuous process of learning, adapting, and refining risk management practices.
General Inquiries
What is the difference between operational risk and financial risk?
Operational risk focuses on internal processes, people, and systems, while financial risk relates to market fluctuations, credit defaults, and liquidity issues. They are distinct but interconnected, as operational failures can trigger financial losses.
How can small businesses effectively manage operational risk?
Small businesses can leverage simple, yet effective strategies like thorough employee training, robust documentation of processes, regular system backups, and outsourcing non-core functions to mitigate operational risks.
What is the role of insurance in operational risk mitigation?
Insurance can act as a safety net, covering potential financial losses resulting from operational failures. However, it shouldn’t replace proactive risk management; instead, it complements a comprehensive mitigation strategy.