Effective risk management is no longer a luxury but a necessity for organizations navigating today’s complex and volatile business environment. From identifying potential threats to implementing robust mitigation strategies, a proactive approach is crucial for ensuring stability, growth, and ultimately, survival. This guide delves into the core principles and practical applications of comprehensive risk management, equipping you with the knowledge and tools to navigate uncertainty with confidence.
We will explore the entire risk management lifecycle, from initial risk identification and assessment through to the implementation of response strategies and ongoing monitoring. We will examine various frameworks, methodologies, and technological tools, providing a holistic understanding of how to integrate risk management into your daily operations and decision-making processes. The aim is to empower you to build a resilient organization capable of weathering any storm.
Defining Risk Management Strategies
Effective risk management is crucial for the success and sustainability of any organization, regardless of size or industry. It involves proactively identifying, analyzing, and responding to potential threats and opportunities that could impact the achievement of objectives. A well-defined risk management strategy allows for informed decision-making, resource allocation, and the mitigation of potential negative consequences.
Core Principles of Effective Risk Management
Effective risk management operates on several key principles. These include a commitment from leadership, a comprehensive and integrated approach, a focus on context and objectives, a participatory and inclusive process, and a commitment to continuous improvement. The strategy should be tailored to the specific context and objectives of the organization, considering its unique risk profile and tolerance levels. Furthermore, a systematic and disciplined approach, coupled with regular monitoring and review, is essential for maintaining the effectiveness of the strategy.
The Risk Management Process
The risk management process is typically iterative and cyclical, involving four key stages: identification, analysis, response, and monitoring. Risk identification involves systematically identifying all potential risks that could impact the organization. This can involve brainstorming sessions, checklists, and hazard analysis techniques. Risk analysis involves evaluating the likelihood and potential impact of each identified risk. This often uses qualitative or quantitative methods to assess the severity and urgency of each risk. Risk response involves developing and implementing strategies to manage the identified risks, such as risk avoidance, mitigation, transfer, or acceptance. Finally, risk monitoring involves tracking the effectiveness of the implemented responses and making adjustments as needed. This ensures that the risk management strategy remains relevant and effective over time.
Examples of Risk Management Frameworks
Several established frameworks provide guidance for implementing effective risk management strategies. One prominent example is ISO 31000, an internationally recognized standard that provides principles and guidelines for managing risks across all types of organizations. ISO 31000 emphasizes a holistic approach, integrating risk management into all aspects of decision-making. Other frameworks include COSO ERM (Committee of Sponsoring Organizations of the Treadway Commission Enterprise Risk Management), which focuses on enterprise-wide risk management, and NIST Cybersecurity Framework, tailored specifically for cybersecurity risks. These frameworks offer structured methodologies and best practices to aid in developing and implementing robust risk management strategies.
Comparison of Proactive and Reactive Risk Management Approaches
| Proactive Risk Management | Reactive Risk Management |
|---|---|
| Identifies and addresses risks *before* they occur. | Responds to risks *after* they have occurred. |
| Emphasizes prevention and mitigation. | Focuses on damage control and recovery. |
| Often involves predictive analysis and scenario planning. | Typically involves crisis management and incident response. |
| Generally more cost-effective in the long run. | Can lead to higher costs and reputational damage. |
| Example: Implementing robust cybersecurity measures to prevent data breaches. | Example: Responding to a data breach after it has already occurred. |
Risk Identification and Assessment

Effective risk identification and assessment are crucial first steps in any robust risk management strategy. Understanding potential threats and their potential impact allows organizations to prioritize resources and develop appropriate mitigation strategies. This section details methods for identifying risks, explores both qualitative and quantitative assessment techniques, and provides a template for documenting identified risks.
Methods for Identifying Potential Risks
Several methods can be employed to identify potential risks within an organization. A comprehensive approach often involves a combination of techniques to ensure a thorough and inclusive assessment. These methods leverage different perspectives and data sources to uncover a wide range of potential threats.
Common methods include brainstorming sessions involving cross-functional teams, check-lists based on industry best practices or previous incidents, SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis to examine the organization’s internal and external environment, and reviewing historical data, including incident reports and near misses. External sources such as industry reports, regulatory changes, and economic forecasts also provide valuable insights into potential risks. Finally, conducting interviews with key personnel across different departments can unearth risks that may not be apparent through other methods.
Qualitative and Quantitative Risk Assessment Techniques
Qualitative and quantitative risk assessment techniques offer different perspectives on evaluating identified risks. Qualitative assessments focus on descriptive attributes, while quantitative assessments use numerical data to provide a more precise evaluation.
Qualitative risk assessment often uses a matrix to assess risk likelihood and impact using descriptive scales (e.g., low, medium, high). This allows for a subjective evaluation based on expert judgment and experience. For example, a risk might be assessed as having a “high” likelihood and a “medium” impact, leading to an overall assessment of “high” risk. Quantitative risk assessment involves assigning numerical values to likelihood and impact, often expressed as probabilities and monetary values. This can involve complex calculations and statistical modeling to determine the potential financial loss associated with a particular risk. For instance, a quantitative assessment might estimate a 10% probability of a system failure resulting in a $1 million loss, yielding an expected monetary value (EMV) of $100,000.
Risk Register Template
A risk register is a crucial tool for documenting and tracking identified risks. The following table provides a template for a risk register.
| Risk Description | Likelihood | Impact | Response |
|---|---|---|---|
| Supplier failure to deliver critical components | Medium | High | Diversify suppliers, implement contingency planning |
| Cybersecurity breach | Low | High | Invest in robust security measures, employee training |
| Loss of key personnel | Medium | Medium | Succession planning, employee retention strategies |
| Regulatory changes | High | Medium | Monitor regulatory developments, adapt business practices |
Comparison of Risk Assessment Tools and Methodologies
Different risk assessment tools and methodologies offer varying levels of complexity and precision. The choice of tool depends on the organization’s specific needs and resources. For example, simple risk matrices provide a quick overview of risks, while more sophisticated tools, such as Monte Carlo simulations, allow for a more detailed analysis of the potential impact of multiple risks. Other tools might include Failure Mode and Effects Analysis (FMEA) for identifying potential failures in a system and Fault Tree Analysis (FTA) for tracing the causes of potential failures. The selection of the appropriate methodology depends on factors such as the complexity of the project or system, the availability of data, and the resources available for the assessment.
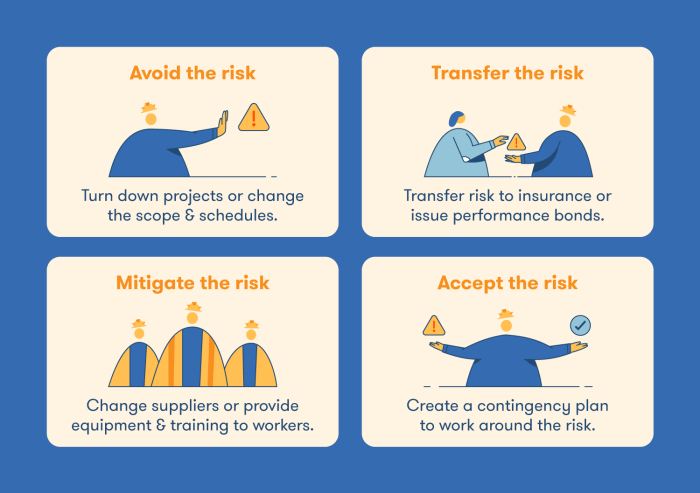
Risk Response Strategies
Once risks have been identified and assessed, the next crucial step is developing and implementing appropriate response strategies. Effective risk response involves a proactive approach to managing potential threats and capitalizing on opportunities. This involves carefully considering the impact and likelihood of each risk, and selecting the most suitable strategy to address it.
Risk Avoidance
Risk avoidance involves eliminating the risk entirely by not undertaking the activity that creates the risk. This is a straightforward approach, best suited for high-impact, high-likelihood risks where the potential negative consequences significantly outweigh the potential benefits. For example, a company might avoid investing in a new market with significant political instability, opting instead for a more stable region to minimize the risk of political upheaval disrupting operations. Another example could be a construction company choosing not to bid on a project in an area prone to severe weather events, thus avoiding potential delays and financial losses. The key is to weigh the potential loss against the potential gain. If the loss is significantly greater, avoidance is often the best option.
Risk Mitigation
Risk mitigation involves reducing the likelihood or impact of a risk. This approach is often preferred when complete avoidance isn’t feasible or practical. Mitigation strategies aim to minimize the potential negative consequences of a risk event. For instance, implementing robust cybersecurity measures to reduce the likelihood of a data breach is a mitigation strategy. Similarly, investing in backup power generators to mitigate the risk of production downtime during power outages is another example. Diversifying suppliers to reduce reliance on a single source and thus lessen the impact of supply chain disruptions is yet another effective mitigation technique. A detailed plan, as illustrated below, is crucial for successful mitigation.
Risk Transfer
Risk transfer involves shifting the responsibility for a risk to a third party. This is commonly achieved through insurance policies, outsourcing, or contracts. For example, purchasing insurance to cover potential liability claims transfers the financial risk associated with accidents or lawsuits to the insurance company. Outsourcing a manufacturing process to a supplier transfers the risk of production delays or quality control issues to the supplier. Contracts can also include clauses that shift specific risks to one party or another. The effectiveness of risk transfer depends on the ability of the third party to absorb the loss and the terms of the agreement.
Risk Acceptance
Risk acceptance involves acknowledging a risk and deciding to bear the consequences should the risk event occur. This strategy is typically employed for low-impact, low-likelihood risks where the cost of mitigation or transfer outweighs the potential loss. For example, a small business might accept the risk of minor equipment malfunctions, knowing that repairs would be relatively inexpensive. However, careful monitoring is still necessary even with accepted risks, as circumstances may change and what was previously a low-impact risk could escalate.
Mitigating Supply Chain Disruption: A Sample Plan
Supply chain disruptions represent a significant risk for many businesses. Here’s a plan outlining steps to mitigate this risk:
- Risk Identification: Identify specific vulnerabilities in the supply chain, such as reliance on single suppliers, geographical concentration of suppliers, or lack of inventory buffers.
- Risk Assessment: Evaluate the likelihood and impact of potential disruptions, considering factors like natural disasters, political instability, and pandemics.
- Mitigation Strategies:
- Diversify suppliers: Establish relationships with multiple suppliers in different geographical locations.
- Increase inventory levels: Maintain a buffer stock of critical materials to absorb potential supply shortages.
- Develop alternative sourcing options: Identify backup suppliers or alternative production methods.
- Improve supply chain visibility: Implement technology to track materials and monitor supply chain performance.
- Strengthen supplier relationships: Foster collaboration and communication with key suppliers.
- Implementation: Allocate resources, establish timelines, and assign responsibilities for implementing the mitigation strategies.
- Monitoring and Review: Regularly monitor the effectiveness of the mitigation strategies and adjust the plan as needed.
Prioritized Risk Response Strategies
Prioritizing risk response strategies is crucial for efficient resource allocation. A common approach is to rank risks based on a combination of likelihood and impact, using a matrix. High-impact, high-likelihood risks should be addressed first, typically through avoidance or mitigation. Low-impact, low-likelihood risks can often be accepted. Risks falling in between require careful consideration and a tailored response strategy. For instance, a risk with high impact but low likelihood might be addressed through a transfer strategy, while a high-likelihood, low-impact risk could be mitigated with relatively inexpensive measures. The specific prioritization will depend on the organization’s risk appetite and available resources.
Risk Monitoring and Control
Effective risk monitoring and control is crucial for ensuring that identified risks remain within acceptable tolerances and that risk response strategies are working as intended. A proactive approach to monitoring allows for early detection of emerging risks and facilitates timely adjustments to mitigate potential negative impacts. Without consistent oversight, even well-planned risk mitigation strategies can become ineffective over time.
Risk monitoring and control involves the continuous tracking and evaluation of risks throughout a project or organization’s lifecycle. This iterative process enables organizations to stay informed about the evolving risk landscape and to make informed decisions about resource allocation and strategic adjustments. The ultimate goal is to minimize potential losses and maximize opportunities.
Continuous Risk Monitoring and Reporting
Continuous risk monitoring and reporting provides a dynamic view of the organization’s risk profile. Regular reporting, whether daily, weekly, or monthly, depending on the criticality of the risks, ensures that stakeholders are informed about the current risk status and any changes that may require attention. This allows for proactive responses, reducing the likelihood of unexpected negative events. Reports should include key risk indicators (KRIs), the effectiveness of risk responses, and any emerging risks. For example, a construction company might monitor daily weather reports as a KRI, adjusting schedules and implementing safety measures to mitigate weather-related delays or accidents.
Tracking Key Risk Indicators (KRIs)
Tracking key risk indicators (KRIs) is fundamental to effective risk monitoring. KRIs are quantifiable metrics that provide early warning signals of potential problems. The selection of appropriate KRIs depends on the specific risks being monitored. Methods for tracking KRIs include using dashboards, spreadsheets, and specialized risk management software. For instance, a financial institution might track its loan default rate as a KRI, using a spreadsheet to monitor the percentage of loans that are delinquent. Changes in this rate above a predetermined threshold would trigger a review of the risk response strategies. Another example could be a manufacturing company tracking the number of defects per unit produced. A significant increase in this KRI might signal a need for improved quality control processes.
Using Risk Registers to Monitor Risk Response Effectiveness
Risk registers serve as central repositories for all identified risks, their associated responses, and their status. Regular review of the risk register is crucial for assessing the effectiveness of implemented risk responses. The register should be updated to reflect changes in risk levels and the success of mitigation efforts. For example, if a risk response involved implementing a new security system to reduce cyber threats, the risk register would track the number of successful cyberattacks before and after the system’s implementation. A decrease in the number of successful attacks would indicate the effectiveness of the risk response. Similarly, a project manager might use a risk register to track the progress of mitigation strategies for schedule delays.
Risk Monitoring and Control Process Flowchart
The following describes a flowchart illustrating the risk monitoring and control process. The flowchart starts with initiating the monitoring process, then proceeds to data collection, risk assessment, response effectiveness evaluation, reporting, and finally, adjusting the risk management plan as needed. The cyclical nature of the process emphasizes the continuous nature of risk management.
[Imagine a flowchart here. The flowchart would begin with a rectangle labeled “Initiate Risk Monitoring.” This would lead to a diamond labeled “Collect Data on KRIs and Risk Responses.” From the diamond, two paths would emerge: one leading to a rectangle labeled “Risk Assessment: Evaluate Risk Levels” and the other leading back to the “Collect Data” diamond. From the “Risk Assessment” rectangle, another path leads to a diamond labeled “Are Risk Responses Effective?” If yes, a path leads to a rectangle labeled “Report Status and Continue Monitoring.” If no, a path leads to a rectangle labeled “Adjust Risk Management Plan.” Finally, both paths from the “Report Status” and “Adjust Plan” rectangles would loop back to the “Initiate Risk Monitoring” rectangle, completing the cycle.]
Risk Management in Specific Contexts
Effective risk management is not a one-size-fits-all approach; its implementation varies significantly depending on the specific context. Factors such as industry regulations, organizational size and structure, and the nature of the business operations all play a crucial role in shaping a robust risk management framework. This section explores risk management in specific contexts, highlighting unique challenges and successful implementation strategies.
Risk Management in the Healthcare Industry
The healthcare industry faces a unique set of risks, including patient safety incidents, data breaches, regulatory non-compliance, and financial instability. Effective risk management in this sector requires a multi-faceted approach, encompassing clinical risk management, operational risk management, and financial risk management. For example, implementing robust infection control protocols minimizes the risk of hospital-acquired infections, while rigorous data security measures protect patient privacy and comply with HIPAA regulations. Failure to adequately manage these risks can lead to significant financial penalties, reputational damage, and even legal action.
Case Study: Successful Risk Management Implementation in a Hospital System
The Mayo Clinic, a renowned healthcare system, exemplifies successful risk management. Their comprehensive approach integrates risk identification and assessment across all departments, fostering a culture of safety and proactive risk mitigation. They utilize a sophisticated system for tracking and analyzing adverse events, enabling continuous improvement in patient safety protocols. This proactive approach, coupled with rigorous training and ongoing education for staff, significantly reduces the likelihood of medical errors and improves patient outcomes. Their success underscores the importance of a culture of safety and continuous improvement in effective healthcare risk management.
Risk Management Challenges in Small Businesses
Small businesses often face unique challenges in managing risk due to limited resources and expertise. They may lack dedicated risk management personnel and struggle to implement sophisticated risk assessment methodologies. This can lead to inadequate risk identification and a higher likelihood of significant disruptions from unforeseen events. However, even small businesses can benefit from implementing basic risk management practices, such as regular risk assessments, contingency planning, and effective insurance coverage. Focusing on the most critical risks and prioritizing resource allocation can help small businesses effectively manage their risk profiles despite limited resources.
Comparing Risk Management Approaches Across Industries
While the core principles of risk management remain consistent across industries, the specific risks and approaches vary considerably. For instance, the financial services industry focuses heavily on financial risk management, including market risk, credit risk, and operational risk, often employing sophisticated quantitative models. In contrast, the manufacturing industry prioritizes operational risks, such as supply chain disruptions, production failures, and workplace safety incidents. The technology sector faces unique challenges related to cybersecurity threats, intellectual property protection, and rapid technological change. These differences necessitate tailored risk management strategies that address the specific vulnerabilities and opportunities inherent in each industry.
Integrating Risk Management into Business Processes

Effective risk management isn’t a separate activity; it’s the seamless integration of risk consideration into the fabric of daily operations and strategic decision-making. By embedding risk management principles into all levels of the organization, businesses can proactively identify, assess, and mitigate potential threats, ultimately fostering resilience and enhancing overall performance. This proactive approach shifts the focus from reacting to crises to anticipating and preventing them.
Embedding risk management into daily operations and decision-making requires a cultural shift. It necessitates that risk awareness is not solely the responsibility of a dedicated risk management team, but rather a shared responsibility across all departments and levels of the organization. This requires clear communication, accessible tools, and consistent training to ensure that all employees understand their role in identifying and reporting potential risks. Regular risk assessments, integrated into routine processes, help maintain a current understanding of the organization’s risk profile.
Risk Management Integration in Project Management
Successful project management inherently involves managing risks. Integrating risk management into project lifecycles requires a structured approach. This includes identifying potential risks during the planning phase, using tools like SWOT analysis and risk registers to document and assess them. Throughout the project, regular monitoring and reporting mechanisms should be in place to track progress and identify emerging risks. Contingency plans, developed in advance for identified risks, allow for proactive responses, minimizing disruption and cost overruns. For example, a construction project might identify the risk of inclement weather delaying the schedule. The risk response could include securing weather insurance, having backup materials on hand, and developing a revised schedule that incorporates potential delays. This proactive approach, embedded in the project’s execution, prevents reactive firefighting.
Developing a Risk Management Training Program
A comprehensive training program is essential for effective risk management integration. The program should be tailored to different roles and responsibilities within the organization. For example, senior management training might focus on strategic risk assessment and decision-making, while operational staff training could concentrate on identifying and reporting hazards in their daily tasks. The program should include interactive workshops, case studies, and simulations to reinforce learning and encourage practical application. Regular refresher training ensures that employees remain updated on best practices and emerging risks. Effective training fosters a risk-aware culture, where employees are empowered to identify and report potential problems, contributing to a more resilient organization.
Risk Management for Business Continuity and Resilience
Risk management is crucial for building business continuity and resilience. By systematically identifying and assessing potential disruptions – such as natural disasters, cyberattacks, or supply chain issues – businesses can develop robust contingency plans. These plans might involve establishing backup systems, diversifying suppliers, or implementing robust data security protocols. Regular business continuity drills and exercises help test the effectiveness of these plans and identify areas for improvement. For instance, a company facing the risk of a power outage might invest in backup generators and develop a communication plan to ensure employees can continue working remotely. This proactive approach, driven by a comprehensive risk management framework, ensures business operations can withstand unforeseen disruptions and recover quickly, minimizing financial losses and reputational damage.
Technological Aspects of Risk Management

Technology has fundamentally reshaped risk management, offering sophisticated tools and techniques to identify, assess, and respond to a wider range of risks more efficiently and effectively than ever before. Its impact spans all aspects of risk management, from initial identification through to ongoing monitoring and control. This section will explore the key roles technology plays in modern risk management practices.
Technology’s Role in Risk Identification, Assessment, and Response
Technology significantly enhances the speed and accuracy of risk identification. Automated data collection from various sources, including internal systems and external databases, allows for a more comprehensive view of potential threats. Sophisticated algorithms can analyze vast datasets to identify patterns and anomalies indicative of emerging risks that might otherwise go unnoticed. In assessment, technology provides quantitative models and simulations to evaluate the likelihood and impact of identified risks, leading to more informed decision-making. For response, technology facilitates the development and implementation of mitigation strategies, enabling proactive and reactive measures to be deployed rapidly and effectively. For example, real-time monitoring systems can automatically trigger alerts and responses to critical events, minimizing damage and disruption.
Examples of Risk Management Software and Tools
Several software solutions and tools are specifically designed to support risk management processes. These range from simple spreadsheet-based systems for smaller organizations to complex enterprise risk management (ERM) platforms for larger corporations. Examples include Archer (from RSA), MetricStream, and SAP GRC. These platforms typically offer features such as risk registers, scenario planning tools, key risk indicator (KRI) dashboards, and reporting functionalities. They often integrate with other enterprise systems to streamline data collection and analysis. Furthermore, specialized software exists for specific risk types, such as cybersecurity risk management platforms that monitor network activity and identify vulnerabilities.
Data Analytics and Machine Learning in Risk Management
Data analytics and machine learning (ML) are transforming risk management by enabling more predictive and proactive approaches. Data analytics allows for the identification of trends and patterns in risk data, providing insights into the drivers of risk and enabling more accurate risk assessments. ML algorithms can be trained on historical risk data to predict future risks, allowing organizations to anticipate and mitigate potential threats before they materialize. For instance, ML models can be used to predict the likelihood of fraud, identify potential supply chain disruptions, or assess the creditworthiness of borrowers. The application of these technologies significantly improves the accuracy and efficiency of risk management processes.
Security Risks Associated with Technology in Risk Management
While technology enhances risk management, it also introduces its own security risks. Data breaches, system failures, and cyberattacks can compromise sensitive risk information and disrupt risk management processes. Therefore, robust cybersecurity measures are crucial to protect risk management systems and data. This includes implementing strong access controls, regularly updating software and systems, conducting security audits, and employing encryption techniques to protect sensitive data. Failure to address these security risks can negate the benefits of technology and expose organizations to significant vulnerabilities.
Communication and Reporting of Risk
Effective communication and reporting of risk information are crucial for successful risk management. Stakeholders at all levels need to understand the organization’s risk profile, potential impacts, and the mitigation strategies in place. Clear, concise, and timely communication fosters informed decision-making and promotes a proactive risk culture.
Effective methods for communicating risk information to various stakeholders depend on their roles and needs. Tailoring the message to the audience ensures that the information is understood and acted upon. Visual aids are especially helpful in conveying complex information in a digestible format. Regular reporting mechanisms ensure that risks are consistently monitored and addressed.
Methods for Communicating Risk Information
Communicating risk information effectively involves selecting the right channel and format for each stakeholder group. For instance, executive summaries and high-level dashboards are suitable for the board of directors, while more detailed reports and training materials are appropriate for employees. Regular meetings, email updates, and intranet portals can be used to disseminate information consistently. Interactive tools and simulations can also enhance engagement and understanding, especially for complex risks.
Importance of Clear and Concise Risk Reporting
Clear and concise risk reporting is paramount for efficient risk management. Ambiguity can lead to misinterpretations, delayed responses, and ultimately, increased risk exposure. Reports should be structured logically, using plain language, and avoiding technical jargon where possible. Focusing on key findings, recommendations, and next steps helps stakeholders quickly grasp the essential information. Consistent reporting formats across different risk types and time periods also aid in comparative analysis and trend identification. A concise report minimizes wasted time and improves decision-making.
Sample Risk Report Template
A risk report template should be adaptable to different audiences. For the board of directors, a concise executive summary highlighting key risks, their potential impact, and proposed mitigation strategies would be appropriate. This summary could include a high-level risk register with key metrics, such as risk probability and impact scores. For employees, a more detailed report explaining specific risks relevant to their roles, along with clear action plans and responsibilities, would be more effective. A template might include sections for risk identification, assessment, response, and monitoring.
Visual Aids for Communicating Complex Risk Information
Visual aids significantly improve the understanding and retention of complex risk information. A heat map, for example, can effectively illustrate the probability and impact of various risks using a color-coded matrix. A bar chart could compare the frequency of different risk events over time, while a pie chart could show the proportion of risks across different categories. Network diagrams can depict the interconnectedness of risks, illustrating how one risk event might trigger others. A Gantt chart could illustrate the timeline for implementing risk mitigation strategies. These visual tools offer a quick and accessible way to understand complex information.
Last Word
Successfully navigating the landscape of risk requires a proactive, multi-faceted approach. By understanding the core principles, employing appropriate methodologies, and leveraging available technologies, organizations can significantly reduce their vulnerability and enhance their resilience. This guide has provided a framework for building a robust risk management system, but remember that continuous monitoring, adaptation, and a commitment to learning are essential for long-term success. Embrace the challenge, and transform risk management from a reactive burden into a strategic advantage.
FAQ Guide
What is the difference between qualitative and quantitative risk assessment?
Qualitative assessment uses descriptive terms (e.g., high, medium, low) to evaluate likelihood and impact, while quantitative assessment uses numerical data and statistical methods for a more precise evaluation.
How often should risk monitoring be performed?
The frequency of risk monitoring depends on the nature and severity of the risks involved. Regular reviews (e.g., monthly, quarterly) are generally recommended, with more frequent checks for high-priority risks.
What are Key Risk Indicators (KRIs)?
KRIs are metrics that provide early warning signals of potential problems. They are used to track the effectiveness of risk responses and to identify emerging threats.
What is the role of a Risk Manager?
A Risk Manager is responsible for developing and implementing the organization’s risk management strategy. They identify, assess, and mitigate risks, and ensure that appropriate controls are in place.