Navigating the complexities of modern business requires a proactive approach to risk. This Risk Management Strategies Guide provides a comprehensive framework for identifying, assessing, and mitigating potential threats. From understanding various risk types to implementing effective response strategies and leveraging key performance indicators (KPIs), this guide equips organizations with the tools and knowledge to build resilience and achieve sustainable success. We explore both qualitative and quantitative methods, showcasing real-world examples and case studies to illustrate best practices and the pitfalls of inadequate risk management.
The guide delves into the development of a robust risk management plan, emphasizing the crucial roles of communication and collaboration. We examine established frameworks such as ISO 31000, offering practical guidance on their implementation across diverse industries. Ultimately, this resource aims to empower decision-makers with the confidence to proactively manage risks and seize opportunities for growth.
Introduction to Risk Management

Risk management is the process of identifying, assessing, and controlling threats to an organization’s capital and earnings. It’s a proactive approach to minimizing potential losses and maximizing opportunities. Effective risk management is crucial for ensuring the long-term sustainability and success of any organization, regardless of size or industry.
Implementing effective risk management strategies offers numerous benefits. It enhances an organization’s resilience by preparing it to withstand unforeseen events. This preparedness can lead to improved decision-making, reduced losses, increased profitability, and a stronger reputation. Furthermore, proactive risk management can improve operational efficiency by identifying and addressing potential bottlenecks before they become critical issues. A robust risk management framework can also enhance compliance with regulatory requirements and improve stakeholder confidence.
Types of Risks Faced by Organizations
Organizations face a wide range of risks that can impact their operations and financial performance. Categorizing these risks helps in developing targeted mitigation strategies. The following table Artikels some common risk types:
| Risk Type | Description | Examples |
|---|---|---|
| Financial Risk | Risks related to the financial stability and performance of the organization. | Credit risk (failure of borrowers to repay loans), market risk (fluctuations in market prices), liquidity risk (inability to meet short-term obligations). |
| Operational Risk | Risks related to internal processes, people, systems, or external events. | System failures, human error, supply chain disruptions, natural disasters. For example, a power outage could halt production and lead to significant financial losses. |
| Strategic Risk | Risks related to the achievement of an organization’s strategic objectives. | Changes in market demand, competitive pressures, regulatory changes, failure to innovate. A company failing to adapt to a shift in consumer preferences could experience declining market share. |
| Compliance Risk | Risks related to non-compliance with laws, regulations, and internal policies. | Failure to meet environmental regulations, data breaches leading to fines, violation of anti-trust laws. For example, a company failing to comply with data privacy regulations could face substantial penalties. |
Risk Identification and Assessment
Effective risk management begins with a thorough understanding of potential threats. This section Artikels methods for identifying and assessing risks within an organization, providing a framework for proactive mitigation strategies. A comprehensive approach ensures that all potential vulnerabilities are addressed, minimizing the likelihood and impact of negative events.
Methods for Identifying Potential Risks
Identifying potential risks requires a multi-faceted approach. Several methods can be employed to ensure a comprehensive overview of potential threats. These include brainstorming sessions involving various departments, reviewing past incidents and near misses, analyzing industry trends and best practices, conducting risk assessments using checklists and questionnaires, and utilizing external resources such as regulatory guidelines and industry reports. Each method offers a unique perspective, contributing to a more complete picture of potential risks. For example, reviewing past incidents highlights recurring vulnerabilities, while analyzing industry trends allows for proactive identification of emerging threats.
Risk Assessment Techniques
Once potential risks have been identified, they need to be assessed to determine their likelihood and potential impact. Two primary techniques are used: qualitative and quantitative risk assessment. Qualitative assessment uses descriptive terms (e.g., low, medium, high) to categorize likelihood and impact, often relying on expert judgment. Quantitative assessment utilizes numerical data and statistical methods to assign probabilities and financial consequences to risks. For instance, a quantitative assessment might estimate the financial loss associated with a data breach based on historical data and industry benchmarks. The choice of technique depends on the complexity of the risk and the availability of data. Many organizations use a combination of both methods for a more robust assessment.
Risk Register Template
A risk register is a crucial tool for tracking and managing identified risks. The following HTML table provides a template for recording key information about each risk. This template allows for easy monitoring and prioritization of risks based on their likelihood and impact. Regular updates to the register ensure the information remains current and relevant.
| Risk Description | Likelihood | Impact | Mitigation Strategy |
|---|---|---|---|
| Data breach due to insufficient cybersecurity measures | Medium | High (financial loss, reputational damage) | Implement multi-factor authentication, employee training, and regular security audits. |
| Supply chain disruption due to geopolitical instability | Low | Medium (production delays, increased costs) | Diversify suppliers, build buffer stock, and develop contingency plans. |
| Loss of key personnel due to lack of succession planning | Medium | High (loss of expertise, project delays) | Implement a robust succession planning program, cross-training, and knowledge management system. |
| Regulatory changes impacting operations | High | High (fines, operational disruptions) | Establish a regulatory compliance program, monitor legislative changes, and engage with regulatory bodies. |
Risk Response Strategies
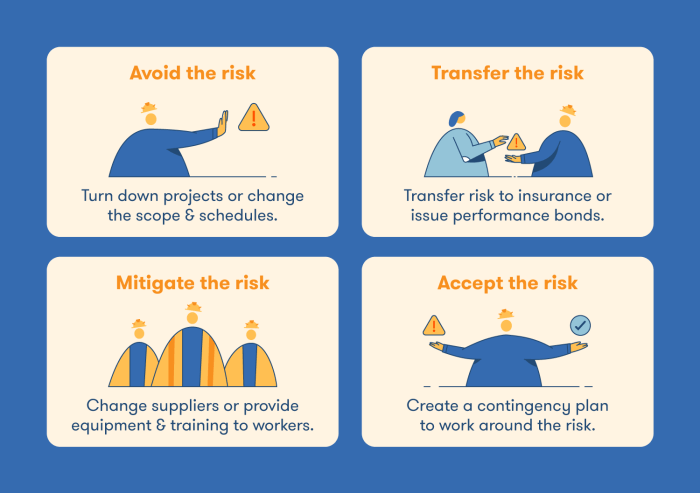
Once risks have been identified and assessed, the next crucial step is developing and implementing appropriate response strategies. Effective risk response planning involves choosing the best approach to each identified risk, considering its likelihood, impact, and the organization’s risk appetite. This involves a careful balancing act between minimizing potential negative impacts and maximizing opportunities.
Common Risk Response Strategies
Four primary strategies are commonly employed to address identified risks: avoidance, mitigation, transfer, and acceptance. The selection of the most suitable strategy depends heavily on the specific nature of the risk, its potential consequences, and the resources available to the organization. Each strategy offers a different approach to managing risk and comes with its own set of advantages and disadvantages.
Risk Avoidance
Risk avoidance involves proactively eliminating the risk altogether by ceasing the activity or process that generates it. This is the most straightforward strategy, but it’s not always feasible or desirable. It’s most effective for high-impact, high-likelihood risks where the potential negative consequences significantly outweigh the benefits.
- Example 1: A construction company decides not to undertake a project in a politically unstable region due to high security risks and potential for project delays or cancellation.
- Example 2: A bank chooses not to offer a new type of high-risk loan product to avoid potential losses from defaults.
Risk Mitigation
Risk mitigation focuses on reducing the likelihood or impact of a risk event. This strategy involves implementing controls to lessen the severity of potential consequences if the risk does occur. Mitigation is often the preferred strategy when avoidance isn’t possible or practical.
- Example 1: Implementing fire suppression systems and regular fire drills to reduce the impact of a fire in an office building.
- Example 2: Developing a robust cybersecurity program, including regular security audits and employee training, to mitigate the risk of data breaches.
Risk Transfer
Risk transfer involves shifting the burden of risk to a third party. This is typically achieved through insurance, outsourcing, or contracts. This strategy is effective for risks that are difficult or expensive to mitigate, but it doesn’t eliminate the risk entirely; it simply transfers the financial consequences.
- Example 1: Purchasing insurance to cover potential losses from property damage due to natural disasters.
- Example 2: Outsourcing IT infrastructure management to a third-party provider to reduce the risk associated with maintaining and securing complex systems.
Risk Acceptance
Risk acceptance involves acknowledging the risk and deciding to accept the potential consequences. This is often the case for low-impact, low-likelihood risks where the cost of mitigation outweighs the potential benefits. However, acceptance should be a conscious decision, not an oversight. Monitoring accepted risks is crucial.
- Example 1: A small business accepts the risk of minor fluctuations in customer demand, recognizing that the cost of implementing strategies to mitigate these fluctuations is too high.
- Example 2: A company accepts a small risk of equipment malfunction, understanding that the probability of failure is low and the impact is minimal.
Comparing Risk Response Strategies
The effectiveness of each risk response strategy varies depending on the specific circumstances. Avoidance is best for high-impact, high-likelihood risks, while mitigation is suitable for risks that can be reduced through controls. Transfer is useful for risks that are difficult to mitigate, and acceptance is appropriate for low-impact, low-likelihood risks. A combination of strategies is often the most effective approach to managing a portfolio of risks. For example, a company might mitigate some risks, transfer others, and accept the remaining low-impact risks.
Risk Monitoring and Control
Effective risk monitoring and control is crucial for ensuring that the implemented risk management strategies remain relevant and effective over time. This involves continuously tracking identified risks, measuring their impact, and adapting strategies as circumstances change. Proactive monitoring allows for early detection of emerging risks and prevents minor issues from escalating into major problems.
The process involves establishing key risk indicators (KRIs), regularly monitoring these indicators, and making necessary adjustments to risk response strategies based on the observed data. This iterative process ensures the organization maintains a robust and adaptable risk management framework.
Establishing Key Risk Indicators (KRIs)
Key Risk Indicators (KRIs) are quantifiable measures used to monitor the likelihood and potential impact of identified risks. They provide early warning signals of potential problems, allowing for timely intervention. KRIs should be specific, measurable, achievable, relevant, and time-bound (SMART). For example, a KRI for a project might be the number of unresolved critical issues, while for a financial institution, it could be the ratio of non-performing loans to total loans. Effective KRIs provide a clear picture of the current risk profile and help in prioritizing risk response activities.
Monitoring and Tracking Identified Risks and KRIs
Monitoring involves the regular collection and analysis of data related to identified risks and their associated KRIs. This can be achieved through various methods, including regular reporting, dashboards, and automated monitoring systems. Data analysis techniques, such as trend analysis and variance analysis, help identify patterns and deviations from expected levels. For instance, a company might track its KRI for customer churn monthly, comparing it to the target churn rate and investigating any significant deviations. Regular reviews and updates of the risk register are crucial for ensuring that the monitoring process is effective and that the information remains current and accurate.
Adjusting Risk Management Strategies Based on Monitoring Results
The results of risk monitoring inform the decision-making process regarding adjustments to risk management strategies. If KRIs indicate a significant increase in risk, corrective actions may be necessary. This could involve implementing new controls, modifying existing strategies, or allocating additional resources. Conversely, if KRIs indicate a decrease in risk, the organization may be able to reduce its efforts or resources allocated to managing that specific risk. For example, if a project’s KRI for schedule slippage consistently exceeds expectations, the project manager might need to adjust the project plan, add resources, or re-evaluate the project scope. Continuous monitoring and adjustment ensure the risk management framework remains effective and adaptive.
Risk Monitoring and Control Methods
| Method | Description | Example | Benefits |
|---|---|---|---|
| Regular Reporting | Periodic reports summarizing the status of risks and KRIs. | Monthly reports on project delays and budget overruns. | Provides a structured overview of risk status. |
| Dashboards | Visual representations of key risk data, enabling quick identification of trends and issues. | A dashboard showing the real-time status of various KRIs, such as customer satisfaction, sales performance, and operational efficiency. | Provides immediate insights into risk levels. |
| Automated Monitoring Systems | Automated systems that continuously track risk-related data and trigger alerts when thresholds are breached. | A system that automatically alerts the IT department when a server’s CPU usage exceeds a predefined threshold. | Provides real-time alerts and reduces manual effort. |
| Risk Audits | Periodic reviews of the effectiveness of the risk management process and its controls. | An annual audit of the organization’s cybersecurity controls. | Ensures the ongoing effectiveness of the risk management framework. |
Developing a Risk Management Plan
A comprehensive risk management plan is the cornerstone of effective risk mitigation. It translates identified risks and chosen responses into actionable steps, ensuring consistent management and proactive adaptation to changing circumstances. A well-structured plan provides a framework for communication, accountability, and continuous improvement within the organization.
Step-by-Step Guide to Developing a Risk Management Plan
Creating a robust risk management plan requires a structured approach. This process should be iterative, allowing for adjustments based on new information and changing contexts. The following steps provide a clear path to developing a comprehensive and effective plan.
- Define Scope and Objectives: Clearly define the project, process, or organization the plan covers. Specify the goals and objectives the plan aims to protect. For example, a software development project’s plan might aim to minimize delays and cost overruns while ensuring product quality.
- Identify Stakeholders: Determine all individuals or groups affected by the risks and the plan’s implementation. This includes project managers, developers, clients, and even end-users. Their input is crucial for a comprehensive risk assessment.
- Risk Identification and Assessment: This involves systematically identifying potential risks using techniques like brainstorming, checklists, SWOT analysis, and HAZOP (Hazard and Operability) studies. For each risk, assess its likelihood and potential impact. A risk matrix, often visualized as a table, can effectively represent this information.
- Risk Response Planning: Develop strategies to address each identified risk. This might involve risk avoidance, mitigation, transference (e.g., insurance), or acceptance. For each strategy, detail the actions required, responsibilities, and timelines.
- Resource Allocation: Allocate the necessary resources (budget, personnel, time) to implement the chosen risk response strategies. This step ensures that the plan is feasible and achievable.
- Plan Documentation and Communication: Document the entire risk management plan comprehensively, including all identified risks, assessments, responses, and resource allocation. Communicate the plan clearly to all stakeholders, ensuring everyone understands their roles and responsibilities.
- Plan Implementation and Monitoring: Implement the plan according to the defined schedule and monitor its effectiveness regularly. This includes tracking progress, identifying any deviations from the plan, and making necessary adjustments.
- Review and Update: Regularly review and update the risk management plan to reflect changes in the environment, project status, or new information. This ensures the plan remains relevant and effective throughout its lifecycle.
The Importance of Communication and Collaboration in Risk Management
Effective communication and collaboration are paramount to successful risk management. Open communication ensures that all stakeholders are informed about potential risks and the strategies to address them. Collaboration fosters a shared understanding and commitment to risk mitigation. A lack of communication can lead to misunderstandings, missed opportunities, and ultimately, failure to manage risks effectively. Regular meetings, progress reports, and readily accessible documentation are essential tools for maintaining effective communication and collaboration.
Sample Risk Management Plan
This sample plan Artikels the key components for a hypothetical software development project.
| Risk | Likelihood | Impact | Response Strategy | Responsible Party | Timeline | Resources |
|---|---|---|---|---|---|---|
| Project Delays | High | High | Mitigation (Implement Agile methodology) | Project Manager | Throughout Project | Dedicated team, Agile tools |
| Budget Overruns | Medium | Medium | Mitigation (Detailed budgeting, regular monitoring) | Finance Manager | Monthly | Budgeting software, regular reports |
| Security Breach | Low | High | Transfer (Cybersecurity insurance) | IT Manager | Project Initiation | Insurance policy |
| Staff Turnover | Medium | Medium | Mitigation (Competitive salaries, professional development) | HR Manager | Ongoing | Training budget, competitive compensation |
Risk Management Frameworks and Standards
Effective risk management relies on a structured approach, and various frameworks provide the necessary guidance. These frameworks offer a common language and methodology, enabling organizations to consistently identify, assess, and respond to risks. Choosing the right framework depends on factors such as industry, organizational size, and risk appetite.
Several prominent frameworks exist, each with its strengths and weaknesses. Understanding their key features allows organizations to select and adapt the most suitable framework for their needs. This section explores some of the most widely used frameworks and illustrates their application across diverse industries.
ISO 31000: Risk Management Principles and Guidelines
ISO 31000 provides a widely accepted international standard for risk management. It emphasizes a holistic, integrated approach, applicable across all types of organizations and contexts. The standard focuses on principles rather than prescriptive methods, allowing flexibility in implementation. Key features include a focus on creating value, integrating risk management into decision-making, and continually improving the risk management process.
COSO ERM Framework
The Committee of Sponsoring Organizations of the Treadway Commission (COSO) Enterprise Risk Management (ERM) framework is a widely recognized framework, particularly in the corporate governance arena. It offers a more comprehensive approach than ISO 31000, encompassing strategic objectives and incorporating a wider range of risk types. COSO ERM emphasizes the importance of aligning risk appetite with strategic objectives and provides a detailed structure for risk assessment and response.
Comparison of ISO 31000 and COSO ERM
While both frameworks aim to improve risk management, they differ in scope and approach. ISO 31000 is more principles-based, offering flexibility in implementation, while COSO ERM is more prescriptive, providing a detailed structure for risk management activities. ISO 31000 focuses on a broader range of risks, whereas COSO ERM is particularly suited to aligning risk management with strategic objectives. The choice between them depends on the specific needs and context of the organization.
| Feature | ISO 31000 | COSO ERM |
|---|---|---|
| Scope | Broad, applicable to any organization or context | Primarily focused on enterprise-level risk management within organizations |
| Approach | Principles-based, flexible implementation | More prescriptive, detailed structure and components |
| Focus | Creating value, integrating risk management into decision-making | Aligning risk appetite with strategic objectives, comprehensive risk assessment and response |
Applications of Risk Management Frameworks Across Industries
The application of these frameworks varies across industries, reflecting the unique risk profiles of each sector. However, the underlying principles remain consistent.
- Healthcare: ISO 31000 can be used to manage risks related to patient safety, data privacy, and regulatory compliance. COSO ERM can help healthcare providers align risk management with strategic goals, such as improving patient outcomes and reducing costs.
- Finance: Both frameworks are crucial in the financial services industry, helping institutions manage risks associated with market volatility, credit defaults, and operational failures. COSO ERM’s emphasis on strategic alignment is particularly relevant for financial institutions.
- Manufacturing: ISO 31000 can be applied to manage operational risks, such as supply chain disruptions and product recalls. COSO ERM can help manufacturing companies align risk management with their strategic objectives, such as increasing efficiency and improving product quality.
- Technology: In the technology sector, both frameworks can help manage risks related to cybersecurity threats, data breaches, and software failures. The frameworks assist in establishing robust security protocols and incident response plans.
Case Studies in Risk Management
This section presents two case studies illustrating both successful and unsuccessful risk management implementations. Examining these real-world examples provides valuable insights into effective strategies and the potential consequences of neglecting risk management. Understanding these contrasting scenarios allows for a more nuanced appreciation of the importance of proactive and comprehensive risk management practices.
Successful Risk Management: The Boeing 787 Dreamliner Program
The Boeing 787 Dreamliner program, while initially plagued by delays and cost overruns, ultimately serves as a case study in adaptive risk management. Early in development, Boeing faced significant challenges, including supply chain disruptions, technological complexities related to the extensive use of composite materials, and integration issues with new systems. These risks were identified through rigorous risk assessments, involving extensive simulations and testing, and stakeholder consultations. Boeing employed several key strategies: a phased rollout approach, allowing for incremental learning and adaptation; strong supplier collaboration to mitigate supply chain risks; and a proactive communication strategy to manage stakeholder expectations. The program experienced significant delays, but through continuous monitoring, adaptation, and a commitment to addressing identified risks, Boeing ultimately delivered the 787, demonstrating the importance of flexible and responsive risk management.
Key Learning: Successful risk management is not about eliminating all risks, but about proactively identifying, assessing, and mitigating them, adapting strategies as new information emerges. A flexible and iterative approach, coupled with open communication and collaboration, is crucial.
Unsuccessful Risk Management: The Deepwater Horizon Oil Spill
The Deepwater Horizon oil spill in 2010 serves as a stark example of the devastating consequences of inadequate risk management. Several factors contributed to the disaster, including cost-cutting measures that compromised safety protocols, inadequate risk assessments that underestimated the potential for catastrophic failure, and a lack of effective communication and coordination among involved parties. The failure to adequately address the risks associated with deep-water drilling, including the potential for wellbore instability and blowout, led to a catastrophic event with devastating environmental and economic consequences. The investigation revealed a culture of complacency and a failure to prioritize safety over cost and schedule pressures. This resulted in insufficient safety checks and a lack of preparedness for a major incident.
Key Learning: Neglecting risk management can lead to catastrophic consequences. A culture of safety and a commitment to thorough risk assessment, coupled with robust emergency response planning, are paramount. Cost-cutting measures should never compromise safety, and effective communication and collaboration across all stakeholders are essential.
Tools and Techniques for Risk Management
Effective risk management relies heavily on the application of appropriate tools and techniques. Choosing the right tools depends on the nature of the risks, the organization’s resources, and the desired level of detail in the analysis. This section explores both qualitative and quantitative approaches, along with commonly used software solutions.
Qualitative Risk Analysis Techniques
Qualitative risk analysis employs subjective judgment and expert opinion to assess risks. This approach is particularly useful when dealing with uncertainties or a lack of historical data. One prominent technique is SWOT analysis.
SWOT Analysis
SWOT analysis is a strategic planning technique used to identify Strengths, Weaknesses, Opportunities, and Threats related to a project or organization. Strengths and weaknesses are internal factors, while opportunities and threats are external. By mapping these factors, organizations can identify potential risks and develop strategies to mitigate them. For example, a new product launch (project) might have a strong brand reputation (strength) but lack sufficient market research (weakness). A competitor’s new product (threat) could present an opportunity to innovate and improve. This analysis helps prioritize risks based on their potential impact.
Quantitative Risk Analysis Techniques
Quantitative risk analysis uses numerical data and statistical methods to assess the likelihood and impact of risks. This approach provides a more precise and objective assessment compared to qualitative methods. Probability and impact matrices are frequently used.
Probability and Impact Matrices
Probability and impact matrices visually represent the likelihood and potential consequences of identified risks. Risks are plotted on a matrix with likelihood on one axis (e.g., low, medium, high) and impact on the other (e.g., low, medium, high). This allows for a clear visualization of the relative importance of different risks. A risk with high likelihood and high impact would be prioritized for mitigation. For example, a risk of a major system failure might have a medium likelihood but a very high impact, requiring significant attention.
Software Tools for Risk Management
Several software tools are available to assist in risk management processes. These tools often automate tasks, enhance collaboration, and provide comprehensive reporting capabilities.
- Microsoft Project: While primarily a project management tool, Microsoft Project offers features for risk management, including the ability to track risks, assign owners, and monitor progress on mitigation strategies.
- Risk Management Pro: This specialized software provides a comprehensive suite of tools for risk identification, analysis, response planning, and monitoring.
- Jira: Commonly used for agile project management, Jira can be configured to track and manage risks through custom workflows and issue tracking.
- Oracle Primavera Risk Analysis: This software uses Monte Carlo simulation to analyze risks and their potential impact on project schedules and budgets.
Final Review
Effective risk management is not merely a compliance exercise; it’s a strategic imperative for organizational success. This guide has provided a roadmap for building a resilient and adaptable organization capable of navigating uncertainty and achieving its objectives. By implementing the strategies Artikeld herein, organizations can transform potential threats into opportunities, fostering a culture of proactive risk management and sustainable growth. Remember, consistent monitoring, adaptation, and continuous improvement are key to maintaining a robust risk management framework.
FAQ Insights
What is the difference between qualitative and quantitative risk analysis?
Qualitative risk analysis uses subjective judgment and descriptive scales to assess risks (e.g., high, medium, low). Quantitative risk analysis uses numerical data and statistical methods to assign probabilities and potential impacts to risks.
How often should a risk management plan be reviewed and updated?
Risk management plans should be reviewed and updated regularly, at least annually, or more frequently if significant changes occur within the organization or its environment.
What are some common software tools used for risk management?
Popular software options include dedicated risk management platforms, project management software with risk management modules, and spreadsheet software for simpler risk registers.
How can I ensure buy-in from all stakeholders for a risk management plan?
Effective communication, clear demonstration of value, and collaborative plan development involving key stakeholders are crucial for securing buy-in.