Risk Management Strategies Guide: Embark on a thrilling journey through the unpredictable world of risk! Think of it as a daring expedition, where instead of battling wild beasts, we conquer unforeseen challenges. This guide equips you with the map, compass, and survival kit (strategies, of course) to navigate the treacherous terrain of potential pitfalls and emerge victorious, possibly with a slightly bruised ego but significantly richer in experience. Prepare for a witty, yet insightful exploration of risk management, where even the most daunting risks become manageable adventures.
This guide delves into the core principles of risk management, from identifying potential threats – be they financial fiascos or operational oddities – to developing robust strategies for mitigation. We’ll explore various techniques, from the classic SWOT analysis to the more statistically sophisticated Monte Carlo simulation, all while maintaining a healthy dose of humor to keep things engaging. Get ready to transform your approach to risk from one of fear to one of calculated strategic prowess.
Introduction to Risk Management
Risk management, in its simplest form, is the art of anticipating trouble before it becomes a full-blown circus – a proactive approach to identifying, analyzing, and mitigating potential problems before they derail your carefully laid plans (and possibly your sanity). Think of it as insurance for your ambitions, but instead of paying premiums, you invest time and strategy.
Proactive risk management strategies are crucial because they transform potential disasters into manageable bumps in the road. By identifying risks early, you can develop effective countermeasures, saving you time, money, and the agonizing feeling of watching your carefully constructed castle crumble into dust. It’s like having a highly skilled (and caffeinated) ninja team constantly scanning the horizon for threats, ready to spring into action before things get out of hand.
Neglecting risk management is akin to sailing a ship without a map or compass, relying solely on the whims of the wind and hoping for the best. The potential consequences range from minor inconveniences to catastrophic failures. Think lost revenue, damaged reputation, legal battles, and even complete business collapse. Essentially, it’s a recipe for disaster, served with a side of regret.
Types of Risks
Various types of risks can threaten an organization’s success. Understanding these different categories allows for targeted mitigation strategies. A well-rounded risk management plan addresses all potential threats, not just the obvious ones. It’s like having a comprehensive first-aid kit – you hope you never need the advanced stuff, but it’s comforting to know it’s there.
| Financial Risk | Operational Risk | Strategic Risk | Compliance Risk |
|---|---|---|---|
| Unexpected changes in interest rates impacting loan repayments. For example, a sudden spike in interest rates could significantly increase the cost of borrowing for a small business, threatening its financial stability. | Equipment malfunction leading to production delays. Imagine a factory’s main assembly line suddenly breaking down, causing significant delays in production and potentially leading to missed deadlines and lost orders. | Failure to adapt to changing market trends. A company that stubbornly sticks to outdated products or services while competitors innovate could lose market share and eventually fail, as seen with many companies that didn’t adapt to the rise of the internet. | Non-compliance with environmental regulations leading to hefty fines. A manufacturing company that fails to adhere to environmental regulations could face substantial fines and legal repercussions, significantly impacting its profitability and reputation. |
| Investment losses due to market volatility. The bursting of the dot-com bubble in the early 2000s wiped out billions in investments, highlighting the inherent volatility of the stock market. | Supply chain disruptions due to natural disasters. The 2011 Tohoku earthquake and tsunami in Japan caused significant disruptions to global supply chains, highlighting the vulnerability of businesses to unforeseen events. | Entering a new market without sufficient market research. A company launching a product in a new market without proper research might face unexpected competition and low demand, leading to significant losses. | Data breaches leading to legal action and reputational damage. The Equifax data breach in 2017 resulted in significant financial losses and reputational damage for the company, illustrating the severe consequences of data breaches. |
Risk Identification and Assessment
Identifying and assessing risks is like a thrilling treasure hunt, except the treasure is avoiding catastrophic failure, and the map is… well, let’s just say it’s a work in progress. This crucial stage sets the stage for effective risk management, ensuring we don’t accidentally stumble into a pit of vipers (metaphorically speaking, of course. We hope).
Methods for Identifying Potential Risks
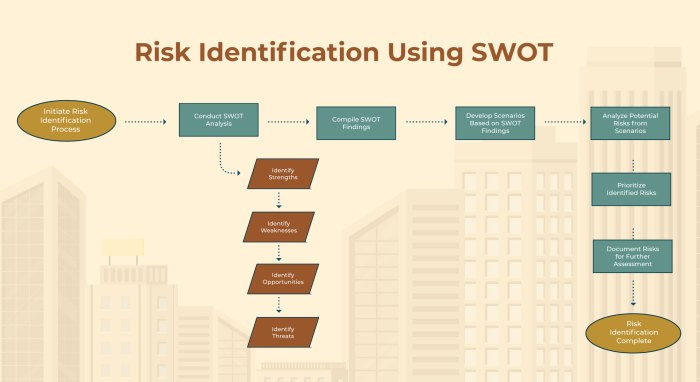
Identifying potential risks requires a multifaceted approach, blending structured methodologies with a healthy dose of creative brainstorming. Ignoring the obvious risks is like ignoring the giant, hissing cobra in the corner – it’s rarely a good idea. Effective risk identification leverages various techniques to uncover both the predictable and the delightfully unexpected. For instance, SWOT analysis (Strengths, Weaknesses, Opportunities, Threats) helps systematically examine internal and external factors influencing the project. Brainstorming sessions, facilitated by experienced risk managers, encourage open discussion and the identification of risks that might otherwise be overlooked. Checklists, tailored to specific industries or project types, provide a structured framework for capturing common risks. Finally, interviews with stakeholders across the organization provide valuable insights into potential problems and vulnerabilities.
Risk Assessment Process: Likelihood and Impact
Assessing the likelihood and impact of identified risks is akin to assigning a danger level to each potential pitfall on our treasure hunt. We need a systematic process to ensure we prioritize the most threatening risks. This process typically involves: (1) Defining criteria for assessing likelihood (e.g., using a scale from “unlikely” to “almost certain”) and impact (e.g., using a scale from “negligible” to “catastrophic”). (2) Assigning numerical scores or qualitative ratings to each risk based on the defined criteria. (3) Visualizing the risks using a matrix, often plotting likelihood against impact. This allows for quick identification of high-priority risks (high likelihood and high impact) that require immediate attention. (4) Documenting the assessment, including the methodology, assigned scores, and rationale. Consider a hypothetical software launch: A minor bug (low likelihood, low impact) might be addressed later, while a security vulnerability (high likelihood, high impact) demands immediate resolution.
Qualitative and Quantitative Risk Assessment Techniques
Qualitative and quantitative risk assessment techniques offer different perspectives on the same problem – like viewing a mountain range from both a bird’s-eye view and from the base camp. Qualitative assessments use subjective judgments and descriptive scales to assess likelihood and impact, making them ideal for early-stage projects or situations with limited data. For example, using a scale of “low,” “medium,” and “high” for both likelihood and impact. Quantitative assessments, conversely, utilize numerical data and statistical analysis to provide a more precise evaluation. This might involve calculating the probability of specific events occurring and their potential financial consequences, such as calculating the expected monetary value (EMV) of a risk using the formula:
EMV = (Probability of occurrence) * (Impact)
. The choice between qualitative and quantitative methods depends on the context, available data, and the project’s complexity.
Step-by-Step Risk Assessment Procedure
A well-structured risk assessment process is like a carefully planned expedition, minimizing surprises and maximizing the chances of success. Following a step-by-step procedure ensures thoroughness and consistency.
- Define the Scope: Clearly identify the project or activity to be assessed.
- Identify Risks: Use various methods (brainstorming, checklists, SWOT analysis) to identify potential risks.
- Analyze Risks: Determine the likelihood and impact of each identified risk.
- Prioritize Risks: Rank risks based on their likelihood and impact using a risk matrix.
- Develop Risk Responses: Create strategies to mitigate, transfer, avoid, or accept each risk.
- Document Findings: Maintain a comprehensive record of the entire risk assessment process.
- Monitor and Review: Regularly monitor and review the risk assessment, updating it as needed.
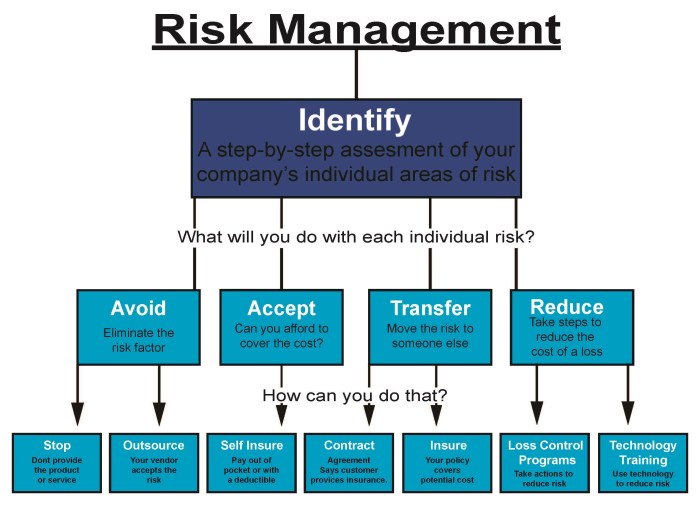
Risk Response Strategies
Now that we’ve identified and assessed those pesky risks (phew!), it’s time to get strategic about how we’re going to handle them. Think of this as the “risk-wrangling” phase – where we tame those wild beasts before they cause havoc in our perfectly planned project (or life!). We’ll explore the four main strategies, each with its own unique flavor and approach. Choosing the right one is key to avoiding a catastrophic tumble down the slippery slope of disaster.
Risk Avoidance
This strategy is all about sidestepping the risk entirely. If a risk is too big, too hairy, or simply too much of a headache, sometimes the best approach is to simply avoid it altogether. Imagine a project involving a notoriously unreliable supplier – avoiding that supplier altogether might be the wisest move, even if it means slightly higher costs elsewhere. This is particularly effective for risks with high impact and high likelihood. The key here is to carefully weigh the pros and cons; sometimes the avoidance strategy might lead to missed opportunities, but avoiding a potential catastrophe is often worth it.
Risk Mitigation
Mitigation is about reducing the likelihood or impact of a risk. It’s like putting a safety net under a tightrope walker – it doesn’t eliminate the risk of falling, but it significantly reduces the consequences. For example, if a risk is a potential software bug causing system downtime, mitigation strategies might include rigorous testing, implementing backup systems, and establishing a quick recovery plan. This strategy is perfect for risks where complete avoidance isn’t feasible or practical. The goal is to minimize the negative effects if the risk does materialize.
Risk Transference
Think of this as shifting the risk onto someone else’s shoulders. This often involves purchasing insurance, outsourcing a risky task, or using contractual agreements to transfer liability. For instance, a construction company might transfer the risk of potential worksite accidents to an insurance company through liability insurance. It’s a clever strategy, but remember, it usually comes with a cost – the insurance premium, for example. However, the cost of transferring the risk is often less than the potential cost of dealing with the risk directly.
Risk Acceptance
Sometimes, the best strategy is to simply accept the risk. This isn’t about being reckless; it’s about acknowledging that some risks are low-impact and the cost of mitigation outweighs the potential losses. For example, a small scratch on a company car might be deemed an acceptable risk, as the cost of repair is minimal compared to the cost of implementing preventative measures for all minor scratches. This strategy is often used for low-probability, low-impact risks where the resources required to mitigate are excessive.
Documenting Risk Responses
Proper documentation is crucial for tracking progress and ensuring accountability. A structured approach is key. Here’s how you might document a risk response:
- Risk ID: Unique identifier for the risk (e.g., RISK-001)
- Risk Description: Clear and concise description of the risk.
- Risk Owner: The individual responsible for managing the risk.
- Response Strategy: The chosen strategy (Avoidance, Mitigation, Transference, Acceptance).
- Response Actions: Specific steps taken to implement the chosen strategy.
- Timeline: Expected completion date for each action.
- Budget: Estimated cost associated with the response.
- Contingency Plan: Alternative actions if the primary response fails.
This structured approach ensures that all relevant information is captured and readily available, making risk management a less daunting, and potentially even enjoyable, process.
Risk Monitoring and Control
Risk management isn’t a “set it and forget it” kind of thing; it’s more like herding cats – chaotic, unpredictable, and requiring constant vigilance. Ongoing monitoring is crucial to ensure your carefully crafted risk mitigation strategies aren’t silently unraveling like a poorly knit sweater. Without consistent oversight, even the most brilliant plan can become a monument to good intentions gone awry.
Risk monitoring and control involves the systematic tracking and evaluation of identified risks, the effectiveness of responses, and the overall health of your risk management program. It’s like having a personal risk-detecting bloodhound, sniffing out potential problems before they morph into full-blown disasters. This proactive approach helps to keep your organization on track and prevents minor issues from escalating into major headaches.
Methods for Tracking Risk Response Strategy Effectiveness
Effective tracking requires a multi-pronged approach, combining qualitative and quantitative data. Regularly reviewing risk registers, conducting post-incident analyses (learning from near misses is as valuable as learning from full-blown catastrophes!), and implementing robust reporting mechanisms are all vital. Imagine your risk response strategies as a finely tuned engine; these tracking methods are the gauges and diagnostics that keep everything running smoothly. For example, if your strategy involved employee training to mitigate a cybersecurity risk, you’d track things like the number of employees completing the training, the time taken to complete it, and the number of subsequent security incidents. If incidents still occur, a review of the training’s effectiveness is warranted. Perhaps a refresher course or a different training approach is needed.
Key Performance Indicators (KPIs) for Measuring Risk Management Effectiveness
KPIs provide quantifiable metrics to assess the success of your risk management efforts. These aren’t just arbitrary numbers; they’re the vital signs of your organization’s risk health. Think of them as the metrics a doctor uses to gauge a patient’s well-being. Examples include the number of risks identified and mitigated, the cost of risk events (both actual and projected), and the frequency of near misses. A lower number of security breaches, a decrease in the average cost of resolving incidents, and a consistent reduction in near-misses are all strong indicators of an effective risk management program. However, don’t rely solely on numbers. Qualitative feedback from employees and stakeholders is also essential for a comprehensive picture.
Visual Representation of the Risk Monitoring and Control Process
Imagine a circular flowchart. The process begins at the “Risk Identification and Assessment” stage (represented by a box at the top). An arrow then points to the “Risk Response Planning” box (to the right). From there, another arrow leads to the “Risk Response Implementation” box (at the bottom). Next, an arrow points to the “Risk Monitoring and Control” box (on the left). Within this box, smaller sub-boxes depict key activities: “Regular Reporting,” “Performance Measurement (KPIs),” “Audits and Reviews,” and “Corrective Actions.” Arrows loop from the “Risk Monitoring and Control” box back to the “Risk Identification and Assessment” box, highlighting the iterative nature of the process. This continuous feedback loop ensures that the risk management program remains dynamic and adaptable to changing circumstances. The entire diagram emphasizes the cyclical and iterative nature of risk management; it’s a never-ending process of identification, assessment, response, monitoring, and readjustment.
Developing a Risk Management Plan

Crafting a robust risk management plan isn’t just about ticking boxes; it’s about building a fortress of preparedness against the inevitable slings and arrows of outrageous fortune (and slightly less outrageous, but still annoying, misfortunes). A well-structured plan provides a roadmap for navigating uncertainty, turning potential disasters into manageable bumps in the road. Think of it as your organization’s insurance policy, but instead of paying premiums, you invest time and effort in proactive strategies.
Key Components of a Comprehensive Risk Management Plan
A comprehensive risk management plan needs several key ingredients, much like a truly excellent cake requires flour, sugar, eggs, and a dash of rebellious spirit (optional, but recommended). These components work together to create a holistic approach to risk management. Missing even one can leave your plan vulnerable, like a cake without flour – a sad, flat pancake of a plan.
| Component | Description | Example | Importance |
|---|---|---|---|
| Risk Register | A centralized repository detailing identified risks, their likelihood, impact, and assigned owners. | A spreadsheet listing potential supply chain disruptions, their probability (e.g., 20% chance of a major delay), and the impact on production (e.g., $100,000 loss per week). | Provides a clear overview of all identified risks, facilitating effective prioritization and response. |
| Risk Response Strategies | Detailed plans for mitigating, transferring, avoiding, or accepting identified risks. | For supply chain risk, strategies could include diversifying suppliers, building buffer stock, or purchasing insurance. | Ensures proactive measures are in place to address potential risks. |
| Contingency Plans | Detailed procedures to follow if a risk event occurs. | A step-by-step guide on how to handle a major supply chain disruption, including communication protocols, alternative sourcing strategies, and customer notification procedures. | Minimizes disruption and ensures business continuity in the event of a risk event. |
| Monitoring and Review Process | Regular review and update mechanisms to ensure the plan remains relevant and effective. | Quarterly reviews of the risk register, including updates on risk likelihood and impact, and adjustments to response strategies as needed. | Ensures the plan adapts to changing circumstances and remains a dynamic, not static, document. |
Risk Management Plan Template
Here’s a template to get you started. Remember, this is a flexible framework; adapt it to your specific needs. Trying to force a square peg into a round hole (or a generic template onto a unique organization) rarely ends well.
| Risk | Likelihood | Impact | Response Strategy | Owner | Status |
|---|---|---|---|---|---|
| Cybersecurity Breach | Medium | High | Implement multi-factor authentication, employee training, and incident response plan. | IT Manager | In Progress |
| Regulatory Changes | Low | Medium | Monitor regulatory developments and adjust compliance procedures accordingly. | Compliance Officer | Ongoing |
| Reputational Damage | Medium | High | Proactive communication strategy, crisis management plan. | Communications Manager | Planned |
Tailoring a Risk Management Plan to Different Organizational Contexts
A risk management plan isn’t a one-size-fits-all solution. A small startup faces different risks than a multinational corporation. A non-profit has different priorities than a for-profit enterprise. The key is to identify the unique challenges and vulnerabilities of your specific organization. Consider factors such as industry, size, location, and organizational culture. For instance, a tech startup might prioritize cybersecurity risks, while a construction company might focus on workplace safety.
Examples of Successful Risk Management Plans
Successful risk management isn’t about avoiding all risks; it’s about being prepared for them. Consider how companies like Johnson & Johnson (handling product recalls), or Boeing (improving aircraft safety following accidents) have demonstrated robust risk management frameworks. Their responses, while painful at times, showcase the importance of proactive planning and effective crisis management. These aren’t perfect examples, but they illustrate the value of learning from mistakes and continuously improving risk management processes. These examples highlight the importance of transparent communication, swift action, and a commitment to learning from past experiences.
Communication and Collaboration in Risk Management
Effective communication and seamless collaboration are not just nice-to-haves in risk management; they’re the lifeblood of a successful program. Think of it like this: a perfectly crafted risk mitigation strategy is useless if nobody knows about it, or worse, if different teams are working at cross-purposes. Open communication and collaborative efforts ensure everyone is on the same page, working towards a common goal of minimizing potential disruptions and maximizing opportunities.
The Importance of Effective Communication in Risk Management
Effective communication is the cornerstone of a robust risk management program. Without it, even the most meticulously identified and assessed risks can easily spiral out of control. Clear, concise, and timely communication ensures that everyone involved understands the risks, their potential impact, and the strategies being implemented to address them. This includes sharing relevant information with all stakeholders, from senior management to front-line employees, ensuring everyone has the context they need to make informed decisions and contribute effectively. A lack of communication can lead to duplicated efforts, missed deadlines, and ultimately, a failure to adequately manage risks. Think of the chaos of a fire drill without clear instructions – that’s what ineffective communication in risk management can look like.
Strategies for Fostering Collaboration Among Stakeholders
Collaboration is key to successful risk management. It involves bringing together individuals from different departments and levels of the organization, each with their own unique perspectives and expertise. This requires establishing a collaborative culture where open communication and mutual respect are valued. Regular meetings, workshops, and training sessions can facilitate collaboration and provide a platform for sharing information and brainstorming solutions. Using collaborative software platforms, such as project management tools, can streamline workflows and improve communication among stakeholders. Imagine a team trying to build a house without architects, builders, and electricians talking to each other – a recipe for disaster! Effective collaboration avoids such architectural (and risk management) mishaps.
Methods for Reporting Risk Information to Management and Other Relevant Parties
Reporting risk information is crucial for keeping stakeholders informed and accountable. This involves creating clear and concise reports that summarize the identified risks, their potential impact, and the mitigation strategies being implemented. Regular reporting, through various channels such as email, dashboards, or formal presentations, ensures that management and other relevant parties are aware of the organization’s risk profile and the progress made in managing those risks. Different reporting methods should be tailored to the audience and the type of information being communicated. For instance, a high-level summary for senior management might differ significantly from a detailed technical report for a specialized team. Regular and transparent reporting ensures everyone stays informed and can proactively contribute to risk management efforts.
Key Communication Channels and Stakeholders in a Risk Management Program
Effective risk management relies on a well-defined communication structure. The following table Artikels key communication channels and stakeholders involved in a typical risk management program. Remember, a well-oiled communication machine is vital for preventing risk-related catastrophes.
| Stakeholder Group | Communication Channel | Frequency | Type of Information |
|---|---|---|---|
| Senior Management | Formal reports, presentations | Monthly, Quarterly | High-level risk summaries, key performance indicators (KPIs) |
| Risk Management Team | Project management software, email, meetings | Daily, Weekly | Risk assessments, mitigation plans, progress updates |
| Departmental Managers | Email, meetings, intranet | Weekly, Monthly | Department-specific risks, mitigation strategies |
| Employees | Intranet, training sessions, email | As needed | Risk awareness training, incident reporting procedures |
Risk Management Tools and Techniques
Navigating the treacherous waters of risk requires more than just a life vest (a well-defined risk management plan, naturally); you need a whole arsenal of tools and techniques. Think of it as choosing the right weapon for the right monster – a slingshot won’t cut it against a dragon, and a flamethrower might be overkill for a pesky goblin. Let’s explore some of the most effective tools in your risk management arsenal.
SWOT Analysis
SWOT analysis, a classic of strategic planning, provides a structured framework for identifying and analyzing Strengths, Weaknesses, Opportunities, and Threats. By systematically examining these four elements, organizations can gain a clearer understanding of their internal capabilities and external environment, allowing for more informed risk assessments and the development of targeted mitigation strategies. For example, a small bakery might find that its strength lies in its delicious pastries (Strength), but its weakness is limited marketing reach (Weakness). An opportunity might be expanding into online sales (Opportunity), while a threat could be the rising cost of ingredients (Threat). This comprehensive overview enables the bakery to make strategic decisions about how to leverage strengths, address weaknesses, capitalize on opportunities, and mitigate threats.
Failure Mode and Effects Analysis (FMEA)
FMEA is a proactive approach to risk management that systematically identifies potential failure modes in a system or process, analyzes their effects, and determines the severity, occurrence, and detectability of each failure. This method helps prioritize risk mitigation efforts by focusing on the most critical failure modes. Imagine a car manufacturer using FMEA to analyze the braking system. By identifying potential failures (e.g., brake line rupture), assessing their severity (e.g., catastrophic accident), occurrence (e.g., low probability), and detectability (e.g., difficult to detect), they can prioritize improvements to the braking system design or manufacturing process to minimize the risk of failure. The result? Happier drivers and fewer lawsuits.
Monte Carlo Simulation, Risk Management Strategies Guide
For those who enjoy a bit of controlled chaos, Monte Carlo simulation is a powerful tool. It uses random sampling to model the probability of different outcomes in a process that involves uncertainty. By running thousands of simulations, organizations can get a clearer picture of the potential range of outcomes and their associated probabilities. For example, a construction company might use Monte Carlo simulation to model the cost and duration of a project, considering the uncertainties associated with material costs, labor availability, and weather conditions. The simulation could reveal that there’s a 15% chance the project will exceed the budget by 10%, prompting the company to take proactive measures to mitigate this risk.
Comparison of Risk Management Tools and Techniques
Choosing the right tool depends heavily on the context. Here’s a handy comparison table:
| Tool/Technique | Key Features | Applications | Advantages | Disadvantages |
|---|---|---|---|---|
| SWOT Analysis | Identifies Strengths, Weaknesses, Opportunities, and Threats | Strategic planning, risk assessment | Simple, widely applicable, provides a holistic view | Can be subjective, lacks quantitative analysis |
| FMEA | Identifies potential failure modes, analyzes effects, prioritizes risks | Product design, process improvement, safety analysis | Proactive, systematic, identifies critical failure modes | Can be time-consuming, requires expertise |
| Monte Carlo Simulation | Uses random sampling to model uncertain outcomes | Project management, financial modeling, risk assessment | Provides a range of potential outcomes, incorporates uncertainty | Requires statistical expertise, can be computationally intensive |
Last Word: Risk Management Strategies Guide
So, there you have it – a whirlwind tour through the exciting world of risk management! While the prospect of managing risk might initially seem daunting, this guide has hopefully demonstrated that it’s far from a terrifying ordeal. With the right tools and strategies, risk management becomes a proactive and even enjoyable process. Remember, embracing uncertainty is not about recklessness; it’s about strategic preparedness. Armed with this knowledge, you’re now ready to face whatever challenges life throws your way, with a confident smile and a well-crafted risk management plan in hand. Go forth and conquer (the risks, that is!).
FAQ Section
What’s the difference between risk avoidance and risk mitigation?
Avoidance means steering clear of the risk altogether. Mitigation means reducing the likelihood or impact of the risk. Think of it like this: avoidance is saying “no” to a risky bungee jump, while mitigation is wearing a safety harness on a slightly less terrifying jump.
How often should I review my risk management plan?
Regularly! The frequency depends on your industry and the nature of your risks. At a minimum, annual reviews are recommended, but more frequent checks might be necessary in dynamic environments. Think of it like your car’s oil change – neglecting it can lead to a costly breakdown.
What if my risk assessment identifies a risk I can’t control?
Even then, you’re not powerless! You can still develop contingency plans to minimize the impact should the risk materialize. It’s like preparing for a hurricane; you can’t stop it, but you can board up your windows.